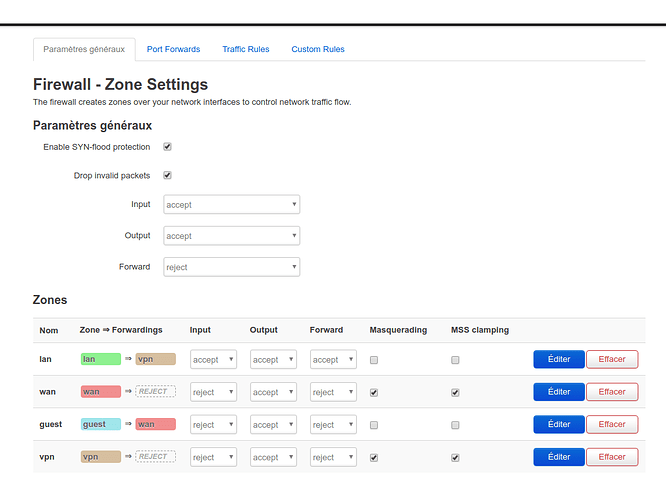
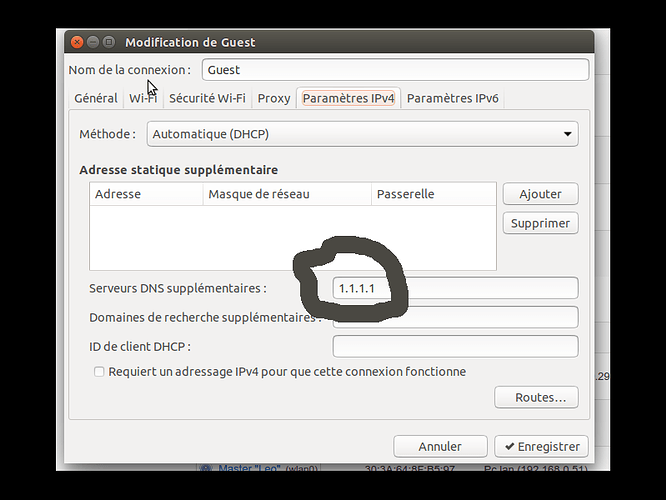
Hello everyone,
I am trying to setup a network where my Wifi guest lan go through normal internet and my normal lan go through VPN. Here is my config:
/etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option network 'lan'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'udp'
option dest_ip '192.168.0.51'
option name 'VPN Home'
option dest_port '1190'
option src_dip '192.168.1.20'
option src_dport '1190'
option enabled '0'
config zone
option name 'guest'
option output 'ACCEPT'
option network 'guest'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option dest 'wan'
option src 'guest'
config rule
option proto 'tcp udp'
option name 'Guest DNS'
option target 'ACCEPT'
option src 'guest'
option dest_port '53'
config rule
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
option name 'Guest DHCP'
option src 'guest'
config zone
option name 'vpn'
option forward 'REJECT'
option output 'ACCEPT'
option network 'tun0'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option dest 'vpn'
option src 'lan'
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdbe:de1b:2cd5::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.0.1'
config interface 'wan'
option ifname 'eth0.2'
option proto 'static'
option ipaddr '192.168.1.20'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
option dns '1.1.1.1 1.0.0.1'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
config interface 'tun0'
option proto 'none'
option ifname 'tun0'
option auto '1'
ifconfig
br-lan Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
inet addr:192.168.0.1 Bcast:192.168.0.255 Mask:255.255.255.0
inet6 addr: XX:XX:XX:XX:XX:XX /64 Scope:Link
inet6 addr: XX:XX:XX:XX:XX:XX ::1/60 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:46944824 errors:0 dropped:5444 overruns:0 frame:0
TX packets:69375180 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3564336608 (3.3 GiB) TX bytes:89932060810 (83.7 GiB)
eth0 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
inet6 addr: XX:XX:XX:XX:XX:XX /64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:74890661 errors:0 dropped:0 overruns:0 frame:0
TX packets:46830800 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:393637435 (375.4 MiB) TX bytes:2558298379 (2.3 GiB)
Interrupt:4
eth0.1 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:388628 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:92594978 (88.3 MiB)
eth0.2 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
inet addr:192.168.1.20 Bcast:192.168.1.255 Mask:255.255.255.0
inet6 addr: XX:XX:XX:XX:XX:XX /64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:74890660 errors:0 dropped:21049 overruns:0 frame:0
TX packets:46442158 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:93534886003 (87.1 GiB) TX bytes:6573346137 (6.1 GiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:15847 errors:0 dropped:0 overruns:0 frame:0
TX packets:15847 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:1541427 (1.4 MiB) TX bytes:1541427 (1.4 MiB)
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:10.8.0.11 P-t-P:10.8.0.11 Mask:255.255.255.0
inet6 addr: XX:XX:XX:XX:XX:XX /64 Scope:Link
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:69022232 errors:0 dropped:0 overruns:0 frame:0
TX packets:46330237 errors:0 dropped:8415 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:88920560050 (82.8 GiB) TX bytes:3460954780 (3.2 GiB)
wlan0 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
inet6 addr: fe80::b2be:76ff:fef7:3a3/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:68092609 errors:0 dropped:0 overruns:0 frame:0
TX packets:91489498 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:30089644217 (28.0 GiB) TX bytes:117781791208 (109.6 GiB)
wlan1 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
inet6 addr: XX:XX:XX:XX:XX:XX /64 Scope:Link
inet6 addr: XX:XX:XX:XX:XX:XX /64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:60433 errors:0 dropped:0 overruns:0 frame:0
TX packets:44678 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:4865027 (4.6 MiB) TX bytes:9884779 (9.4 MiB)
wlan1-1 Link encap:Ethernet HWaddr XX:XX:XX:XX:XX:XX
inet addr:192.168.2.1 Bcast:192.168.2.255 Mask:255.255.255.0
inet6 addr: XX:XX:XX:XX:XX:XX/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:7 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:864 (864.0 B)
ip route
0.0.0.0/1 via 10.8.0.1 dev tun0
default via 192.168.1.1 dev eth0.2 proto static
10.8.0.0/24 dev tun0 proto kernel scope link src 10.8.0.11
128.0.0.0/1 via 10.8.0.1 dev tun0
{vpn_serveur_adress} via 192.168.1.1 dev eth0.2
192.168.0.0/24 dev br-lan proto kernel scope link src 192.168.0.1
192.168.1.0/24 dev eth0.2 proto kernel scope link src 192.168.1.20
192.168.2.0/24 dev wlan1-1 proto kernel scope link src 192.168.2.1
ip rule
0: from all lookup local
32765: from 192.168.2.0/24 lookup guest
32766: from all lookup main
32767: from all lookup default
Policy routing for guest:
ip rule list table guest
32765: from 192.168.2.0/24 lookup guest
ip route list table guest
default via 192.168.1.1 dev eth0.2
Result: Everything works fine except my Wifi guest users can not access internet getting error: DNS_PROBE_FINISHED_BAD_CONFIG
But when i manually set DNS serveur in IPV4 settings on my guest client side everything works like i want. Can somebody help me with this DNS issue since i can not access all my guest device to manually set the DNS?
NB: My Openwrt Router(192.168.1.20) is behind the FAI router (192.168.1.1)
Thanks you in advance