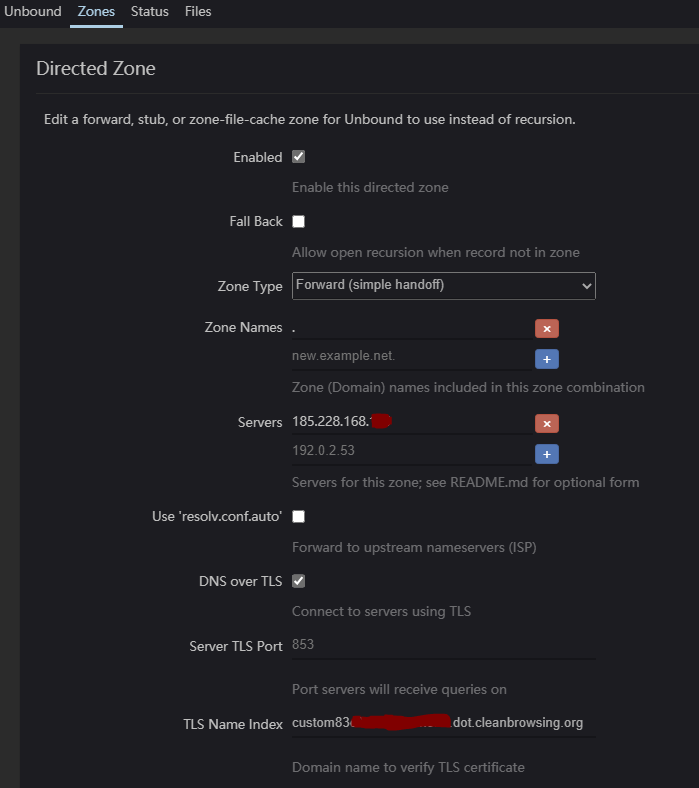
I don't get any errors when I use their FREE Adult TLS DNS. My issue is when I'm trying to use the paid TLS DNS servers they have configured for my account specifically.
date
Fri Jan 24 15:09:01 EST 2020
output of: openssl s_client -CApath /var/lib/unbound -connect adult-filter-dns.cleanbrowsing.org:853 -status
openssl s_client -CApath /var/lib/unbound -connect adult-filter-dns.cleanbrowsing.org:853 -status
CONNECTED(00000003)
depth=3 C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
verify error:num=19:self signed certificate in certificate chain
verify return:1
depth=3 C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
verify return:1
depth=2 C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", CN = Go Daddy Root Certificate Authority - G2
verify return:1
depth=1 C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
verify return:1
depth=0 OU = Domain Control Validated, CN = *.cleanbrowsing.org
verify return:1
OCSP response: no response sent
---
Certificate chain
0 s:OU = Domain Control Validated, CN = *.cleanbrowsing.org
i:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
1 s:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
i:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", CN = Go Daddy Root Certificate Authority - G2
2 s:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", CN = Go Daddy Root Certificate Authority - G2
i:C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
3 s:C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
i:C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIGwzCCBaugAwIBAgIJAKeWQyCeW3i4MA0GCSqGSIb3DQEBCwUAMIG0MQswCQYD
VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEa
MBgGA1UEChMRR29EYWRkeS5jb20sIEluYy4xLTArBgNVBAsTJGh0dHA6Ly9jZXJ0
cy5nb2RhZGR5LmNvbS9yZXBvc2l0b3J5LzEzMDEGA1UEAxMqR28gRGFkZHkgU2Vj
dXJlIENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTE4MDgxMDIxMzQwN1oX
DTIwMDgxMDIxMzQwN1owQTEhMB8GA1UECxMYRG9tYWluIENvbnRyb2wgVmFsaWRh
dGVkMRwwGgYDVQQDDBMqLmNsZWFuYnJvd3Npbmcub3JnMIIBIjANBgkqhkiG9w0B
AQEFAAOCAQ8AMIIBCgKCAQEApM72exOeLQcq9x5y4HIdRGLnv5ffykkVIrqqGXyv
zLdxY6oSR3EZ8UviWJFx6f7XSbJz8/t0ESVgsIKAqPFUXXlZ9JJRO1AU+TeMbMbv
LEAIzZ3xJ+O4xYPMmENfsYjd9UzQJ0QwwNn4Ae3WPKN1trG6SMsq/muPrpE7YrXy
Kc+b6+YMl4VXIi078CnZ3fUSOqdTUc/qdrMHKjWtrBf62obmQBF/8xpnvdOYeIa+
tC/dhhaYBmEXpg7RbOj4u5if3naKgchXz1PKsm5jCrgElRFAJowlUVdSSmjNnyAI
