rtemp
August 6, 2019, 12:34pm
1
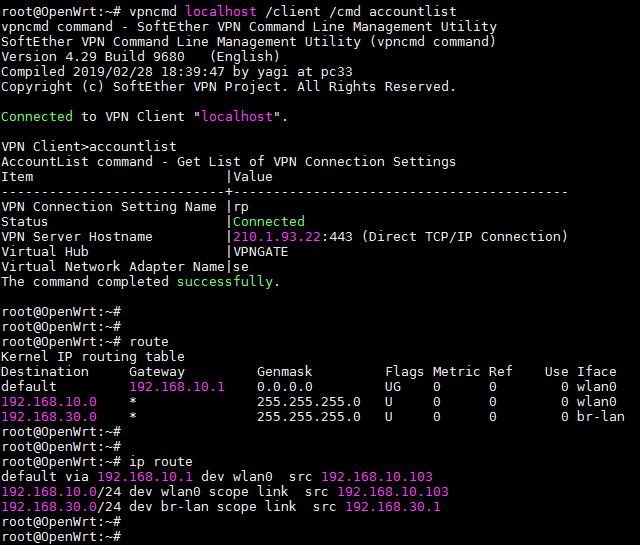
Friends, I got a Xiaomi and RPi both at the current FW level of OpenWrt. I tested each as my VPN router, successfully installed and set-up the SE vpn client and was able to connect to a VPN server. However, my VPN connection disconnects after the virtual network is defined in the interface (DHCP client) and after it gets an IP and then the internet connection also disconnects. Internet would come back after disabling the interface and then reboot. I get the same result on both devices. There must be something I'm missing in the setup process. Kindly help.
My interface config is something like this:
Search the settings for an option to disable the default gateway modification or to change the method the routes are added to achieve something like this:
rtemp
August 7, 2019, 5:42pm
4
Check from the router:
nslookup example.org 8.8.8.8
ip a; ip r; ip ru; iptables-save
rtemp
August 9, 2019, 8:29am
6
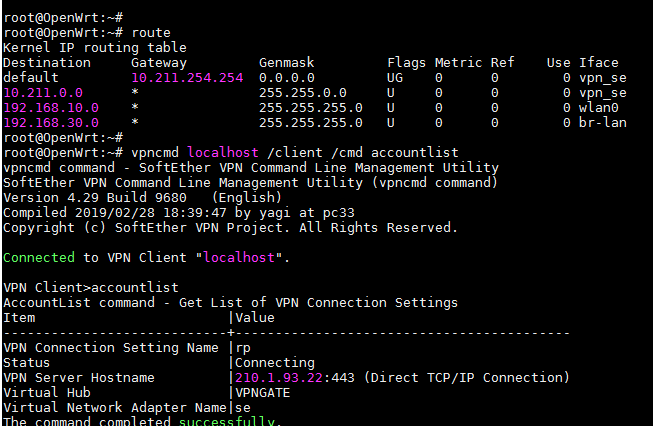
Sorry for the late reply. Here's the output of those commands. Kindly help me check and find out what is wrong with it. I can ping web sites from my openwrt with VPN enabled but I can't reach those with my PC.
