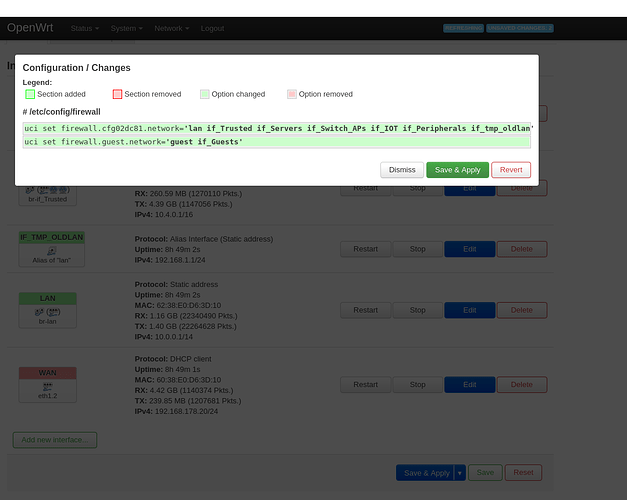
I have a concrete example of how (L)uci can make a mess of things.
When moving my guests interface back to it's own fwzone I normally just save&apply.
But when looking at the unsaved changes first I saw references to interfaces that have long since been deleted using (L)uci. Image at the bottom.
Turns out that the lan firewall zone is not properly updated by uci when deleting interfaces from Luci that are still in a firewall zone. I am sure I am doing something wrong but just a heads up to @developers
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd68:74a7:6e62::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
content removed due to considerations
option netmask '255.252.0.0'
option delegate '0'
option force_link '0'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
option peerdns '0'
list dns '1.1.1.1'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0 1 2 3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '4 6t'
config interface 'if_Trusted'
option proto 'static'
option force_link '0'
option type 'bridge'
content removed due to considerations
option netmask '255.255.0.0'
option ifname 'eth0.40'
option delegate '0'
list dns '1.1.1.1'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '2t 5t'
option vid '40'
config interface 'if_Guests'
option proto 'static'
option type 'bridge'
content removed due to considerations
option netmask '255.255.0.0'
option ifname 'eth0.50'
option delegate '0'
option force_link '0'
list dns '1.1.1.1'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '2t 5t'
option vid '50'
config interface 'if_tmp_oldlan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ifname '@lan'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan if_Trusted if_Servers if_Switch_APs if_IOT if_Peripherals if_tmp_oldlan if_Guests'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'lan'
option name 'block iot wan'
option src_ip '192.168.1.128/25'
option dest 'wan'
option target 'DROP'
config rule
option src 'lan'
option name 'block default ipcam'
option src_ip '192.168.1.10'
option dest 'wan'
option target 'DROP'
config redirect
option dest_port '443'
option src 'wan'
option name 'guideriis'
option src_dport '443'
option target 'DNAT'
option dest 'lan'
option proto 'tcp udp'
option dest_ip '192.168.1.111'
config zone 'guest'
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option network 'guest'
config forwarding 'guest_wan'
option src 'guest'
option dest 'wan'
config rule 'guest_dns'
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option proto 'tcp udp'
option target 'ACCEPT'
config rule 'guest_dhcp'
option name 'Allow-DHCP-Guest'
option src 'guest'
option dest_port '67'
option family 'ipv4'
option proto 'udp'
option target 'ACCEPT'