vhIMFGYOEiVCU6bLO0Mf+90kpPaxh7S9Wa/jYNrftBRoNwIDAQABo4IDSDCCA0Qw
DAYDVR0TAQH/BAIwADAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDgYD
VR0PAQH/BAQDAgWgMDcGA1UdHwQwMC4wLKAqoCiGJmh0dHA6Ly9jcmwuZ29kYWRk
eS5jb20vZ2RpZzJzMS04NTYuY3JsMF0GA1UdIARWMFQwSAYLYIZIAYb9bQEHFwEw
OTA3BggrBgEFBQcCARYraHR0cDovL2NlcnRpZmljYXRlcy5nb2RhZGR5LmNvbS9y
ZXBvc2l0b3J5LzAIBgZngQwBAgEwdgYIKwYBBQUHAQEEajBoMCQGCCsGAQUFBzAB
hhhodHRwOi8vb2NzcC5nb2RhZGR5LmNvbS8wQAYIKwYBBQUHMAKGNGh0dHA6Ly9j
ZXJ0aWZpY2F0ZXMuZ29kYWRkeS5jb20vcmVwb3NpdG9yeS9nZGlnMi5jcnQwHwYD
VR0jBBgwFoAUQMK9J47MNIMwojPX+2yz8LQsgM4wMQYDVR0RBCowKIITKi5jbGVh
bmJyb3dzaW5nLm9yZ4IRY2xlYW5icm93c2luZy5vcmcwHQYDVR0OBBYEFBDfeB2j
KdPI8Kaabg7ow84BxvoMMIIBgAYKKwYBBAHWeQIEAgSCAXAEggFsAWoAdwCkuQmQ
tBhYFIe7E6LMZ3AKPDWYBPkb37jjd80OyA3cEAAAAWUlw3Z+AAAEAwBIMEYCIQCD
eR6AXI1YRvTiwgkEz2BTU5tPNgqmYN93JXhsD1YnnwIhALg0i9ZlBEkDciwDf2lG
cRr1HFSjIiPiIgFWIxgCT+PLAHYA7ku9t3XOYLrhQmkfq+GeZqMPfl+wctiDAMR7
iXqo/csAAAFlJcN7mgAABAMARzBFAiB04b8jtxECVdc7IBlaWDF5AdeOhA56dL9n
vIq77diiNAIhAKFDoPNqhyKCPH0JH0t0xRr+nJICWSC80Nw1B/UQfh9qAHcAXqdz
+d9WwOe1Nkh90EngMnqRmgyEoRIShBh1loFxRVgAAAFlJcN8WwAABAMASDBGAiEA
v241P0JJkXB+Re4s9w94Qz6RV10kh0FkSisfHVANGjUCIQCdJonDNlvXHIZ4EqyR
zcMYfSGEI1P8g17NesChd0tF1TANBgkqhkiG9w0BAQsFAAOCAQEAs2AFNDG3I7Rv
p09ELIXL4xC5XeGdkDAQOdLxG9um3z8wmdtU3vrPbs4FugJelQgC6XCFh36ug5cP
BUqtvuKdP+S6Hs5DAqGk0xiscSMbei45cTA+1oWnZarefkxml6B7bBw/KpaBb5s9
RlAcA19SOfhWtcoLi8VY1r8pF0ozCgLTkSr16iFLItcYwPDrtmcMGh2tIyUxwspR
BToVtLJQfBHvaqlwJ5nblQn29+lbfAIzKoyJ+3QrOUoaMKQchSmJ3zBJrr8k6ETO
peW3JlruHPLnpCIRKctzV63GjAkGAxsViiA36Fa4ZVM5mExvyq3bnUdkoVA12v5c
oFxjsQxy8A==
-----END CERTIFICATE-----
subject=OU = Domain Control Validated, CN = *.cleanbrowsing.org
issuer=C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 6135 bytes and written 463 bytes
Verification error: self signed certificate in certificate chain
---
New, TLSv1.2, Cipher is ECDHE-RSA-CHACHA20-POLY1305
Server public key is 2048 bit
Secure Renegotiation IS supported
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-CHACHA20-POLY1305
Session-ID: A250C57838A0F287112221FA3DCA539CF54840EC617FA80223547BD10B33D352
Session-ID-ctx:
Master-Key: 2E058B69ECBA4FDB9816623ADE500C76C19519B0C1FBCF75A506059A6C16B90EA75D200DDED48E03F46F728A8249E517
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 3600 (seconds)
TLS session ticket:
0000 - a9 a2 86 87 6c d9 29 85-95 60 02 cf 8f cf 3a 08 ....l.)..`....:.