# VPN Enabled:
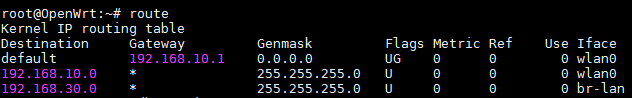
root@OpenWrt:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 10.211.254.254 0.0.0.0 UG 0 0 0 vpn_se
10.211.0.0 * 255.255.0.0 U 0 0 0 vpn_se
153.145.39.90 192.168.10.1 255.255.255.255 UGH 0 0 0 wlan0-1
192.168.10.0 * 255.255.255.0 U 0 0 0 wlan0-1
192.168.30.0 * 255.255.255.0 U 0 0 0 br-lan
root@OpenWrt:~#
root@OpenWrt:~#
root@OpenWrt:~# nslookup openwrt.org 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
Name: openwrt.org
Address 1: 139.59.209.225
Address 2: 2a03:b0c0:3:d0::1af1:1
root@OpenWrt:~#
root@OpenWrt:~#
root@OpenWrt:~# ip a; ip r; ip ru; iptables-save
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UP qlen 1000
link/ether 00:27:84:b8:9c:00 brd ff:ff:ff:ff:ff:ff
6: vpn_se: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 1000
link/ether 5e:11:7b:9a:ee:e1 brd ff:ff:ff:ff:ff:ff
inet 10.211.2.92/16 brd 10.211.255.255 scope global vpn_se
valid_lft forever preferred_lft forever
inet6 fe80::5c11:7bff:fe9a:eee1/64 scope link
valid_lft forever preferred_lft forever
15: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:27:84:b8:9c:00 brd ff:ff:ff:ff:ff:ff
inet 192.168.30.1/24 brd 192.168.30.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fdea:66d9:a24::1/60 scope global
valid_lft forever preferred_lft forever
inet6 fe80::ba27:ebff:fe84:bfa5/64 scope link
valid_lft forever preferred_lft forever
16: wlan0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:0f:00:52:4c:1c brd ff:ff:ff:ff:ff:ff
17: wlan0-1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 52:00:1d:0f:38:92 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.104/24 brd 192.168.10.255 scope global wlan0-1
valid_lft forever preferred_lft forever
inet6 fe80::20f:ff:fe52:4c1d/64 scope link
valid_lft forever preferred_lft forever
default via 10.211.254.254 dev vpn_se src 10.211.2.92
10.211.0.0/16 dev vpn_se scope link src 10.211.2.92
153.145.39.90 via 192.168.10.1 dev wlan0-1
192.168.10.0/24 dev wlan0-1 scope link src 192.168.10.104
192.168.30.0/24 dev br-lan scope link src 192.168.30.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
# Generated by iptables-save v1.6.2 on Fri Aug 9 08:10:33 2019
*nat
:PREROUTING ACCEPT [17:3467]
:INPUT ACCEPT [8:2437]
:OUTPUT ACCEPT [13:1168]
:POSTROUTING ACCEPT [19:1357]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i vpn_se -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i wlan0-1 -m comment --comment "!fw3" -j zone_wan_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o vpn_se -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o wlan0-1 -m comment --comment "!fw3" -j zone_wan_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Fri Aug 9 08:10:33 2019
# Generated by iptables-save v1.6.2 on Fri Aug 9 08:10:33 2019
*mangle
:PREROUTING ACCEPT [3165:1309130]
:INPUT ACCEPT [3141:1307296]
:FORWARD ACCEPT [24:1834]
:OUTPUT ACCEPT [1186:108478]
:POSTROUTING ACCEPT [1192:107750]
-A FORWARD -o wlan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o wlan0-1 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Fri Aug 9 08:10:33 2019
# Generated by iptables-save v1.6.2 on Fri Aug 9 08:10:33 2019
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i vpn_se -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wlan0 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i wlan0-1 -m comment --comment "!fw3" -j zone_wan_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i vpn_se -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wlan0 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i wlan0-1 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o vpn_se -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wlan0 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o wlan0-1 -m comment --comment "!fw3" -j zone_wan_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_ACCEPT -o vpn_se -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_src_ACCEPT -i vpn_se -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o wlan0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wlan0 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o wlan0-1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wlan0-1 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_dest_REJECT -o wlan0-1 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_src_REJECT -i wlan0-1 -m comment --comment "!fw3" -j reject
COMMIT
Change the firewall zone of the VPN interface from lan to wan.
rtemp
August 11, 2019, 6:53am
8
Thanks. But but it didn't work either. I have followed all tutorials that I could find on the net but none worked. Maybe this isn't for me.
Let's check the updated diagnostics:
nslookup example.org 8.8.8.8
ping -c 3 example.org
traceroute example.org
ip a; ip r; ip ru; iptables-save
rtemp
August 11, 2019, 7:56am
10
Here we go.
