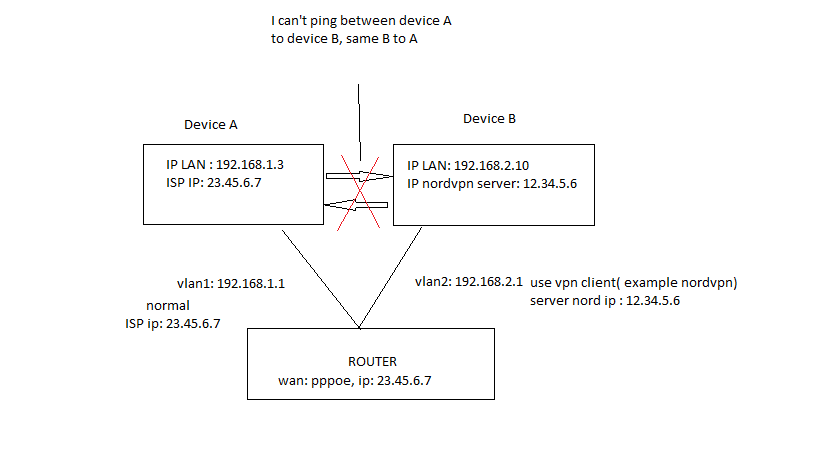
Hi all, i'm newbie, im trying setup 2 vlans (example 192.168.1.1 and 192.168.4.1), one use openvpn client ( like nordvpn ), one use normal with internet. Everything is working fine but when i ping between 2 vlans get result: "destination port unreachable" ( i can ping again if i turnoff openvpn client service ), someone can tell me is it possible ?Tks
//Sorry my English so bad.
you did not mention where you are pinging from?
makes all the difference!
luckily you mentioned the openvpn->off resolves it.
what this means is... a device... that is in the transmission path between pinger and pingee...
a) alters it's routing table... thus... making the pings fail....
b) instantiates a firewall rule that prevents the ping
two commands
traceroute ( linux ) | tracert ( *otheros )
and
ip route
run on every host from point a to point b... will get to the bottom of it.
you should also mention how the vlan's are physically assigned.... ( out what interfaces they flow ).
uci show network; uci show firewall
ip a; ip r; ip ru
/etc/init.d/network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fda6:229c:8e65::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth1.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.100.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.dns='8.8.8.8 8.8.4.4'
network.lan4=interface
network.lan4.type='bridge'
network.lan4.ifname='eth1.4'
network.lan4.proto='static'
network.lan4.ipaddr='192.168.4.1'
network.lan4.netmask='255.255.255.0'
network.lan4.ip6assign='60'
network.wan=interface
network.wan.ifname='eth0.2'
network.wan.proto='pppoe'
network.wan.username='xxxxxxxx'
network.wan.password='xxxxxxxx'
network.wan.ipv6='auto'
network.wan.peerdns='0'
network.wan.dns='8.8.8.8 8.8.4.4 1.1.1.1 1.0.0.1'
network.wan6=interface
network.wan6.ifname='eth0.2'
network.wan6.proto='dhcpv6'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0t 2 3 4 5'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='1 6t'
network.@switch_vlan[1].vid='2'
network.@route[0]=route
network.@route[0].interface='lan'
network.@route[0].netmask='255.255.255.0'
network.@route[0].target='192.168.4.0'
network.@route[0].gateway='192.168.4.1'
network.@switch_vlan[2]=switch_vlan
network.@switch_vlan[2].device='switch0'
network.@switch_vlan[2].vlan='3'
network.@switch_vlan[2].vid='4'
network.@switch_vlan[2].ports='0t 2t 3t 4t 5t'
network.@route[1]=route
network.@route[1].netmask='255.255.255.0'
network.@route[1].interface='lan4'
network.@route[1].target='192.168.100.0'
network.@route[1].gateway='192.168.100.1'
network.@route[2]=route
network.@route[2].interface='lan'
network.@route[2].target='192.168.1.0'
network.@route[2].netmask='255.255.255.0'
network.@route[2].gateway='192.168.100.205'
network.vpnserver=interface
network.vpnserver.ifname='tun1'
network.vpnserver.proto='none'
network.nordvpntun=interface
network.nordvpntun.proto='none'
network.nordvpntun.ifname='tun0'
firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].flow_offloading='1'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].network='lan'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].device='tun1'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].forward='ACCEPT'
firewall.@zone[1].network='wan wan6'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].name='lan4'
firewall.@zone[2].network='lan4'
firewall.@zone[2].forward='ACCEPT'
firewall.@zone[2].device='tun0'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].dest='wan'
firewall.@forwarding[0].src='lan'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].dest='wan'
firewall.@forwarding[1].src='lan4'
firewall.vpn=rule
firewall.vpn.name='Allow-OpenVPN'
firewall.vpn.src='wan'
firewall.vpn.proto='udp'
firewall.vpn.target='ACCEPT'
firewall.vpn.dest_port='11914'
firewall.@zone[3]=zone
firewall.@zone[3].output='ACCEPT'
firewall.@zone[3].masq='1'
firewall.@zone[3].mtu_fix='1'
firewall.@zone[3].network='nordvpntun'
firewall.@zone[3].name='vpn'
firewall.@zone[3].input='REJECT'
firewall.@zone[3].forward='REJECT'
firewall.@zone[4]=zone
firewall.@zone[4].name='vpnserver'
firewall.@zone[4].input='ACCEPT'
firewall.@zone[4].output='ACCEPT'
firewall.@zone[4].network='vpnserver'
firewall.@zone[4].forward='ACCEPT'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].dest='vpn'
firewall.@forwarding[2].src='lan'
firewall.@forwarding[3]=forwarding
