im using windows 10 home but on my next pc i will install professional so thanks for the tip
I think you can use the following in powershell under windows10/11:
New-NetQosPolicy -Name "putty" -AppPathNameMatchCondition "putty.exe" -PolicyStore ActiveStore -NetworkProfile All -DSCPAction 46
Get-NetQosPolicy -Store ActiveStore
Name : putty_ps
Owner : PowerShell / WMI
NetworkProfile : All
Precedence : 127
AppPathName : putty.exe
JobObject :
DSCPValue : 46
Remove-NetQosPolicy -Name "putty_ps" -PolicyStore ActiveStore
Seems to work, and I confirmed via tcpdump that putty's ssh packet originating from the windows VM host actually used DSCP 46 (aka EF). I note that powershell needs to be run as administrator, and the policies do not end up visible in Local Group Policy Editor. "-PolicyStore ActiveStore" will not survive a reboot, but for novice users that might be nice so a reboot cleans the slate in good windows tradition. I assume that after initial testing one could omit the "-PolicyStore ActiveStore" directive and store tested configs more permanently.
so its not necessary to tick this pox ?:
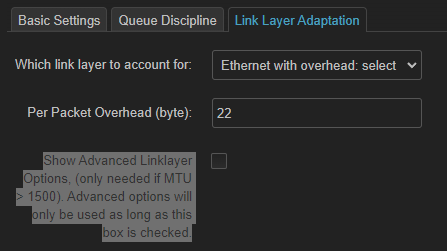
If you use the option string to pass mpu 64 to cake you do not check this. However for fq_codel ypu need that checkbox and the mpu setting there.
@Dopam-IT_1987 how do you see the call of duty ports ? my game (cod warzone) always crashes because of wireshark but csgo and wireshark is working perfectly.
with a device sniffer i use
hewlett packard the model
i'm use script modified by me
like the screen

can u tell me the port range that warzone uses ? i have read in the netduma forum udp 30000-45000 and udp3074
Yep, like moeller0 said, you can do it this way, or by including "mpu 64" in the advanced options strings for ingress and egress. I would point out dont do it in both spots, you will end up setting it to 128! (64+64) At least it used to do this years ago, as I found out to my embarrassment.
always crashes because of wireshark but csgo and wireshark is working perfectly.
You could run tcpdump on the router's br-lan interface to see internal IP addresses and ports, no need to use wireshark on the gaming computer to capture the packets.
You can even direct tcpdump to write to file, and the use wireshark to load that file so you can use wireshark's convenient GUI and tooling.
I would point out dont do it in both spots, you will end up setting it to 128! (64+64) At least it used to do this years ago, as I found out to my embarrassment.
I have not tried that myself, for the overhead keywords that behavior is intended, so that one can request accounting for vlan tags in addition to any other encapsulations, not sure why the same also applies to mpu, but I guess there is no good reason to request the same mpu twice....
so what exatly do i have to do to see the game ports and dscps of my gaming pc and the game server.
install tcpdump on my router via luci ? and what command do i have to run next ?
Yes you need only this port for call of duty
Exemple 41000--3074 - cs4
E.g.:
tcpdump -i br-lan -vv -n 'host 192.168.42.201'
shows packets to/from the internal host with the IPv4 address of 192.168.42.201 (replace with your gaming computers IPv4 address):
root@turris:/srv/persistent/captures# tcpdump -i br-lan -vv -n 'host 192.168.42.201'
tcpdump: listening on br-lan, link-type EN10MB (Ethernet), capture size 262144 bytes
16:22:37.590465 IP (tos 0x2,ECT(0), ttl 116, id 31550, offset 0, flags [DF], proto TCP (6), length 115)
155.133.226.75.27031 > 192.168.42.201.55909: Flags [P.], cksum 0xed4e (correct), seq 3993736584:3993736659, ack 2148036925, win 1026, length 75
16:22:37.590755 IP (tos 0x0, ttl 64, id 16092, offset 0, flags [DF], proto TCP (6), length 40)
192.168.42.201.55909 > 155.133.226.75.27031: Flags [.], cksum 0x0edc (correct), seq 1, ack 75, win 32403, length 0
16:22:39.267686 IP (tos 0x2,ECT(0), ttl 64, id 38328, offset 0, flags [none], proto UDP (17), length 106)
192.168.42.201.61002 > 192.168.42.1.64932: [udp sum ok] UDP, length 78
16:22:39.268838 IP (tos 0x2,ECT(0), ttl 63, id 63555, offset 0, flags [none], proto UDP (17), length 98)
192.168.42.1.64932 > 192.168.42.201.61002: [udp sum ok] UDP, length 70
16:22:42.267674 IP (tos 0x2,ECT(0), ttl 64, id 38690, offset 0, flags [none], proto UDP (17), length 109)
192.168.42.201.61002 > 192.168.42.1.64932: [udp sum ok] UDP, length 81
16:22:42.268977 IP (tos 0x2,ECT(0), ttl 63, id 8611, offset 0, flags [none], proto UDP (17), length 101)
192.168.42.1.64932 > 192.168.42.201.61002: [udp sum ok] UDP, length 73
16:22:45.269740 IP (tos 0x2,ECT(0), ttl 64, id 39067, offset 0, flags [none], proto UDP (17), length 107)
192.168.42.201.61002 > 192.168.42.1.64932: [udp sum ok] UDP, length 79
