Good afternoon people...
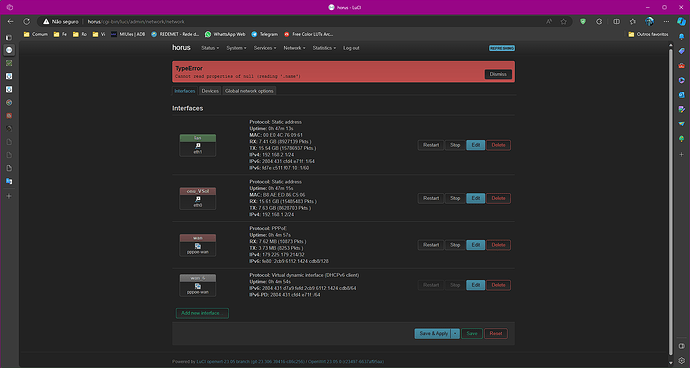
I'm finding it difficult to configure IPV6 correctly on my x64/64 router where I have the wan connected to eth0 and the lan connected to eth1...
My ISP delivers IPV6 to me on the wan_6 virtual interface and I can see something on the interface like "PD" - Prefix Delegation, right?
My configs of network are:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd7e:c511:0f07::/48'
config interface 'lan'
option device 'eth1'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option dhcpv6 'server'
option ra_management '1'
option ra 'server'
option ndp 'hybrid'
option delegate '0'
list ip6class 'wan_6'
option ip6assign '64'
config interface 'wan'
option proto 'pppoe'
option device 'eth0'
option username 'cliente@cliente'
option password 'cliente'
option ignore '1'
option dhcpv6 'relay'
option ra 'relay'
option ndp 'relay'
option master '1'
option ipv6 'auto'
option force_link '1'
config interface 'onu_VSol'
option proto 'static'
option device 'eth0'
option ipaddr '192.168.1.2'
option netmask '255.255.255.0'
config device
option name 'eth1'
option promisc '0'
and I have one firewall rule:
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'onu_VSol'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option target 'ACCEPT'
option src 'wan'
option proto 'udp'
option dest_port '546'