0010 - 52 4e 2b 5e e2 fe eb ca-6c 91 e0 16 cf e6 0b 73 RN+^....l......s
0020 - 01 90 70 83 ad 59 ff 4e-3a 3c d8 fa 70 1b 52 2b ..p..Y.N:<..p.R+
0030 - cf 67 4b 6a fb 68 41 67-2e f8 82 e8 8b fd 42 ff .gKj.hAg......B.
0040 - 45 15 03 fa 44 3f 79 fe-cb 9c b2 03 ea 3e 6e 94 E...D?y......>n.
0050 - 91 cb de e8 e9 fe 0b 8f-21 fe 36 2e e2 70 f1 9a ........!.6..p..
0060 - d7 97 30 ef ae 4a 1d a0-1d 47 0b c3 33 6f 41 25 ..0..J...G..3oA%
0070 - 30 fd c4 07 53 ec 68 be-a8 0a 48 e9 50 14 b9 06 0...S.h...H.P...
0080 - 2d d9 96 c1 88 48 79 c7-40 77 78 12 6f 97 04 d6 -....Hy.@wx.o...
0090 - f2 a2 0d a2 4d 81 47 1d-0a 43 cb 84 2c 79 ed bf ....M.G..C..,y..
00a0 - 82 c8 4a b0 d2 04 1b d2-45 ee 3f aa 7e b0 77 82 ..J.....E.?.~.w.
00b0 - f6 ff 26 14 60 36 f7 76-49 28 3e a6 2b 53 54 63 ..&.`6.vI(>.+STc
00c0 - b9 92 d1 f7 5e a9 d5 9a-aa b5 70 a2 2c bd c2 7d ....^.....p.,..}
00d0 - 9e 48 8c ad 11 ef 81 2f-a1 d6 90 20 93 c8 57 4b .H...../... ..WK
00e0 - e0 5b cd e8 56 a8 fd 20-57 ca 48 1c a3 a4 e9 ca .[..V.. W.H.....
00f0 - ee 31 e1 c7 b8 f7 1e 08-98 eb cb a7 bd 56 a3 a1 .1...........V..
0100 - ea b5 96 78 05 c9 2d c1-fa 40 d1 b6 62 3e 9b 2a ...x..-..@..b>.*
0110 - 2b 31 ff 94 5e 08 4f 21-e0 9e 30 4e b3 69 80 ac +1..^.O!..0N.i..
0120 - 5d cd a7 60 a0 4c 59 e0-c6 32 e6 50 eb a0 a9 e3 ]..`.LY..2.P....
0130 - 65 f8 30 21 dd 7b 12 fb-b1 0d 79 2e 8e 72 6b fd e.0!.{....y..rk.
0140 - b7 ff e0 20 48 ca cd a1-33 1c 10 8d ee 9c 32 a5 ... H...3.....2.
0150 - f5 41 70 42 2a 1f fb dd-94 c3 44 b4 bf 7d 1f 0c .ApB*.....D..}..
0160 - b4 ed 61 44 c3 d3 bf 67-e6 51 16 f1 be 8b 15 e8 ..aD...g.Q......
