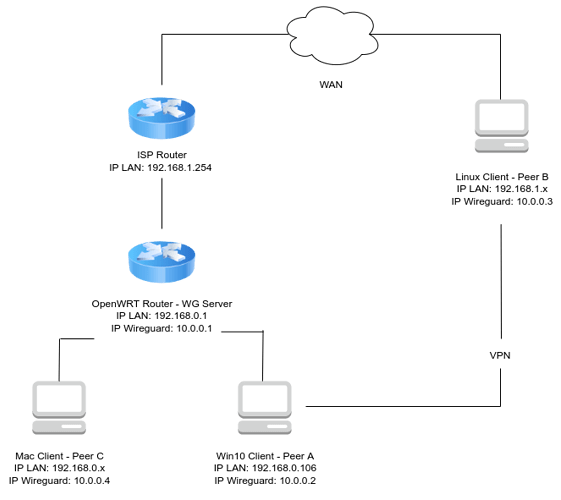
Hi,
I have a Wireguard server running on OpenWRT and I would like to have a peer to peer connection between Peer A (Win10 client) and B (Linux client) through the server (basically Peer B should act like it's part of A's LAN).
As you can see from the map of my network, Peer A is on the same LAN as the WG server while Peer B is on the internet. You might have noticed Peer C (Mac client) but I am not interested in connecting directly to it right now. I have a static public IP for the WAN interface which should be under NAT.
As of now everything works fine except that Peer B cannot reach A:
-
Peer A cannot ping the WG server, got "General Failure" error in Powershell
-
Peer A can ping B and not vice versa because packets get lost
-
Peer B can ping the WG server
Note that Peer A firewall is disabled. Could you please tell me what's wrong? Thanks in advance!
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option input 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config rule
option name 'Allow-Wireguard-Inbound'
list proto 'udp'
option src 'wan'
option dest_port '50820'
option target 'ACCEPT'
option dest 'wgnet'
config redirect
option target 'DNAT'
list proto 'udp'
option src 'wan'
option src_dport '50820'
option dest_port '50820'
option dest 'wgnet'
option dest_ip '192.168.0.1'
option name 'WAN_WGNET_R7800'
config zone
option name 'wgnet'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'wgnet'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'wgnet'
option dest 'lan'
config forwarding
option src 'wgnet'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'wgnet'
config forwarding
option src 'wan'
option dest 'wgnet'
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd54:538b:baad::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0t'
config interface 'wgnet'
option proto 'wireguard'
option private_key '<wg-server-private-key>'
option listen_port '50820'
list addresses '10.0.0.1/32'
config wireguard_wgnet
option description 'Peer B'
option public_key '<peer-B-public-key>'
option persistent_keepalive '25'
list allowed_ips '10.0.0.3/32'
option route_allowed_ips '1'
config wireguard_wgnet
option description 'Peer A'
option public_key '<peer-A-public-key>'
list allowed_ips '10.0.0.2/32'
option persistent_keepalive '25'
option route_allowed_ips '1'
WG server config
[Interface]
ListenPort = 50820
PrivateKey = <wg-server-private-key>
[Peer]
PublicKey = <peer-B-public-key>
AllowedIPs = 10.0.0.3/32
PersistentKeepalive = 25
[Peer]
PublicKey = <peer-A-public-key>
AllowedIPs = 10.0.0.2/32
PersistentKeepalive = 25
Peer A config
[Interface]
PrivateKey = <peer-A-private-key>
Address = 10.0.0.2/32
[Peer]
PublicKey = <wg-server-public-key>
AllowedIPs = 10.0.0.1/32
PersistentKeepalive = 25
Peer B config
[Interface]
PrivateKey = <peer-B-private-key>
Address = 10.0.0.3/32
[Peer]
PublicKey = <wg-server-public-key>
AllowedIPs = 10.0.0.1/32
Endpoint = <ISP-public-IP>:50820
PersistentKeepalive = 25