option name 'Allow DHCPv6 replies'
option family 'ipv6'
option src_port '547'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'NintendoSwitch'
list proto 'udp'
option src 'wan'
option src_dport '45000-65535'
option dest_ip '192.168.2.143'
option dest_port '45000-65535'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'DDNS 8181'
list proto 'tcp'
option src 'wan'
option src_dport '80'
option dest_ip '192.168.2.1'
option dest_port '81'
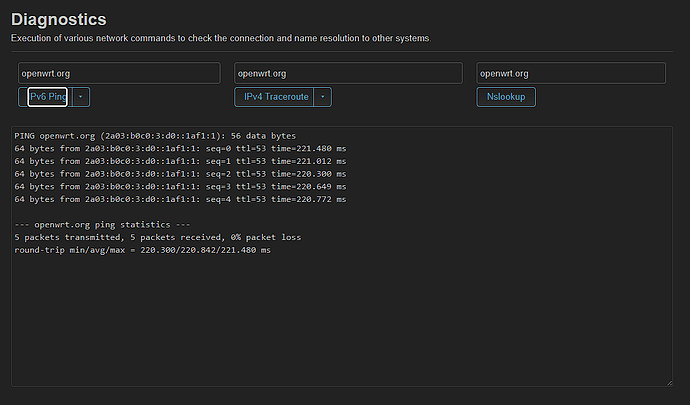
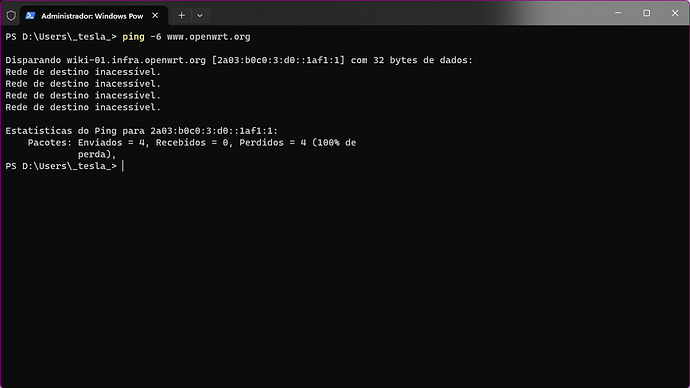
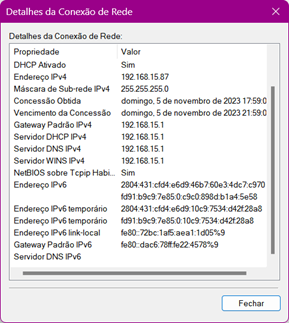
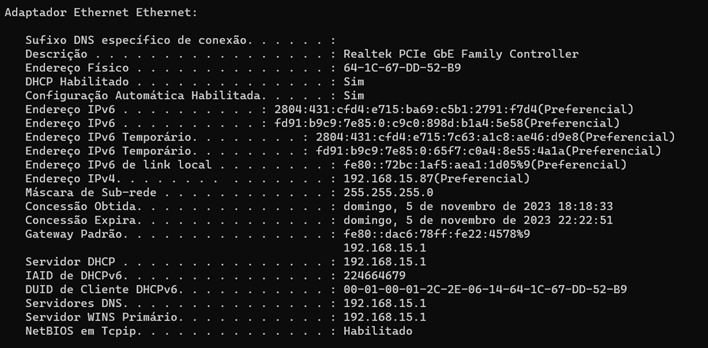
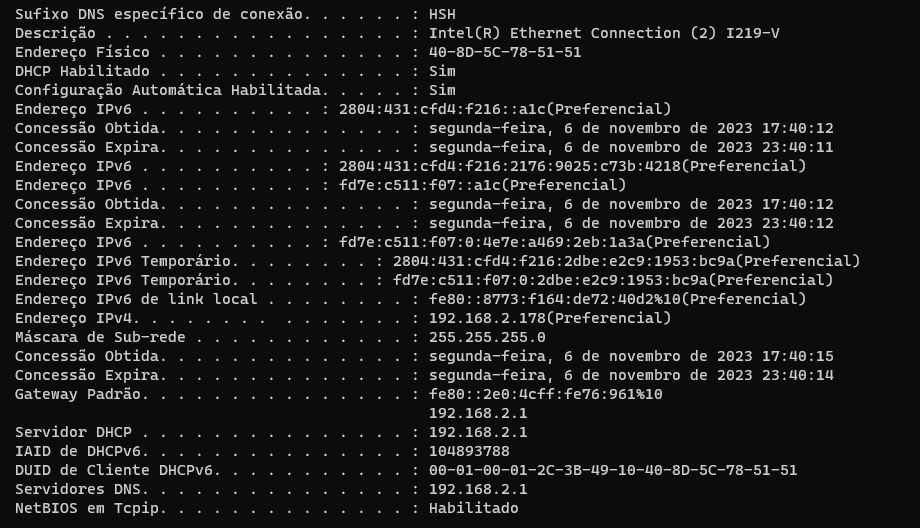
The interesting thing is that I receive IPV6 on my computers' network cards,like it:
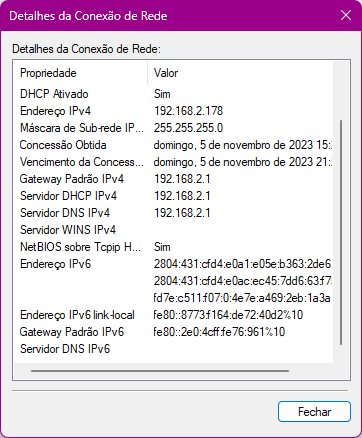
Router:
Physical interface eth0 (WAN):
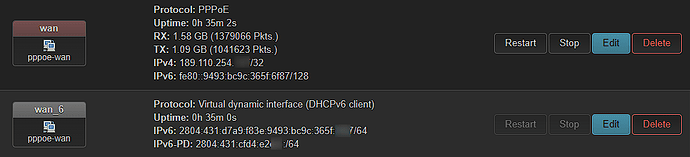
IPv6: fe80::9493:bc9c:365f:6f87/128
Advanced Settings:
=> Force Link: Checked
=> Obtain IPv6 address: Automatic
=> Override IPv6 routing table: none
=> Delegate IPv6 prefixes: Checked
=> IPv6 assignment length: disabled
=> IPv6 prefix filter: none
=> IPv6 suffix: none (default config is configured ::1)
=> IPv6 preference: none (default config is configured 0)
Virtual interface (wan_6):
IPv6: 2804:431:d7a9:f83e:9493:bc9c:365f:6f87/64
IPv6-PD: 2804:431:cfd4:e2ed::/64
It is not possible to change any configuration of this interface
