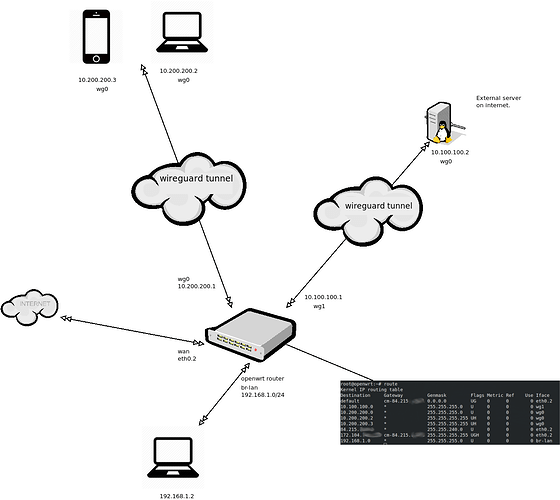
When i ping from 192.168.1.2 (client br-lan) to 10.100.100.2 connected to wg1 interface on router, everything works fine.
But when i try to curl a service running on that same ip 10.100.100.2 on port 5000 the response does not get routed back to the client that asked for it.
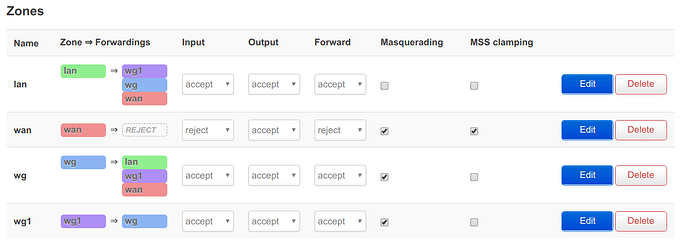
Masquarade is on for the zone.
➜ ~ ping -c1 10.100.100.2
PING 10.100.100.2 (10.100.100.2) 56(84) bytes of data.
64 bytes from 10.100.100.2: icmp_seq=1 ttl=63 time=35.6 ms
--- 10.100.100.2 ping statistics ---
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 35.688/35.688/35.688/0.000 ms
➜ ~ curl 10.100.100.2:5000
curl: (7) Failed to connect to 10.100.100.2 port 5000: Connection refused
root@openwrt:~# tcpdump -i wg1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on wg1, link-type RAW (Raw IP), capture size 262144 bytes
13:14:50.469236 IP 10.100.100.1 > 10.100.100.2: ICMP echo request, id 27326, seq 1, length 64
13:14:50.506108 IP 10.100.100.2 > 10.100.100.1: ICMP echo reply, id 27326, seq 1, length 64
13:14:51.783712 IP 10.100.100.1.43802 > 10.100.100.2.5000: Flags [S], seq 56625904, win 29200, options [mss 1460,sackOK,TS val 842812138 ecr 0,nop,wscale 7], length 0
13:14:51.818168 IP 10.100.100.2.5000 > 10.100.100.1.43802: Flags [R.], seq 0, ack 56625905, win 0, length 0
Here is a tcpdump on the client (192.168.1.2) with ping first then curl.
sudo tcpdump -vv -i eth1 -n host 10.100.100.2
tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
13:38:23.693982 IP (tos 0x0, ttl 64, id 15668, offset 0, flags [DF], proto ICMP (1), length 84)
192.168.1.2 > 10.100.100.2: ICMP echo request, id 30901, seq 1, length 64
13:38:23.728750 IP (tos 0x0, ttl 63, id 48793, offset 0, flags [none], proto ICMP (1), length 84)
10.100.100.2 > 192.168.1.2: ICMP echo reply, id 30901, seq 1, length 64
13:38:25.303043 IP (tos 0x0, ttl 64, id 41152, offset 0, flags [DF], proto TCP (6), length 60)
192.168.1.2.44126 > 10.100.100.2.5000: Flags [S], cksum 0x04e7 (correct), seq 2543336090, win 29200, options [mss 1460,sackOK,TS val 844225677 ecr 0,nop,wscale 7], length 0
13:38:25.338708 IP (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 40)
10.100.100.2.5000 > 192.168.1.2.44126: Flags [R.], cksum 0xeda5 (correct), seq 0, ack 2543336091, win 0, length 0