0170 - 7e 7c 36 c1 84 9d 31 1d-21 b2 fe cb 72 2a 8b 51 ~|6...1.!...r*.Q
0180 - 76 46 34 28 e7 89 03 bb-43 37 54 e9 62 7d 2e fd vF4(....C7T.b}..
0190 - fe 5a c9 48 fa 44 dc fe-64 f8 2d 12 81 92 a6 69 .Z.H.D..d.-....i
01a0 - 80 51 fc 1f b4 07 ee 92-f4 fa e2 bb 54 d4 cc cf .Q..........T...
01b0 - 03 a2 bd 30 3a 18 68 da-2a 9f c9 e4 a3 53 00 45 ...0:.h.*....S.E
01c0 - 56 d8 7f e1 bf 66 V....f
Start Time: 1579896402
Timeout : 7200 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
Extended master secret: yes
---
closed
output using the TLS domain for my paid service:
openssl s_client -CApath /var/lib/unbound -connect customXXXXXXXXXXXXXX.dot.cleanbrowsing.org:853 -status
CONNECTED(00000003)
depth=3 C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
verify error:num=19:self signed certificate in certificate chain
verify return:1
depth=3 C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
verify return:1
depth=2 C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", CN = Go Daddy Root Certificate Authority - G2
verify return:1
depth=1 C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
verify return:1
depth=0 OU = Domain Control Validated, CN = *.dot.cleanbrowsing.org
verify return:1
OCSP response: no response sent
---
Certificate chain
0 s:OU = Domain Control Validated, CN = *.dot.cleanbrowsing.org
i:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
1 s:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
i:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", CN = Go Daddy Root Certificate Authority - G2
2 s:C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", CN = Go Daddy Root Certificate Authority - G2
i:C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
3 s:C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
i:C = US, O = "The Go Daddy Group, Inc.", OU = Go Daddy Class 2 Certification Authority
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIGyzCCBbOgAwIBAgIIOLa4mD+XluowDQYJKoZIhvcNAQELBQAwgbQxCzAJBgNV
BAYTAlVTMRAwDgYDVQQIEwdBcml6b25hMRMwEQYDVQQHEwpTY290dHNkYWxlMRow
GAYDVQQKExFHb0RhZGR5LmNvbSwgSW5jLjEtMCsGA1UECxMkaHR0cDovL2NlcnRz
LmdvZGFkZHkuY29tL3JlcG9zaXRvcnkvMTMwMQYDVQQDEypHbyBEYWRkeSBTZWN1
cmUgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IC0gRzIwHhcNMjAwMTE1MDAwNDE0WhcN
MjIwMTE1MDAwNDE0WjBFMSEwHwYDVQQLExhEb21haW4gQ29udHJvbCBWYWxpZGF0
ZWQxIDAeBgNVBAMMFyouZG90LmNsZWFuYnJvd3Npbmcub3JnMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEAsSVW1l+dfNPFWeqsB1hPcLCaMMhFEbeo7opX
GcOKWY4tCFGSv4P1or2vRCUn/TsnesVumf/rzZDYjuAaco7EM7qqg6N3jYI93r2j
xnzBgVMZVJshF/fDZtMSPuGqY0E/b9xnoBxqjHTygZ+2+2Qzqtfr3Qt8teuUoZOv
ucrFqKm5Vsl6dB5qsf895ZVTQ0sZQB9SS/ztaZNRC4KBNI28Zxlad+fkqbcMlz0U