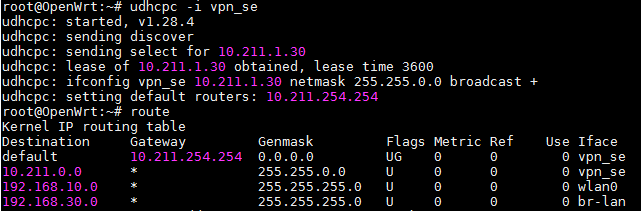
root@OpenWrt:/tmp# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 10.211.254.254 0.0.0.0 UG 0 0 0 vpn_se
10.211.0.0 * 255.255.0.0 U 0 0 0 vpn_se
153.145.39.90 192.168.10.1 255.255.255.255 UGH 0 0 0 wlan0
192.168.10.0 * 255.255.255.0 U 0 0 0 wlan0
192.168.30.0 * 255.255.255.0 U 0 0 0 br-lan
root@OpenWrt:/tmp#
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# nslookup openwrt.org 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
Name: openwrt.org
Address 1: 139.59.209.225
Address 2: 2a03:b0c0:3:d0::1af1:1
root@OpenWrt:/tmp#
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# ping -c 3 openwrt.org
PING openwrt.org (139.59.209.225): 56 data bytes
64 bytes from 139.59.209.225: seq=0 ttl=43 time=7057.367 ms
64 bytes from 139.59.209.225: seq=1 ttl=43 time=6055.830 ms
64 bytes from 139.59.209.225: seq=2 ttl=43 time=9278.647 ms
--- openwrt.org ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 6055.830/7463.948/9278.647 ms
root@OpenWrt:/tmp#
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# traceroute openwrt.org
traceroute to openwrt.org (139.59.209.225), 30 hops max, 38 byte packets
1 * * *
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
root@OpenWrt:/tmp# traceroute -i vpn_se openwrt.org
traceroute to openwrt.org (139.59.209.225), 30 hops max, 38 byte packets
1 * * *
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
root@OpenWrt:/tmp# traceroute -i wlan0 openwrt.org
traceroute to openwrt.org (139.59.209.225), 30 hops max, 38 byte packets
1 192.168.10.103 (192.168.10.103) 3128.573 ms !H 3118.566 ms !H 3119.170 ms !H
root@OpenWrt:/tmp#
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UP qlen 1000
link/ether b8:27:eb:84:bf:a5 brd ff:ff:ff:ff:ff:ff
4: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether b8:27:eb:84:bf:a5 brd ff:ff:ff:ff:ff:ff
inet 192.168.30.1/24 brd 192.168.30.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fdea:66d9:a24::1/60 scope global
valid_lft forever preferred_lft forever
inet6 fe80::ba27:ebff:fe84:bfa5/64 scope link
valid_lft forever preferred_lft forever
5: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:1c:df:9f:e3:22 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.103/24 brd 192.168.10.255 scope global wlan0
valid_lft forever preferred_lft forever
inet6 fe80::21c:dfff:fe9f:e322/64 scope link
valid_lft forever preferred_lft forever
8: vpn_se: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 1000
link/ether 5e:1a:90:60:cd:22 brd ff:ff:ff:ff:ff:ff
inet 10.211.1.12/16 brd 10.211.255.255 scope global vpn_se
valid_lft forever preferred_lft forever
inet6 fe80::5c1a:90ff:fe60:cd22/64 scope link
valid_lft forever preferred_lft forever
root@OpenWrt:/tmp#
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# ip r
default via 10.211.254.254 dev vpn_se src 10.211.1.12
10.211.0.0/16 dev vpn_se scope link src 10.211.1.12
153.145.39.90 via 192.168.10.1 dev wlan0
192.168.10.0/24 dev wlan0 scope link src 192.168.10.103
192.168.30.0/24 dev br-lan scope link src 192.168.30.1
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# ip ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
root@OpenWrt:/tmp#
root@OpenWrt:/tmp#
root@OpenWrt:/tmp# iptables-save
Generated by iptables-save v1.6.2 on Sun Aug 11 07:50:31 2019
*nat
:PREROUTING ACCEPT [250:52259]
:INPUT ACCEPT [130:39044]
:OUTPUT ACCEPT [226:10082]
:POSTROUTING ACCEPT [273:11692]
:postrouting_lan_rule - [0:0]
:postrouting_ovpn_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_ovpn_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_ovpn_postrouting - [0:0]
:zone_ovpn_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i vpn_se -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i tun0 -m comment --comment "!fw3" -j zone_ovpn_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o vpn_se -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o tun0 -m comment --comment "!fw3" -j zone_ovpn_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_ovpn_postrouting -m comment --comment "!fw3: Custom ovpn postrouting rule chain" -j postrouting_ovpn_rule
