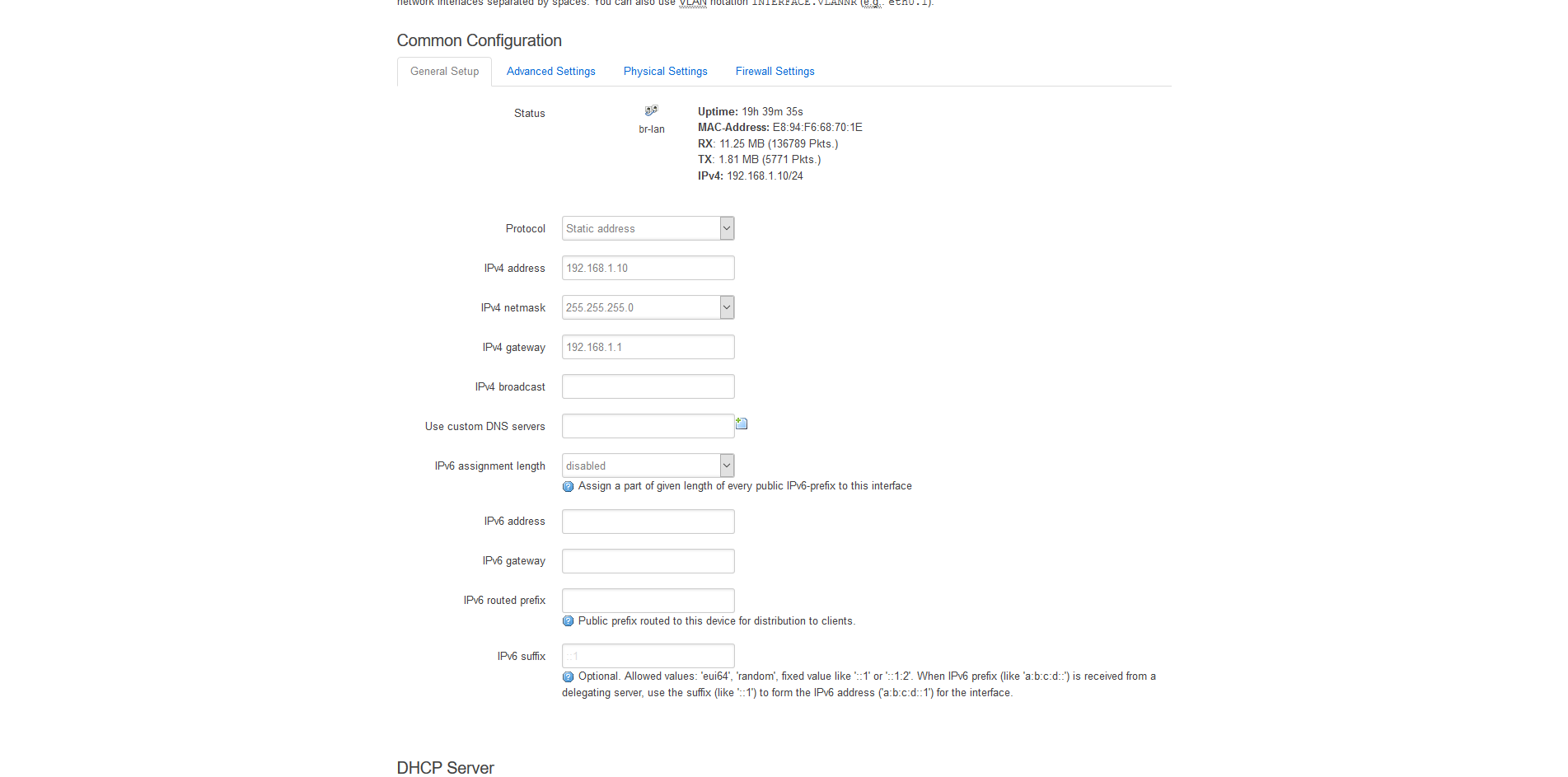
Hey all,
I've managed to install LEDE/OpenWRT on a Xiaomi Mi Router 3G, with the latest snapshot.
I'm attempting to use it to bridge (not sure if that's actually the right word) a wireless connection.
I've created two wireless networks, one as client and one as master. The client successfully connects to the wireless network, and hence the box itself has internet access. I've chosen to add unbound for DNS, which is also working find.
Now regarding the issue, I the second wireless network is on my lan, but neither devices connected to that network, nor via the ethernet ports have internet.
They can communicate internally, and DNS resolution works (router hosts that though), but any outward connection results in 'connection refused'. As I understand, I need to have the router masquerade connections from the lan outward, so that I can run a Google Home without other people casting to it.
My configs are as follows...
/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option local '/z/'
option domain 'z'
option port '53535'
config dhcp 'lan'
option interface 'lan'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
option dynamicdhcp '0'
list dhcp_option 'option:dns-server,192.168.1.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config host
option name 'dt'
option dns '1'
option mac 'REMOVED'
option ip '192.168.1.2'
option leasetime 'infinite'
config host
option name 'hm'
option dns '1'
option mac 'REMOVED'
option ip '192.168.1.3'
option leasetime 'infinite'
config host
option name 'cc'
option dns '1'
option mac 'REMOVED'
option ip '192.168.1.4'
option leasetime 'infinite'
config host
option name 'ph'
option dns '1'
option mac 'REMOVED'
option ip '192.168.1.5'
option leasetime 'infinite'
config host
option name 'lt'
option dns '1'
option mac 'REMOVED'
option ip '192.168.1.6'
option leasetime 'infinite'
/etc/config/firewall
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config defaults
option output 'ACCEPT'
option forward 'REJECT'
option input 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option forward 'REJECT'
option input 'REJECT'
option network 'wan wan6 wwan'
config include
option path '/etc/firewall.user'
config forwarding
option dest 'wan'
option src 'lan'
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd9d:f95b:1023::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.1'
option gateway '192.168.1.1'
option broadcast '192.168.1.255'
config device 'lan_dev'
option name 'eth0.1'
option macaddr 'REMOVED'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 6t'
config interface 'wwan'
option proto 'dhcp'
/etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:00.0/0000:01:00.0'
option htmode 'HT20'
option country 'NZ'
option legacy_rates '1'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:01.0/0000:02:00.0'
option htmode 'VHT80'
option disabled '0'
option channel '60'
option legacy_rates '1'
option country 'NZ'
config wifi-iface
option network 'wwan'
option ssid 'REMOVED'
option device 'radio1'
option mode 'sta'
option bssid 'REMOVED'
option encryption 'wpa2'
option eap_type 'peap'
option auth 'EAP-MSCHAPV2'
option identity 'REMOVED'
option password 'REMOVED'
config wifi-iface
option device 'radio0'
option mode 'ap'
option ssid 'z'
option network 'lan'
option macfilter 'allow'
option encryption 'psk2'
option key 'REMOVED'
list maclist 'REMOVED'
list maclist 'REMOVED'
list maclist 'REMOVED'
list maclist 'REMOVED'
Hopefully someone can point out where I'm going wrong...
If you need any more info just ask!
Thanks,
Zach