oimpNC4E4opRYTCMntNt4mwGsoLytkaPFVkau2Z1/wYpRM58NPRaqna+jTGBLz87
1sM3XmiCapL48TApeUZtk0tFd2ve3gq2enIUz23bXgpYQZ+v7QIDAQABo4IDTTCC
A0kwDAYDVR0TAQH/BAIwADAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIw
DgYDVR0PAQH/BAQDAgWgMDgGA1UdHwQxMC8wLaAroCmGJ2h0dHA6Ly9jcmwuZ29k
YWRkeS5jb20vZ2RpZzJzMS0xNjQ2LmNybDBdBgNVHSAEVjBUMEgGC2CGSAGG/W0B
BxcBMDkwNwYIKwYBBQUHAgEWK2h0dHA6Ly9jZXJ0aWZpY2F0ZXMuZ29kYWRkeS5j
b20vcmVwb3NpdG9yeS8wCAYGZ4EMAQIBMHYGCCsGAQUFBwEBBGowaDAkBggrBgEF
BQcwAYYYaHR0cDovL29jc3AuZ29kYWRkeS5jb20vMEAGCCsGAQUFBzAChjRodHRw
Oi8vY2VydGlmaWNhdGVzLmdvZGFkZHkuY29tL3JlcG9zaXRvcnkvZ2RpZzIuY3J0
MB8GA1UdIwQYMBaAFEDCvSeOzDSDMKIz1/tss/C0LIDOMDkGA1UdEQQyMDCCFyou
ZG90LmNsZWFuYnJvd3Npbmcub3JnghVkb3QuY2xlYW5icm93c2luZy5vcmcwHQYD
VR0OBBYEFPZvn/v9UV4RKsbGwWyO5o/FGVuHMIIBfAYKKwYBBAHWeQIEAgSCAWwE
ggFoAWYAdQCkuQmQtBhYFIe7E6LMZ3AKPDWYBPkb37jjd80OyA3cEAAAAW+mg9iv
AAAEAwBGMEQCIEVEc6+lx3qgpIAnRb43Wpy7gWKJc/z9Mc1PBUjHzCbGAiB9SmCa
CN5L4UAemaVfUdbuE14eu9g5AsWwwXJJviVd7gB1AO5Lvbd1zmC64UJpH6vhnmaj
D35fsHLYgwDEe4l6qP3LAAABb6aD3U4AAAQDAEYwRAIgDKZnDZgyOh+NZE4t5rV2
yuYRGjYyLFpC7MzYyE7v0qcCIDjlyUPhHmVkGrZWPFf34ivJCtvb5brPRLK1bI+e
6q3cAHYAVhQGmi/XwuzT9eG9RLI+x0Z2ubyZEVzA75SYVdaJ0N0AAAFvpoPe9gAA
BAMARzBFAiEAlhpMQs9NbY2rSn7ooE0WDHS/QgjwhiE212cBs5oWtM4CIFgsO+8C
ubr05L0AI4rReHhB067tMunIpKppAcsW3ZF8MA0GCSqGSIb3DQEBCwUAA4IBAQCG
EKXT7bXtSfb8O9OWmaYFm2Lc14wMFGnv4CkrdwcT0een5ZfpY7+WdI7L4OGMVX0E
0j8BtSD8LHEq6dsgQ/zJAQZVdhUa9tEjYDjXy6zTjJKBw+xlnGHzhTQZXgQicM6t
oeWRoZnY49H5tzEEQ1bPG/qMepXkcYTTq7SuyyeHINAgpxRA+vF9XraRDsgcKI9V
fsplI52HI8pzf1FxjS6n4ozqutQXuS4HQKhs5lPIeVzt6GIQO5BerM/uC1fJm30P
wTHKVgZw8lueUKqnec6/NDcBxTRC1mfXcOP1IEl/2jqXOLZbl8S9eAYxDH9esEgo
RlaP5I0svCbqnZ7u32RI
-----END CERTIFICATE-----
subject=OU = Domain Control Validated, CN = *.dot.cleanbrowsing.org
issuer=C = US, ST = Arizona, L = Scottsdale, O = "GoDaddy.com, Inc.", OU = http://certs.godaddy.com/repository/, CN = Go Daddy Secure Certificate Authority - G2
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 6143 bytes and written 473 bytes
Verification error: self signed certificate in certificate chain
---
New, TLSv1.2, Cipher is ECDHE-RSA-CHACHA20-POLY1305
Server public key is 2048 bit
Secure Renegotiation IS supported
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-CHACHA20-POLY1305
Session-ID: CE55277BDDABE28D38742D43A3F9FA43B42B3388986D4A1FB5553CD74A0FD805
Session-ID-ctx:
Master-Key: D7BB7C2B3F3D9CF4654FA054B06EC100E9FCAAECFB86F2A687B8DDB1AF4DCE3AA72AD2D74BC09C89A4CBE7692855160A
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 3600 (seconds)
TLS session ticket:
0000 - cd 9b a9 37 3d 52 8d aa-57 35 bd 42 6b 75 08 15 ...7=R..W5.Bku..
