Hello,
I try to configure my LEDE 17.01.3 with OpenVPN (mebtls) in bridge mode. I've followed this and this tutorial butI still can't manage it to work. (In routed mode, it works).
For testing purpose, I've installed LEDE in Virtualbox and 2 Debian stable:
DEBIAN1 (DHCP) ---- (192.168.1.1/24 - br-lan/eth0) LEDE (172.16.0.1/16 - eth1) ---- DEBIAN2 (172.16.0.2/16)
There is a third (eth2) network interface for management connected to VirtualBox Host-Only Adapter (192.168.56.1).
OpenVPN configuration:
root@LEDE:~# cat /etc/config/openvpn
config openvpn 'myvpn'
option enabled '1'
option verb '3'
option proto 'udp'
option port '1194'
option dev 'tap'
option mode 'server'
option tls_server '1'
list push 'route-gateway dhcp'
list push 'redirect-gateway def1'
option keepalive '10 120'
option ca '/etc/openvpn/ca.crt'
option cert '/etc/openvpn/my-server.crt'
option key '/etc/openvpn/my-server.key'
option dh '/etc/openvpn/dh2048.pem'
list 'push' 'dhcp-option DNS 192.168.1.1'
option 'client_to_client' '1'
option 'comp_lzo' 'no'
option 'keepalive' '10 120'
option 'persist_key' '1'
option 'persist_tun' '1'
Firewall configuration:
root@LEDE:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option name 'newzone'
option input 'ACCEPT'
option forward 'REJECT'
option output 'ACCEPT'
option network 'mng'
config rule 'Allow_OpenVPN_Inbound'
option target 'ACCEPT'
option src '*'
option proto 'udp'
option dest_port '1194'
Network config:
root@LEDE:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fded:ae9d:bca2::/48'
config interface 'lan'
option type 'bridge'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.1'
option ifname 'eth0 tap0'
config interface 'wan'
option ifname 'eth1'
option _orig_ifname 'eth1'
option _orig_bridge 'false'
option proto 'static'
option delegate '0'
option ipaddr '172.16.0.1'
option netmask '255.255.0.0'
option broadcast '172.16.255.255'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config interface 'mng'
option proto 'static'
option netmask '255.255.255.0'
option ifname 'eth2'
option ipaddr '192.168.56.1'
option broadcast '192.168.56.255'
config interface 'vpn0'
option ifname 'tap0'
option proto 'none'
option auto '1'
Client config:
client
dev tap
proto udp
remote 172.16.0.1 1194
remote-cert-tls server
comp-lzo no
verb 3
<ca>
-----BEGIN CERTIFICATE-----
.................
I'm able to connect to my server with DEBIAN2 and after manually (??) do a "dhclient tap0" I can get an IP and ping the gateway (192.168.1.1).
From DEBIAN2 (192.168.1.157): ping, arping to DEBIAN1 doesn't work, neither a "netcat DEBIAN1 PORT". But if I do a tcpdump on DEBIAN1, I can see "ARP request" and "ARP reply".
From DEBIAN1 (192.168.1.145)8: ping DEBIAN2 doesn't work BUT I can see "arp request" and "icmp request". Also, sometimes, arping reply:
root@debian:~# arping 192.168.1.157
ARPING 192.168.1.157 from 192.168.1.145 eth0
Unicast reply from 192.168.1.157 [1E:79:30:7E:82:54] 1.076ms
^CSent 3 probes (1 broadcast(s))
Received 1 response(s)
This a strange behaviour, like if LEDE don't want to send packets from tap to lan.
Does anyone has a solution ?
Thanks !
P.S: here is the openvpn server log
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 TLS: Initial packet from [AF_INET]172.16.0.2:1194, sid=86e45079 53a174d2
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 VERIFY OK: depth=1, C=GB, ST=London, O=WWW Ltd.
