Hi all,
A couple of years ago (time really flies!) I tried to set up my first VLAN after migrating to OpenWRT, with the main motivation being the control it gave me over my network and ability to create real VLAN's for security. The problem is, I could not wrap my head around the whole concept of VLAN's as I have no experience in networking. It was recommended that I wait for DSA to release before trying. It was still quite overwhelming, and I put it off a long time, however, after many hours, I think I have started to come to something resembling a rudimentary VLAN. Still, I have run into a few issues, would you be able to provide some advice/guidance?
My hardware
OpenWRT Router (Linksys EA8300) in the hallway with 5 ports, lan1 through lan4, with the 5th port being for wan.
A basic Netgear managed switch (Netgear GS305E) with 5 more ports, installed in my bedroom with a server and desktop connected to it via Ethernet.
I am running OpenWRT 24.10.2 and using DSA. My interface and device setup looks something like this:
Interfaces
-
Guest = br-lan.20
-
Home = br-lan.10
-
Lan = br-lan.99
-
Wan = wan
-
Wan6 = br-wan6
Devices
-
Br-lan (bridge device for my VLAN)
-
Br-lan.10
-
Br-lan.20
-
Br-lan.99
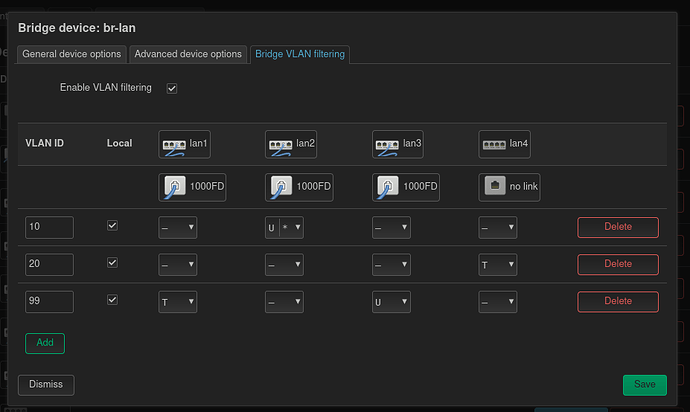
VLAN Filtering
Bridge device: br-lan
Bridge ports: lan1, lan2, lan3, lan4
Here is my config, my idea was for lan1 to be used for VLAN 99 with no wireless connectivity and lan2 to be used for my home network with wireless attached, it has been left untagged as my partner needs to use an Ethernet cable on occasion. Lan3 is for a backup server that is next to my router and lan4 is to be used for my Guest network, with no Ethernet cable but a wireless interface.
Like so
Here is my VLAN config
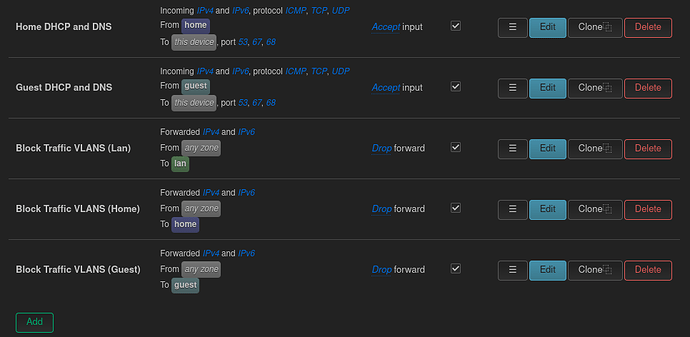
I have then created these firewall rules to stop traffic moving between VLAN's (apart from DCHP/DNS) as I will use Tailscale for any inter-network transfers:
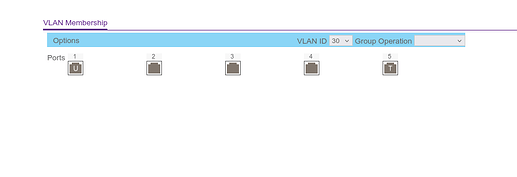
Netgear VLAN integration
My main issue, apart from not being sure if this is actually a secure VLAN setup is that I am not able to get OpenWRT to work with my switch like this. I have to leave VLAN 99 as untagged otherwise I cannot reach my devices on the switch.
My plan was to create two 802.1q VLAN's, VLAN 30 and VLAN 40. The idea being to further segment my OpenWRT VLAN 99 into two further separate vlans, one for my desktop PC and another for my server.
For VLAN 30, I selected Port 1 as (untagged), ports 2 (not a member), 3 (not a member) and 4 (not a member) and port 5 as tagged as this is what goes upstream to my VLAN 99 on OpenWRT.
For VLAN 40, Port 1 (not a member), Port 2 (untagged), 3 (not a member), 4 (not a member) and Port 5 as tagged.
Then reflected this in the default VLAN group
Unfortunately, every time I try this, I end up locked out of my switch (unable to access any of it's ports) and have to do a factory reset. Am I correct in thinking that if my Switch is VLAN aware and set to Tagged on Port 5 and my VLAN 99 in OpenWRT is also set to Tagged, then traffic should be able to flow between the two?
Does my overall setup make sense, in terms of functionality and security, or have I misunderstood how VLAN's should work? What am I doing wrong?