ETH1 physical interface (LAN):
IPv6: 2804:431:cfd4:e2ed::1/64
Advanced Settings:
=> Force Link: Checked
=> Override IPv6 routing table: none
=> Delegate IPv6 prefixes: Not Checked
=> IPv6 assignment length: 64
=> IPv6 assignment hint: none (default config is configured 0)
=> IPv6 prefix filter: wan_6
=> IPv6 suffix: none (default config is configured ::1)
=> IPv6 preference: none (default config is configured 0)
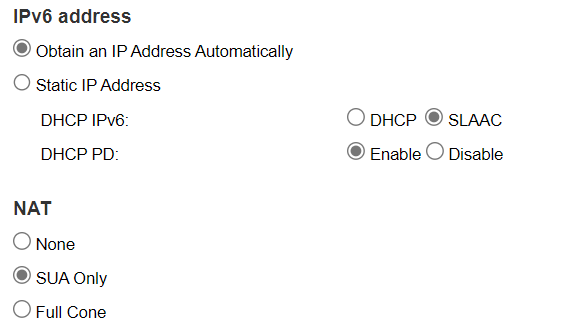
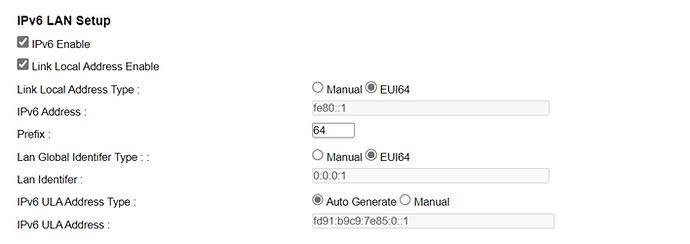
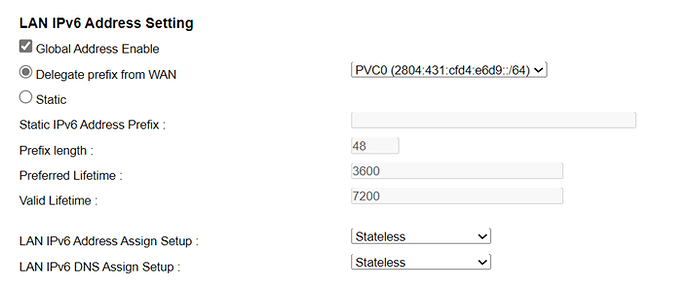
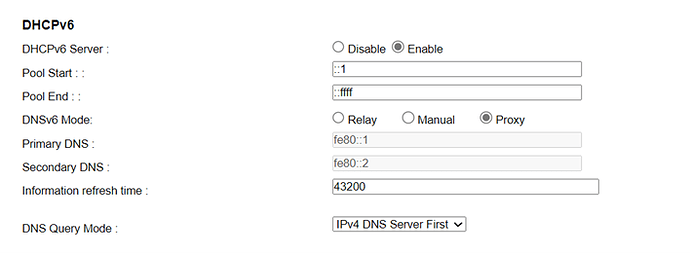
OK, I have with me the ISP's default modem settings where IPV6 works correctly, where it is configured to receive IPV6 automatically, in SLAAC mode and DHCP PD is active too and I don't have any other visible configuration, like this:
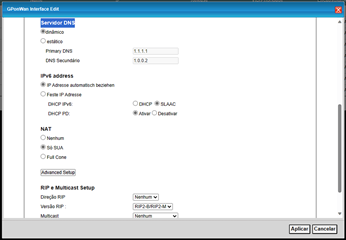
Going back to Openwrt, the dhcpv6 part of my lan interface is configured like this:
IPV6 Settings:
=> Designated master: none
=> RA-Service: server mode
=> DHCPv6-Service: server mode
=> Announced IPv6 DNS servers: none
=> Local IPv6 DNS server: none
=> Announced DNS domains: none
=> NDP-Proxy: disabled
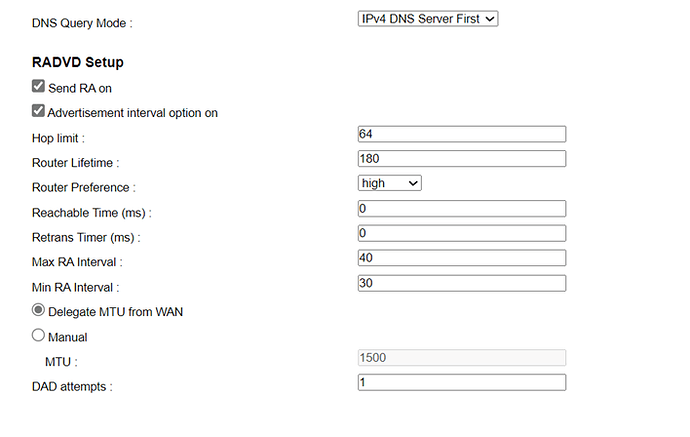
IPV6 RA Settings:
=> Default router: Automatic
=> Enable SLAAC: Checked
=> RA Flags: O and H
And the rest of the settings are set to default.