-A zone_ovpn_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_ovpn_prerouting -m comment --comment "!fw3: Custom ovpn prerouting rule chain" -j prerouting_ovpn_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
Completed on Sun Aug 11 07:50:31 2019
Generated by iptables-save v1.6.2 on Sun Aug 11 07:50:31 2019
*mangle
:PREROUTING ACCEPT [56947:19611933]
:INPUT ACCEPT [54196:19112649]
:FORWARD ACCEPT [2707:490748]
:OUTPUT ACCEPT [6237:1169413]
:POSTROUTING ACCEPT [8880:1654895]
:RRDIPT_FORWARD - [0:0]
:RRDIPT_INPUT - [0:0]
:RRDIPT_OUTPUT - [0:0]
-A INPUT -j RRDIPT_INPUT
-A FORWARD -j RRDIPT_FORWARD
-A FORWARD -o wlan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone ovpn MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A OUTPUT -j RRDIPT_OUTPUT
-A RRDIPT_FORWARD -s 192.168.10.1/32 -j RETURN
-A RRDIPT_FORWARD -d 192.168.10.1/32 -j RETURN
-A RRDIPT_FORWARD -s 192.168.30.229/32 -j RETURN
-A RRDIPT_FORWARD -d 192.168.30.229/32 -j RETURN
-A RRDIPT_INPUT -i eth0 -j RETURN
-A RRDIPT_INPUT -i tun0 -j RETURN
-A RRDIPT_INPUT -i wlan0 -j RETURN
-A RRDIPT_OUTPUT -o eth0 -j RETURN
-A RRDIPT_OUTPUT -o tun0 -j RETURN
-A RRDIPT_OUTPUT -o wlan0 -j RETURN
COMMIT
Completed on Sun Aug 11 07:50:31 2019
Generated by iptables-save v1.6.2 on Sun Aug 11 07:50:31 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_ovpn_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_ovpn_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_ovpn_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_REJECT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_ovpn_dest_ACCEPT - [0:0]
:zone_ovpn_dest_REJECT - [0:0]
:zone_ovpn_forward - [0:0]
:zone_ovpn_input - [0:0]
:zone_ovpn_output - [0:0]
:zone_ovpn_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i vpn_se -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wlan0 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i tun0 -m comment --comment "!fw3" -j zone_ovpn_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i vpn_se -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wlan0 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_ovpn_forward
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o vpn_se -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wlan0 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_ovpn_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_ACCEPT -o vpn_se -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
-A zone_lan_dest_REJECT -o vpn_se -m comment --comment "!fw3" -j reject
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to ovpn forwarding policy" -j zone_ovpn_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_REJECT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_src_ACCEPT -i vpn_se -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_ovpn_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_ovpn_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
-A zone_ovpn_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
-A zone_ovpn_forward -m comment --comment "!fw3: Custom ovpn forwarding rule chain" -j forwarding_ovpn_rule
-A zone_ovpn_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_ovpn_forward -m comment --comment "!fw3" -j zone_ovpn_dest_REJECT
-A zone_ovpn_input -m comment --comment "!fw3: Custom ovpn input rule chain" -j input_ovpn_rule
-A zone_ovpn_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_ovpn_input -m comment --comment "!fw3" -j zone_ovpn_src_REJECT
-A zone_ovpn_output -m comment --comment "!fw3: Custom ovpn output rule chain" -j output_ovpn_rule
-A zone_ovpn_output -m comment --comment "!fw3" -j zone_ovpn_dest_ACCEPT
-A zone_ovpn_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
-A zone_wan_dest_ACCEPT -o wlan0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wlan0 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j DROP
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i wlan0 -m comment --comment "!fw3" -j reject
COMMIT
Completed on Sun Aug 11 07:50:31 2019
root@OpenWrt:/tmp#
rtemp
August 11, 2019, 8:10am
12
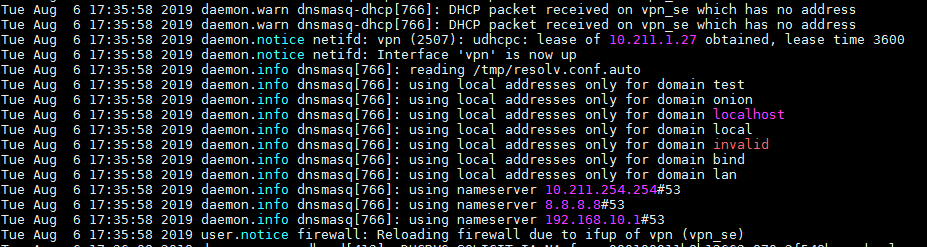
I'm also getting this error when the vpn (vpn_se) interface becomes active.
