hey @moeller0 is this post from you still relevant ?
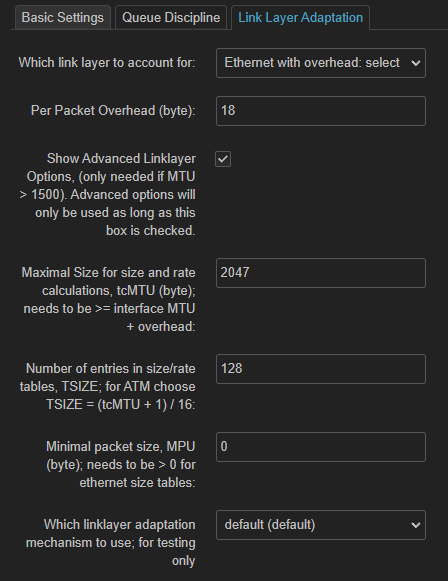
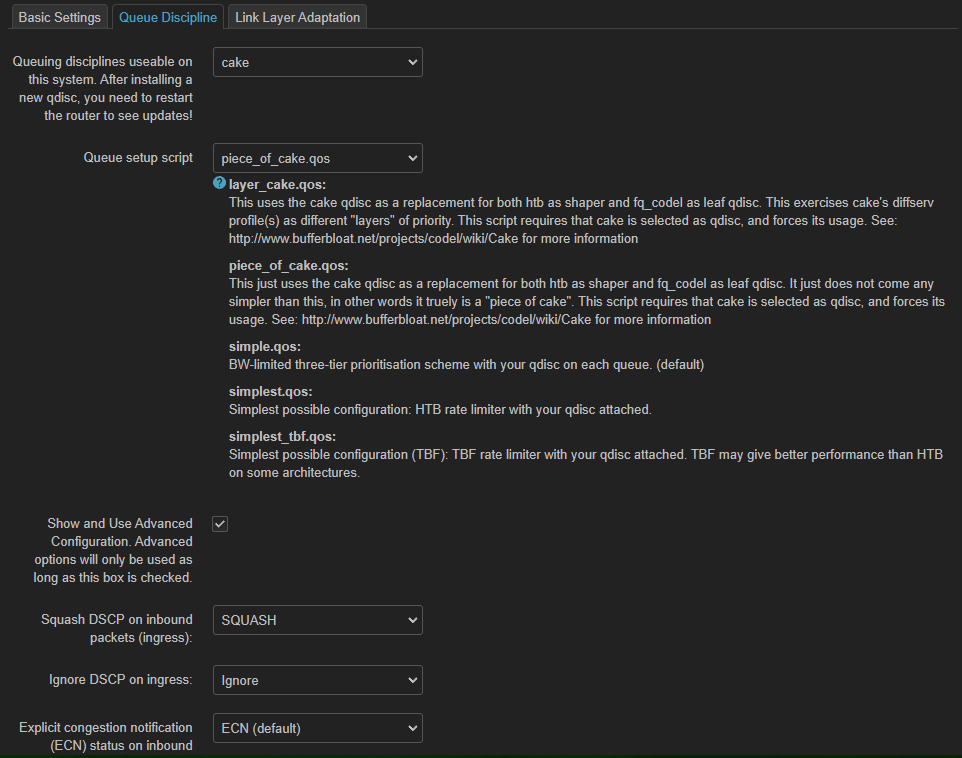
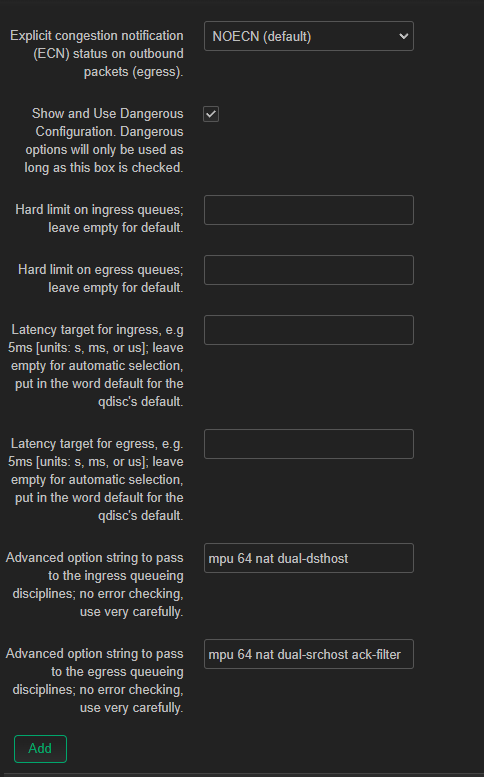
why should someone do point 4. - 6.1 when it says :
Show Advanced Linklayer Options, (only needed if MTU > 1500)
what will these commands do then ?
did i set up everything correct for low latency gaming ?
root@OpenWrt:~# tc -s qdisc
qdisc noqueue 0: dev lo root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc cake 8039: dev eth0 root refcnt 9 bandwidth 42Mbit besteffort dual-srchost nat nowash ack-filter split-gso rtt 100ms noatm overhead 18 mpu 64
Sent 557716 bytes 2136 pkt (dropped 1, overlimits 503 requeues 0)
backlog 0b 0p requeues 0
memory used: 99668b of 4Mb
capacity estimate: 42Mbit
min/max network layer size: 28 / 1500
min/max overhead-adjusted size: 64 / 1518
average network hdr offset: 14
Tin 0
thresh 42Mbit
target 5ms
interval 100ms
pk_delay 248us
av_delay 22us
sp_delay 8us
backlog 0b
pkts 2137
bytes 559230
way_inds 0
way_miss 218
way_cols 0
drops 1
marks 0
ack_drop 0
sp_flows 1
bk_flows 1
un_flows 0
max_len 17301
quantum 1281
qdisc ingress ffff: dev eth0 parent ffff:fff1 ----------------
Sent 5015802 bytes 55734 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc fq_codel 0: dev eth1 root refcnt 2 limit 10240p flows 1024 quantum 1514 target 5ms interval 100ms memory_limit 4Mb ecn drop_batch 64
Sent 9269453949 bytes 6920256 pkt (dropped 5753, overlimits 0 requeues 89363)
backlog 0b 0p requeues 89363
maxpacket 1514 drop_overlimit 4864 new_flow_count 17581 ecn_mark 0 drop_overmemory 4864
new_flows_len 0 old_flows_len 0
qdisc noqueue 0: dev br-lan root refcnt 2
Sent 0 bytes 0 pkt (dropped 0, overlimits 0 requeues 0)
backlog 0b 0p requeues 0
qdisc cake 803a: dev ifb4eth0 root refcnt 2 bandwidth 850Mbit besteffort dual-dsthost nat wash no-ack-filter split-gso rtt 100ms noatm overhead 18 mpu 64
Sent 5809566 bytes 55734 pkt (dropped 0, overlimits 679 requeues 0)
backlog 0b 0p requeues 0
memory used: 32358b of 15140Kb
capacity estimate: 850Mbit
min/max network layer size: 46 / 1500
min/max overhead-adjusted size: 64 / 1518
average network hdr offset: 14
Tin 0
thresh 850Mbit
target 5ms
interval 100ms
pk_delay 14us
av_delay 7us
sp_delay 1us
backlog 0b
pkts 55734
bytes 5809566
way_inds 2
way_miss 218
way_cols 0
drops 0
marks 0
ack_drop 0
sp_flows 0
bk_flows 1
un_flows 0
max_len 21852
quantum 1514