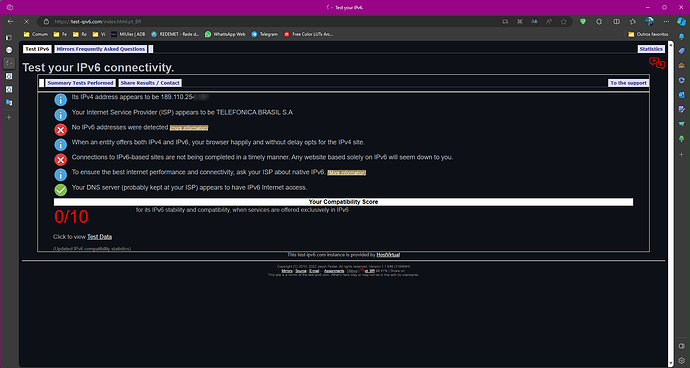
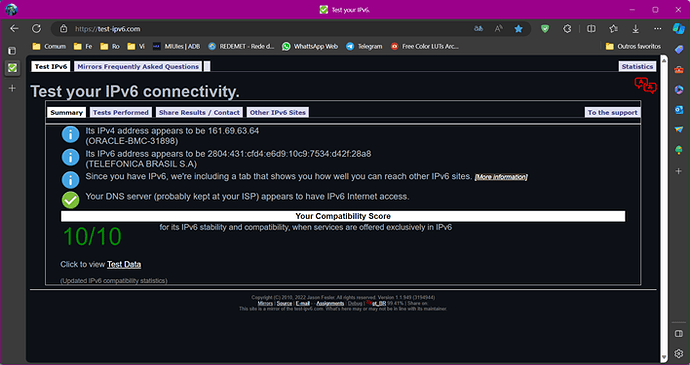
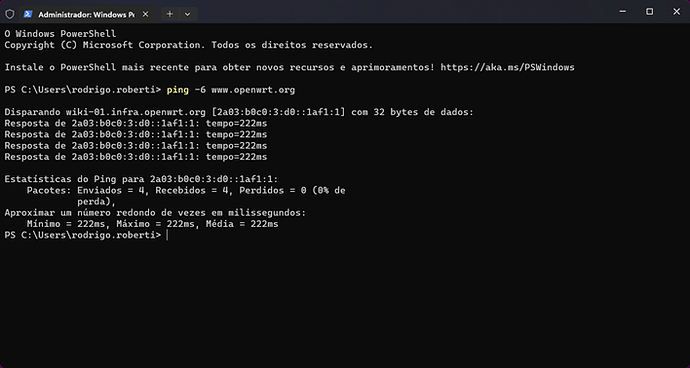
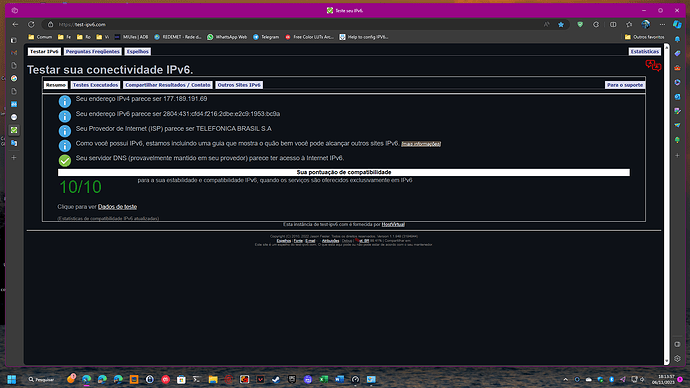
When I go to the website https://test-ipv6.com/ to test, I get this response:
Can anyone clarify and help me configure this correctly? I can start IPV6 configuration from scratch without any problems.
Sorry for my English, it's not my native language...