It's just a warning and has nothing to do with your issue.
It seems the VPN provider performs traffic filtering, but it is not critical.
The VPN interface is still in the lan zone.wan.
rtemp
August 11, 2019, 8:31am
14
firewall zone to wan:
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# nslookup openwrt.org 8.8.8.8
Server: 8.8.8.8
Address: 8.8.8.8#53
Name: openwrt.org
Address 1: 139.59.209.225
Address 2: 2a03:b0c0:3:d0::1af1:1
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# ping -c 3 openwrt.org
PING openwrt.org (139.59.209.225): 56 data bytes
64 bytes from 139.59.209.225: seq=0 ttl=43 time=3704.529 ms
64 bytes from 139.59.209.225: seq=1 ttl=43 time=2703.400 ms
64 bytes from 139.59.209.225: seq=2 ttl=43 time=4588.410 ms
--- openwrt.org ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 2703.400/3665.446/4588.410 ms
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# traceroute openwrt.org
traceroute to openwrt.org (139.59.209.225), 30 hops max, 38 byte packets
1 * * *
2 * * *
3 * * *
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UP qlen 1000
link/ether b8:27:eb:84:bf:a5 brd ff:ff:ff:ff:ff:ff
8: vpn_se: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 1000
link/ether 5e:1a:90:60:cd:22 brd ff:ff:ff:ff:ff:ff
inet 10.211.1.12/16 brd 10.211.255.255 scope global vpn_se
valid_lft forever preferred_lft forever
inet6 fe80::5c1a:90ff:fe60:cd22/64 scope link
valid_lft forever preferred_lft forever
10: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether b8:27:eb:84:bf:a5 brd ff:ff:ff:ff:ff:ff
inet 192.168.30.1/24 brd 192.168.30.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fdea:66d9:a24::1/60 scope global
valid_lft forever preferred_lft forever
inet6 fe80::ba27:ebff:fe84:bfa5/64 scope link
valid_lft forever preferred_lft forever
11: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:1c:df:9f:e3:22 brd ff:ff:ff:ff:ff:ff
inet 192.168.10.103/24 brd 192.168.10.255 scope global wlan0
valid_lft forever preferred_lft forever
inet6 fe80::21c:dfff:fe9f:e322/64 scope link
valid_lft forever preferred_lft forever
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# ip r
default via 10.211.254.254 dev vpn_se
default via 10.211.254.254 dev vpn_se src 10.211.1.12
10.211.0.0/16 dev vpn_se scope link src 10.211.1.12
153.145.39.90 via 192.168.10.1 dev wlan0
192.168.10.0/24 dev wlan0 scope link src 192.168.10.103
192.168.30.0/24 dev br-lan scope link src 192.168.30.1
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# ip ru
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config#
root@OpenWrt:/etc/config# iptables-save
# Generated by iptables-save v1.6.2 on Sun Aug 11 08:27:48 2019
*nat
:PREROUTING ACCEPT [6997:2155049]
:INPUT ACCEPT [1:328]
:OUTPUT ACCEPT [118:5373]
:POSTROUTING ACCEPT [6:378]
:postrouting_lan_rule - [0:0]
:postrouting_ovpn_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_ovpn_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_ovpn_postrouting - [0:0]
:zone_ovpn_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i vpn_se -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i tun0 -m comment --comment "!fw3" -j zone_ovpn_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o vpn_se -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o tun0 -m comment --comment "!fw3" -j zone_ovpn_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_ovpn_postrouting -m comment --comment "!fw3: Custom ovpn postrouting rule chain" -j postrouting_ovpn_rule
-A zone_ovpn_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_ovpn_prerouting -m comment --comment "!fw3: Custom ovpn prerouting rule chain" -j prerouting_ovpn_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sun Aug 11 08:27:48 2019
# Generated by iptables-save v1.6.2 on Sun Aug 11 08:27:48 2019
*mangle
:PREROUTING ACCEPT [34603:12589049]
:INPUT ACCEPT [33789:12353084]
:FORWARD ACCEPT [790:231309]
:OUTPUT ACCEPT [3791:818527]