firewall.@forwarding[3].dest='vpn'
firewall.@forwarding[3].src='lan4'
firewall.@forwarding[4]=forwarding
firewall.@forwarding[4].dest='vpn'
firewall.@forwarding[4].src='vpnserver'
ip a; ip r; ip ru
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 11:11:11:f1:11:11 brd ff:ff:ff:ff:ff:ff
inet6 1111::16cc:20ff:fef1:1111/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 11:11:11:f1:a5:da brd ff:ff:ff:ff:ff:ff
inet6 1111::16cc:20ff:fef1:a5da/64 scope link
valid_lft forever preferred_lft forever
4: ifb0: <BROADCAST,NOARP> mtu 1500 qdisc noop state DOWN group default qlen 32
link/ether aa:69:48:2e:bb:62 brd ff:ff:ff:ff:ff:ff
5: ifb1: <BROADCAST,NOARP> mtu 1500 qdisc noop state DOWN group default qlen 32
link/ether 22:5f:8b:1a:fb:e2 brd ff:ff:ff:ff:ff:ff
24: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 11:11:11:f1:a5:da brd ff:ff:ff:ff:ff:ff
inet 192.168.100.1/24 brd 192.168.100.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 2001:ee0:4001:6f44::1/64 scope global dynamic noprefixroute
valid_lft 767sec preferred_lft 767sec
inet6 fda6:229c:8e65::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 1111::16cc:20ff:fef1:a5da/64 scope link
valid_lft forever preferred_lft forever
25: eth1.1@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 11:11:11:f1:a5:da brd ff:ff:ff:ff:ff:ff
26: br-lan4: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 11:11:11:f1:a5:da brd ff:ff:ff:ff:ff:ff
inet 192.168.4.1/24 brd 192.168.4.255 scope global br-lan4
valid_lft forever preferred_lft forever
inet6 fda6:229c:8e65:10::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 1111::16cc:20ff:fef1:a5da/64 scope link
valid_lft forever preferred_lft forever
27: eth1.4@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan4 state UP group default qlen 1000
link/ether 11:11:11:f1:a5:da brd ff:ff:ff:ff:ff:ff
28: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 11:11:11:f1:11:11 brd ff:ff:ff:ff:ff:ff
inet6 1111::16cc:20ff:fef1:1111/64 scope link
valid_lft forever preferred_lft forever
29: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc fq_codel state UNKNOWN group default qlen 3
link/ppp
inet 123.123.11.12 peer 123.24.54.1/32 scope global pppoe-wan
valid_lft forever preferred_lft forever
inet6 2001:ee0:4002:86f4:9572:2261:122b:8da5/64 scope global dynamic noprefixroute
valid_lft 2591567sec preferred_lft 604367sec
inet6 1111::9572:2261:122b:8da5/10 scope link
valid_lft forever preferred_lft forever
30: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 11:11:11:f1:a5:d9 brd ff:ff:ff:ff:ff:ff
inet6 1111::16cc:20ff:fef1:a5d9/64 scope link
valid_lft forever preferred_lft forever
31: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 11:11:11:f1:a5:d8 brd ff:ff:ff:ff:ff:ff
inet6 1111::16cc:20ff:fef1:a5d8/64 scope link
valid_lft forever preferred_lft forever
32: wlan1-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan4 state UP group default qlen 1000
link/ether 16:cc:20:f1:a5:d9 brd ff:ff:ff:ff:ff:ff
inet6 1111::14cc:20ff:fef1:a5d9/64 scope link
valid_lft forever preferred_lft forever
33: tun1: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
link/none
inet 192.168.8.1/24 brd 192.168.8.255 scope global tun1
valid_lft forever preferred_lft forever
inet6 1111::155f:69fe:9f62:845b/64 scope link stable-privacy
valid_lft forever preferred_lft forever
34: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
link/none
inet 10.8.8.10/24 brd 10.8.8.255 scope global tun0
valid_lft forever preferred_lft forever
inet6 1111::f93f:d0d9:70d4:e34/64 scope link stable-privacy
valid_lft forever preferred_lft forever
default via 123.24.54.1 dev pppoe-wan proto static
10.8.8.0/24 dev tun0 proto kernel scope link src 10.8.8.10
118.69.201.202 via 123.24.54.1 dev pppoe-wan
123.24.54.1 dev pppoe-wan proto kernel scope link src 123.123.11.12
192.168.1.0/24 via 192.168.100.205 dev br-lan proto static
192.168.4.0/24 dev br-lan4 proto kernel scope link src 192.168.4.1
192.168.8.0/24 dev tun1 proto kernel scope link src 192.168.8.1
192.168.100.0/24 dev br-lan proto kernel scope link src 192.168.100.1
0: from all lookup local
32738: from all fwmark 0x20000 lookup 202
32739: from all fwmark 0x10000 lookup 201
32762: from all to 192.168.4.0/24 lookup vpn
32763: from 192.168.4.0/24 lookup vpn
32766: from all lookup main
32767: from all lookup default
It is difficult to express with my English, thank you  .