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 VERIFY OK: depth=0, CN=my-client
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_VER=2.4.0
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_PLAT=linux
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_PROTO=2
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_NCP=2
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_LZ4=1
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_LZ4v2=1
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_LZO=1
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_COMP_STUB=1
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_COMP_STUBv2=1
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 peer info: IV_TCPNL=1
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 Control Channel: TLSv1.2, cipher TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384, 4096 bit key
Mon Oct 9 23:40:37 2017 daemon.notice openvpn(myvpn)[7747]: 172.16.0.2:1194 [my-client] Peer Connection Initiated with [AF_INET]172.16.0.2:1194
Mon Oct 9 23:40:37 2017 daemon.err openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 MULTI: no dynamic or static remote --ifconfig address is available for my-client/172.16.0.2:1194
Mon Oct 9 23:40:38 2017 daemon.notice openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 PUSH: Received control message: 'PUSH_REQUEST'
Mon Oct 9 23:40:38 2017 daemon.notice openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 SENT CONTROL [my-client]: 'PUSH_REPLY,route-gateway dhcp,redirect-gateway def1,dhcp-option DNS 192.168.1.1,ping 10,ping-restart 120,peer-id 0,cipher AES-256-GCM' (status=1)
Mon Oct 9 23:40:38 2017 daemon.notice openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 Data Channel: using negotiated cipher 'AES-256-GCM'
Mon Oct 9 23:40:38 2017 daemon.notice openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 Data Channel Encrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Mon Oct 9 23:40:38 2017 daemon.notice openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 Data Channel Decrypt: Cipher 'AES-256-GCM' initialized with 256 bit key
Mon Oct 9 23:40:57 2017 daemon.notice openvpn(myvpn)[7747]: my-client/172.16.0.2:1194 MULTI: Learn: 1e:79:30:7e:82:54 -> my-client/172.16.0.2:1194
Mon Oct 9 23:40:57 2017 daemon.info dnsmasq-dhcp[4758]: DHCPREQUEST(br-lan) 192.168.56.224 1e:79:30:7e:82:54
Mon Oct 9 23:40:57 2017 daemon.info dnsmasq-dhcp[4758]: DHCPNAK(br-lan) 192.168.56.224 1e:79:30:7e:82:54 wrong network
Mon Oct 9 23:40:58 2017 daemon.info odhcpd[1138]: Using a RA lifetime of 0 seconds on br-lan
Mon Oct 9 23:41:00 2017 daemon.info dnsmasq-dhcp[4758]: DHCPDISCOVER(br-lan) 1e:79:30:7e:82:54
Mon Oct 9 23:41:00 2017 daemon.info dnsmasq-dhcp[4758]: DHCPOFFER(br-lan) 192.168.1.157 1e:79:30:7e:82:54
Mon Oct 9 23:41:00 2017 daemon.info dnsmasq-dhcp[4758]: DHCPDISCOVER(br-lan) 1e:79:30:7e:82:54
Mon Oct 9 23:41:00 2017 daemon.info dnsmasq-dhcp[4758]: DHCPOFFER(br-lan) 192.168.1.157 1e:79:30:7e:82:54
Mon Oct 9 23:41:00 2017 daemon.info dnsmasq-dhcp[4758]: DHCPREQUEST(br-lan) 192.168.1.157 1e:79:30:7e:82:54
Mon Oct 9 23:41:00 2017 daemon.info dnsmasq-dhcp[4758]: DHCPACK(br-lan) 192.168.1.157 1e:79:30:7e:82:54 debian
Mon Oct 9 23:44:44 2017 kern.info kernel: [ 2315.041011] device br-lan entered promiscuous mode
Mon Oct 9 23:45:50 2017 daemon.info odhcpd[1138]: Using a RA lifetime of 0 seconds on br-lan
Mon Oct 9 23:47:00 2017 kern.info kernel: [ 2450.758084] device br-lan left promiscuous mode
Mon Oct 9 23:54:35 2017 daemon.info odhcpd[1138]: Using a RA lifetime of 0 seconds on br-lan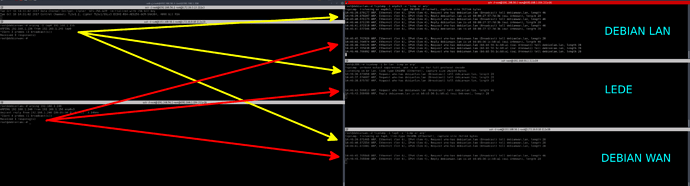
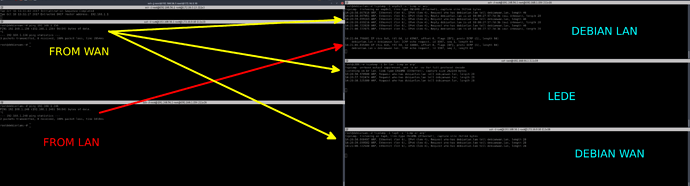
 It can't handle MAC address change as ESXi (a vswitch option).
It can't handle MAC address change as ESXi (a vswitch option).