:POSTROUTING ACCEPT [4565:1049196]
:RRDIPT_FORWARD - [0:0]
:RRDIPT_INPUT - [0:0]
:RRDIPT_OUTPUT - [0:0]
-A INPUT -j RRDIPT_INPUT
-A FORWARD -j RRDIPT_FORWARD
-A FORWARD -o wlan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o vpn_se -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone ovpn MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A OUTPUT -j RRDIPT_OUTPUT
-A RRDIPT_FORWARD -s 192.168.10.1/32 -j RETURN
-A RRDIPT_FORWARD -d 192.168.10.1/32 -j RETURN
-A RRDIPT_FORWARD -s 192.168.30.229/32 -j RETURN
-A RRDIPT_FORWARD -d 192.168.30.229/32 -j RETURN
-A RRDIPT_INPUT -i eth0 -j RETURN
-A RRDIPT_INPUT -i tun0 -j RETURN
-A RRDIPT_INPUT -i wlan0 -j RETURN
-A RRDIPT_OUTPUT -o eth0 -j RETURN
-A RRDIPT_OUTPUT -o tun0 -j RETURN
-A RRDIPT_OUTPUT -o wlan0 -j RETURN
COMMIT
# Completed on Sun Aug 11 08:27:48 2019
# Generated by iptables-save v1.6.2 on Sun Aug 11 08:27:48 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_ovpn_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_ovpn_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_ovpn_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_REJECT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_ovpn_dest_ACCEPT - [0:0]
:zone_ovpn_dest_REJECT - [0:0]
:zone_ovpn_forward - [0:0]
:zone_ovpn_input - [0:0]
:zone_ovpn_output - [0:0]
:zone_ovpn_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wlan0 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i vpn_se -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i tun0 -m comment --comment "!fw3" -j zone_ovpn_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wlan0 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i vpn_se -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_ovpn_forward
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wlan0 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o vpn_se -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_ovpn_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to ovpn forwarding policy" -j zone_ovpn_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_REJECT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_ovpn_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_ovpn_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
-A zone_ovpn_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
-A zone_ovpn_forward -m comment --comment "!fw3: Custom ovpn forwarding rule chain" -j forwarding_ovpn_rule
-A zone_ovpn_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_ovpn_forward -m comment --comment "!fw3" -j zone_ovpn_dest_REJECT
-A zone_ovpn_input -m comment --comment "!fw3: Custom ovpn input rule chain" -j input_ovpn_rule
-A zone_ovpn_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_ovpn_input -m comment --comment "!fw3" -j zone_ovpn_src_REJECT
-A zone_ovpn_output -m comment --comment "!fw3: Custom ovpn output rule chain" -j output_ovpn_rule
-A zone_ovpn_output -m comment --comment "!fw3" -j zone_ovpn_dest_ACCEPT
-A zone_ovpn_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
-A zone_wan_dest_ACCEPT -o wlan0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wlan0 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o vpn_se -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o vpn_se -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_dest_REJECT -o vpn_se -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j DROP
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_src_REJECT -i vpn_se -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sun Aug 11 08:27:48 2019
root@OpenWrt:/etc/config#
Okay, now we have the MASQUERADE as well as working ping and nslookup.
The next step is to perform the testing from the PC.
rtemp
August 11, 2019, 9:08am
16
Hi vgaetera, I got it to work. I copied the firewall settings of openvpn. Now it's working. My problem before was the clients can't connect to the internet when vpn_se is active.
