Hello everyone, I have a (assumingly) simple question regarding learning static routes.
I have watched some videos on subnet masking, how its applied in binary, and read some other questions here. However, the questions are just too advanced for me. I think I need to start experimenting with even more simple setups to begin to understand. (and unfortunately I couldn't even do that -_-)
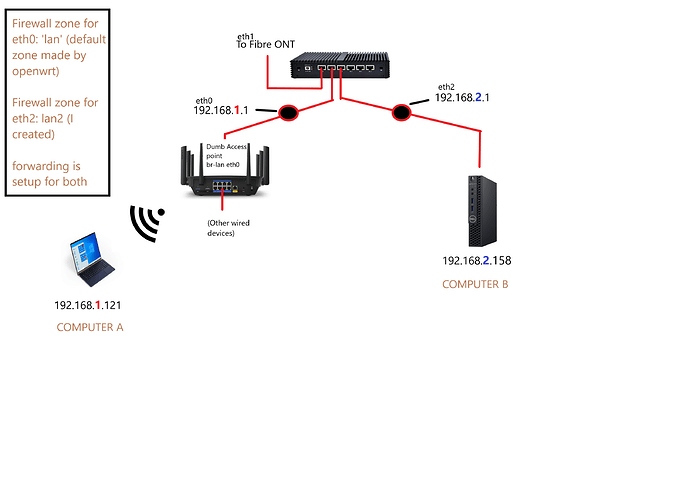
I have x86 openwrt installed on a recommended mini pc. My network is functioning, but I am trying create the below scenario to experiment with, in order to get better over the years.
What I am trying to do is create a static route so that I can ping computer A from computer B, or vice-versa (they are on different subnets).
I uploaded a picture of my setup. I added the routes to openwrt. What I made sure to do from reading the other questions is to:
-
in addition to creating another interface, I made another firewall zone with forwarding enabled (I edited eth0 to forward back and forth with eth2, and edited eth2 to forward back and forth with eth0)
-
I tried to research about adding routes to both computers. The are running windows 10, and apparently are automatically supposed to defer to the default gateway if there is no route? so it makes me think I am doing something wrong.
So I believe I took care everything, but I still failed. When trying to ping from either computer A or B, its just says 'request timed out'
It's much appreciated if anyone reads all this and can help me. I know my measly 3 days of research doesn't compare to everyone on here, but I do really want to get better at this.
Also, I think from the other topics I should upload the firewall configuration and the network configuration, so I'll do that.
**NETWORK CONFIG**
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd41:29cc:46c6::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option ifname 'eth0'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config interface 'LAN2'
option ifname 'eth2'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
config route
option target '192.168.1.0'
option gateway '192.168.1.1'
option netmask '255.255.255.0'
option interface 'lan'
config route
option target '192.168.2.0'
option gateway '192.168.2.1'
option netmask '255.255.255.0'
option interface 'LAN2'
**FIREWALL CONFIG**
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config zone
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option name 'lan2'
option network 'LAN2'
config forwarding
option dest 'wan'
option src 'lan2'
config forwarding
option dest 'lan'
option src 'lan2'
config forwarding
option src 'lan'
option dest 'lan2'