16:22:45.270530 IP (tos 0x2,ECT(0), ttl 63, id 53006, offset 0, flags [none], proto UDP (17), length 95)
192.168.42.1.64932 > 192.168.42.201.61002: [udp sum ok] UDP, length 67
16:22:47.331852 ARP, Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.42.201 tell 192.168.42.1, length 28
16:22:47.332097 ARP, Ethernet (len 6), IPv4 (len 4), Reply 192.168.42.201 is-at 34:64:a9:9a:2f:30, length 46
16:22:48.271130 IP (tos 0x2,ECT(0), ttl 63, id 18476, offset 0, flags [none], proto UDP (17), length 110)
192.168.42.1.64932 > 192.168.42.201.61002: [udp sum ok] UDP, length 82
16:22:48.271469 IP (tos 0x2,ECT(0), ttl 64, id 39590, offset 0, flags [none], proto UDP (17), length 102)
192.168.42.201.61002 > 192.168.42.1.64932: [udp sum ok] UDP, length 74
16:22:51.271735 IP (tos 0x2,ECT(0), ttl 64, id 39914, offset 0, flags [none], proto UDP (17), length 102)
192.168.42.201.61002 > 192.168.42.1.64932: [udp sum ok] UDP, length 74
16:22:51.272969 IP (tos 0x2,ECT(0), ttl 63, id 3739, offset 0, flags [none], proto UDP (17), length 99)
192.168.42.1.64932 > 192.168.42.201.61002: [udp sum ok] UDP, length 71
^C
14 packets captured
14 packets received by filter
0 packets dropped by kernel
for example lets look at:
16:22:51.272969 IP (tos 0x2,ECT(0), ttl 63, id 3739, offset 0, flags [none], proto UDP (17), length 99)
192.168.42.1.64932 > 192.168.42.201.61002: [udp sum ok] UDP, length 71
this means an UDP packet from 192.168.42.1 (my router) from port 64932 was sent to 192.168.42.201 (my "gaming computer") to port 61002 with tos byte value 0x2 which according to this table means CS1.
If you want to store this to a capture file on the router just add -w my_capture_file_name.cap to the tcpdump invocation, but be aware that capture files can grow quickly and drive your router into out of memory errors, so only do this for a short while (so the file stays small) and/or write to a mounted storage device on the router.
so it only captures tcp put my games use only udp
What output do you see? Do not be confused by the tcp in the tcpdump name ![]()
In my example the proto UDP indicates that it captured UDP packets....
15:14:27.013320 IP (tos 0x48, ttl 64, id 7467, offset 0, flags [DF], proto TCP (6), length 324)
192.168.1.1.22 > 192.168.1.184.49443: Flags [P.], cksum 0x8540 (incorrect -> 0xc4f2), seq 1762412736:1762413020, ack 210585, win 534, length 284
15:14:27.013547 IP (tos 0x48, ttl 64, id 7468, offset 0, flags [DF], proto TCP (6), length 488)
192.168.1.1.22 > 192.168.1.184.49443: Flags [P.], cksum 0x85e4 (incorrect -> 0x38db), seq 1762413020:1762413468, ack 210585, win 534, length 448
15:14:27.013766 IP (tos 0x0, ttl 128, id 44862, offset 0, flags [DF], proto TCP (6), length 40)
192.168.1.184.49443 > 192.168.1.1.22: Flags [.], cksum 0x2189 (correct), seq 210585, ack 1762412736, win 8209, length 0
15:14:27.013766 IP (tos 0x0, ttl 128, id 44863, offset 0, flags [DF], proto TCP (6), length 40)
192.168.1.184.49443 > 192.168.1.1.22: Flags [.], cksum 0x1eaf (correct), seq 210585, ack 1762413468, win 8207, length 0
15:14:27.014016 IP (tos 0x48, ttl 64, id 7470, offset 0, flags [DF], proto TCP (6), length 324)
192.168.1.1.22 > 192.168.1.184.49443: Flags [P.], cksum 0x8540 (incorrect -> 0x5d1f), seq 1762414048:1762414332, ack 210585, win 534, length 284
15:14:27.014235 IP (tos 0x48, ttl 64, id 7471, offset 0, flags [DF], proto TCP (6), length 456)
192.168.1.1.22 > 192.168.1.184.49443: Flags [P.], cksum 0x85c4 (incorrect -> 0x06d2), seq 1762414332:1762414748, ack 210585, win 534, length 416
its only tcp
The easiest way to use tcpdump with wireshark (besides using ntopng) is
- Open a ssh session
- tcpdump -i br-lan -w /tmp/capturefile.pcap ##creates a capture file in your /tmp folder named capturefile.pcap
- Play the game ##if you think you captured enough ->
- Go back to the ssh session an hit CTRL + C ##to stop the capture
- Open Winscp an copy the capturefile.pcap from /tmp to your pc
- Open it with wireshark
i got what i want with
root@OpenWrt:~# tcpdump -i br-lan -v -n 'udp and host 192.168.1.184'
16:29:54.737340 IP (tos 0xb8, ttl 51, id 56582, offset 0, flags [DF], proto UDP (17), length 580)
51.195.60.27.27021 > 192.168.1.184.27005: UDP, length 552
16:29:54.738849 IP (tos 0x0, ttl 128, id 24707, offset 0, flags [none], proto UDP (17), length 164)
192.168.1.184.27005 > 51.195.60.27.27021: UDP, length 136
it looks like the dscp prio with qosify from the server is working with 0xb8 = EF (from the website you linked, but what means tos delay flag and tos throughput flag on the website, would it be better to not have that with CS5 or CS6), but my pc to the server is still 0x0=none
but my pc to the server is still 0x0=none
You’re capturing upload traffic before it gets processed by qosify.