DoXer
September 4, 2021, 2:58pm
1
Hello,
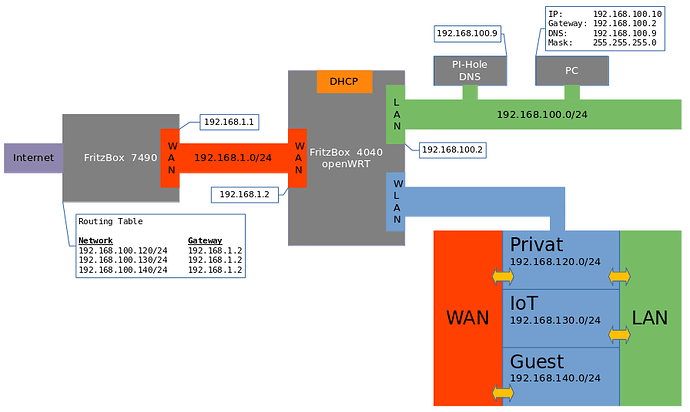
I have a fresh setup on a FritzBox 4040 with V21.02. and have made the appropriate settings. Unfortunately, I have no Internet access with it.
The DNS (PI-HOLE) is running correctly as it works in the current setup.
I have set the routes on the Fritzbox 7490 to avoid a double NAT.
What is possible after the setup:
access to openWRT via 192.168.100.1
after ssh-login in openWRT a ping to 192.168.1.1 is possible
no ping from the PC (192.168.100.10) to 192.168.1.1 and 192.168.1.2 and thus probably no Internet.
What have I done wrong?
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd44:e14b:4618::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.100.1'
option device 'eth0'
config interface 'wan'
option device 'eth1'
option proto 'static'
option ipaddr '192.168.1.2'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'REJECT'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
1 Like
Does it work if you enable masquerading on the WAN firewall zone?
DoXer:
no ping from the PC (192.168.100.10) to 192.168.1.1 and 192.168.1.2 and thus probably no Internet.
Don't assume "probably no internet" -- please test this. Ping to 8.8.8.8 and then google.com and see if you can get any responses.
1 Like
DoXer
September 4, 2021, 4:58pm
5
Ping 8.8.8.8 inside openWRT (192.168.1.2) is Ok. Outside (from PC 192.168.100.10) not.
ping google.de is not succesful
What does the PC show for the full IP information (IP address, subnet mask, gateway, dns)?
DoXer
September 4, 2021, 5:10pm
7
IP: 192.168.100.10
The gateway is wrong. It should be 192.168.100.1 based on the config you presented earlier.
Once you fix the gateway, on the PC, pings to 8.8.8.8 should work. If pings to google.de fail, that is likely the pihole at that point.
2 Likes
DoXer
September 4, 2021, 6:00pm
10
Sorry, indeed a mistake in the config. But also after changing to the correct gateway-ip a ping from PC is not successful. Below the corrected config-network. I also added the broadcast-ip,
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd44:e14b:4618::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'eth0'
option ipaddr '192.168.100.2'
option gateway '192.168.1.1'
option broadcast '192.168.100.255'
config interface 'wan'
option device 'eth1'
option proto 'static'
option ipaddr '192.168.1.2'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
option broadcast '192.168.100.255'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
Clear the gateway field from the lan config.
What does the pc see as the current network settings?
1 Like
DoXer
September 4, 2021, 6:07pm
12
Ok, i downgrade to 19.7. But I have a fresh install (firstboot) of 21.02, without restoring a backup. I created everything new.
DoXer
September 4, 2021, 6:18pm
13
Normally I'm working with ARCH linux, but don't know how to get the details of the interface. For that I started Windows.
Ethernet-Adapter Ethernet 2:
Verbindungsspezifisches DNS-Suffix:
Beschreibung. . . . . . . . . . . : Intel(R) 82579LM Gigabit Network Connection
Physische Adresse . . . . . . . . : F0-92-1C-5B-F9-52
DHCP aktiviert. . . . . . . . . . : Nein
Autokonfiguration aktiviert . . . : Ja
IPv4-Adresse . . . . . . . . . . : 192.168.100.200(Bevorzugt)
Subnetzmaske . . . . . . . . . . : 255.255.255.0
Standardgateway . . . . . . . . . : 192.168.100.2
DNS-Server . . . . . . . . . . . : 192.168.100.9
NetBIOS über TCP/IP . . . . . . . : Aktiviert
The gateway is still wrong. Is this set by dhcp? Is the OpenWrt router your dhcp server? Or is that handled by the pihole?
DoXer
September 4, 2021, 6:24pm
15
No, fixed IP, DNS, Gateway. And again I made a typo, yes. I saw may mistake and changed it, no ping. The Gateway is 192.168.100.2
The gateway is not correct. It should be 192.168.100.1
DoXer
September 4, 2021, 7:17pm
18
I downgraded to 19.07, made a firstboot and made the setup via LUCI again.
Everything works as expected.
Looks like there is a bug in V21.02.rc4
1 Like
Can you describe the details of the bug you believe you have found?
To my eye, the issue was your gateway, but maybe there was something else going on.
DoXer
September 4, 2021, 7:31pm
20
Here the configs from 19.07.08 (as mentioned, no restore, rebuilded after firstboot).
So, I think the description of the bug is in my first post.
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdbf:29b3:652a::/48'
config interface 'lan'
option ifname 'eth0'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.100.2'
option gateway '192.168.1.1'
list dns '192.168.100.9'
config interface 'wan'
option ifname 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.1.2'
option gateway '192.168.1.1'
list dns '192.168.100.9'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'