.
118.69.201.202 is the nordvpn server ip.
One problem i can't connect isp ip if i use vlan2 ( nordvpn client), example i use port 80 for nginx, when i connect 23.45.6.7, it result
" Forbidden
Rejected request from RFC1918 IP to public server address"
ip -4 route list table all
iptables-save | grep -i -e mark
ip -4 route list table all
default dev tun0 table vpn scope link
192.168.4.0/24 dev br-lan4 table vpn scope link src 192.168.4.1
default via 123.24.54.1 dev pppoe-wan table 201
default via 10.8.8.10 dev tun0 table 202
default via 123.24.54.1 dev pppoe-wan proto static
10.8.8.0/24 dev tun0 proto kernel scope link src 10.8.8.10
118.69.201.202 via 123.24.54.1 dev pppoe-wan
123.24.54.1 dev pppoe-wan proto kernel scope link src 123.123.11.12
192.168.1.0/24 via 192.168.100.205 dev br-lan proto static
192.168.4.0/24 dev br-lan4 proto kernel scope link src 192.168.4.1
192.168.8.0/24 dev tun1 proto kernel scope link src 192.168.8.1
192.168.100.0/24 dev br-lan proto kernel scope link src 192.168.100.1
broadcast 10.8.8.0 dev tun0 table local proto kernel scope link src 10.8.8.10
local 10.8.8.10 dev tun0 table local proto kernel scope host src 10.8.8.10
broadcast 10.8.8.255 dev tun0 table local proto kernel scope link src 10.8.8.10
local 123.123.11.12 dev pppoe-wan table local proto kernel scope host src 123.123.11.12
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.4.0 dev br-lan4 table local proto kernel scope link src 192.168.4.1
local 192.168.4.1 dev br-lan4 table local proto kernel scope host src 192.168.4.1
broadcast 192.168.4.255 dev br-lan4 table local proto kernel scope link src 192.168.4.1
broadcast 192.168.8.0 dev tun1 table local proto kernel scope link src 192.168.8.1
local 192.168.8.1 dev tun1 table local proto kernel scope host src 192.168.8.1
broadcast 192.168.8.255 dev tun1 table local proto kernel scope link src 192.168.8.1
broadcast 192.168.100.0 dev br-lan table local proto kernel scope link src 192.168.100.1
local 192.168.100.1 dev br-lan table local proto kernel scope host src 192.168.100.1
broadcast 192.168.100.255 dev br-lan table local proto kernel scope link src 192.168.100.1
iptables-save | grep -i -e mark
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A PREROUTING -m mark --mark 0x0/0xff0000 -j VPR_PREROUTING
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A INPUT -m mark --mark 0x0/0xff0000 -j VPR_INPUT
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A FORWARD -m mark --mark 0x0/0xff0000 -j VPR_FORWARD
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A OUTPUT -m mark --mark 0x0/0xff0000 -j VPR_OUTPUT
-A VPR_PREROUTING -p tcp -m multiport --sports 11914 -m comment --comment VPN_Server -j MARK --set-xmark 0x10000/0xff0000
-A VPR_PREROUTING -m set --match-set nordvpntun dst -j MARK --set-xmark 0x20000/0xff0000
-A VPR_PREROUTING -m set --match-set wan dst -j MARK --set-xmark 0x10000/0xff0000
firewall.@zone[3].network='nordvpntun'
Does this exist ^?
Would be helpful if you wrote all the names from the firewall rule on the diagram.
-zone name
-interface name
-friendly interface names
The ones your used are a little confusing.... ( i do it too but i don't help with new setups... clear consistent conventions! )
Rlan1 = tun1 = vpnzone1
Rlan2 = tun2 = vpnzone2
etc.
uci -q delete firewall.lan_lan4
uci set firewall.lan_lan4="forwarding"
uci set firewall.lan_lan4.src="lan"
uci set firewall.lan_lan4.dest="lan4"
uci -q delete firewall.lan4_lan
uci set firewall.lan4_lan="forwarding"
uci set firewall.lan4_lan.src="lan4"
uci set firewall.lan4_lan.dest="lan"
uci commit firewall
service firewall restart