0010 - 82 4f 2b 5e 4b 1a a4 04-65 2b 64 5f c3 f6 7e 12 .O+^K...e+d_..~.
0020 - 01 90 70 54 cf 96 7f 53-47 18 87 94 c1 80 00 1b ..pT...SG.......
0030 - fc 03 26 76 f2 8c 2b 02-aa 5f 63 96 fb 4c 49 44 ..&v..+.._c..LID
0040 - c6 41 13 47 ee 16 e6 d4-3a a6 e9 1b d1 70 a8 80 .A.G....:....p..
0050 - 4b e0 73 de 8b 25 0f a4-34 5b 34 05 66 b0 d1 15 K.s..%..4[4.f...
0060 - f9 e0 14 27 ed 3e fc 04-b4 58 65 83 d9 4c 39 6b ...'.>...Xe..L9k
0070 - c0 0b a4 7f 3e f5 ea 86-c3 8d 5f 22 a9 e5 fe b6 ....>....._"....
0080 - 48 b6 2a 16 3c cf d5 51-d7 88 1f da 64 cb ac 60 H.*.<..Q....d..`
0090 - fd d2 4e f8 c2 4a 0a 1b-42 46 11 1d 05 d9 f1 68 ..N..J..BF.....h
00a0 - 35 36 72 ce 06 d8 c3 f8-e3 f5 a3 12 77 b6 78 d5 56r.........w.x.
00b0 - 87 34 75 dd d8 cd 55 c0-0c ff 45 29 e1 1b b6 25 .4u...U...E)...%
00c0 - 38 1c 07 9e f6 43 1d ff-ed 74 7c 4f 2b 10 90 1a 8....C...t|O+...
00d0 - 44 80 ff b9 6f 66 10 2f-80 2f 03 df 1c fa 50 fd D...of././....P.
00e0 - da 5f a1 06 65 a3 05 44-70 be ab c8 4e f6 2d 47 ._..e..Dp...N.-G
00f0 - bd 97 ba 0e d3 a5 4f d3-9c d2 fb f2 47 8d f3 9a ......O.....G...
0100 - 42 c8 72 f5 c0 70 43 95-ec 1e 5d b1 ca 93 9e ae B.r..pC...].....
0110 - 20 83 a6 af 38 1a e5 43-d5 67 34 23 da 50 ce 01 ...8..C.g4#.P..
0120 - 74 59 ef 51 24 6d 93 54-b6 ce bd c7 eb 26 b2 8c tY.Q$m.T.....&..
0130 - 71 dc 16 75 b4 92 be 73-10 35 62 a9 a7 f4 f5 1f q..u...s.5b.....
0140 - 47 8a 56 eb a4 ed 66 07-4b a5 99 04 d3 08 a8 83 G.V...f.K.......
0150 - f0 92 3c 89 63 0b 45 3a-4a 95 44 43 c3 48 5d a6 ..<.c.E:J.DC.H].
0160 - 82 12 51 7a 3d 8c 47 8c-63 c4 05 65 8c a8 50 92 ..Qz=.G.c..e..P.
0170 - 9f 6d e5 4e 0e c8 b2 86-c3 26 d1 61 0d 4b 3a 54 .m.N.....&.a.K:T
0180 - 8f 99 af a3 d3 f4 a3 d1-eb 65 be eb 47 be f6 f8 .........e..G...
0190 - cb 4f d4 b6 67 cd 10 ea-69 23 c6 96 e0 18 a4 69 .O..g...i#.....i
01a0 - 2e 81 72 c9 08 ba 96 c6-16 80 b4 27 de c2 35 c5 ..r........'..5.
01b0 - 81 e1 58 82 76 21 d9 75-34 0e 70 37 e4 23 aa 01 ..X.v!.u4.p7.#..
01c0 - f3 5d 66 19 b9 99 .]f...
Start Time: 1579896706
Timeout : 7200 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
Extended master secret: yes
---
closed