Here's my firewall setting.
firewall.@zone[2]=zone
firewall.@zone[2].name='ovpn'
firewall.@zone[2].forward='REJECT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].input='REJECT'
firewall.@zone[2].masq='1'
firewall.@zone[2].mtu_fix='1'
firewall.@zone[2].network='ovpn'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].dest='ovpn'
firewall.@forwarding[1].src='lan'
firewall.@zone[3]=zone
firewall.@zone[3].name='vpnse'
firewall.@zone[3].output='ACCEPT'
firewall.@zone[3].network='vpnse'
firewall.@zone[3].input='REJECT'
firewall.@zone[3].forward='REJECT'
firewall.@zone[3].masq='1'
firewall.@zone[3].mtu_fix='1'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].dest='vpnse'
firewall.@forwarding[2].src='lan'
rtemp
August 11, 2019, 9:32am
17
root@OpenWrt:~#
root@OpenWrt:~# iptables-save
# Generated by iptables-save v1.6.2 on Sun Aug 11 09:32:32 2019
*nat
:PREROUTING ACCEPT [344:77547]
:INPUT ACCEPT [5:300]
:OUTPUT ACCEPT [88:6553]
:POSTROUTING ACCEPT [6:408]
:postrouting_lan_rule - [0:0]
:postrouting_ovpn_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_vpnse_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_ovpn_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_vpnse_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_ovpn_postrouting - [0:0]
:zone_ovpn_prerouting - [0:0]
:zone_vpnse_postrouting - [0:0]
:zone_vpnse_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i tun0 -m comment --comment "!fw3" -j zone_ovpn_prerouting
-A PREROUTING -i vpn_se -m comment --comment "!fw3" -j zone_vpnse_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o tun0 -m comment --comment "!fw3" -j zone_ovpn_postrouting
-A POSTROUTING -o vpn_se -m comment --comment "!fw3" -j zone_vpnse_postrouting
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_ovpn_postrouting -m comment --comment "!fw3: Custom ovpn postrouting rule chain" -j postrouting_ovpn_rule
-A zone_ovpn_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_ovpn_prerouting -m comment --comment "!fw3: Custom ovpn prerouting rule chain" -j prerouting_ovpn_rule
-A zone_vpnse_postrouting -m comment --comment "!fw3: Custom vpnse postrouting rule chain" -j postrouting_vpnse_rule
-A zone_vpnse_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_vpnse_prerouting -m comment --comment "!fw3: Custom vpnse prerouting rule chain" -j prerouting_vpnse_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Sun Aug 11 09:32:32 2019
# Generated by iptables-save v1.6.2 on Sun Aug 11 09:32:32 2019
*mangle
:PREROUTING ACCEPT [19995:7362192]
:INPUT ACCEPT [8519:3046516]
:FORWARD ACCEPT [11436:4308108]
:OUTPUT ACCEPT [4492:902979]
:POSTROUTING ACCEPT [15912:5209459]
:RRDIPT_FORWARD - [0:0]
:RRDIPT_INPUT - [0:0]
:RRDIPT_OUTPUT - [0:0]
-A INPUT -j RRDIPT_INPUT
-A FORWARD -j RRDIPT_FORWARD
-A FORWARD -o wlan0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone ovpn MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o vpn_se -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone vpnse MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A OUTPUT -j RRDIPT_OUTPUT
-A RRDIPT_INPUT -i eth0 -j RETURN
-A RRDIPT_OUTPUT -o eth0 -j RETURN
COMMIT
# Completed on Sun Aug 11 09:32:32 2019
# Generated by iptables-save v1.6.2 on Sun Aug 11 09:32:32 2019
*filter
:INPUT DROP [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_ovpn_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_vpnse_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_ovpn_rule - [0:0]
:input_rule - [0:0]
:input_vpnse_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_ovpn_rule - [0:0]
:output_rule - [0:0]
:output_vpnse_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_dest_REJECT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_ovpn_dest_ACCEPT - [0:0]
:zone_ovpn_dest_REJECT - [0:0]
:zone_ovpn_forward - [0:0]
:zone_ovpn_input - [0:0]
:zone_ovpn_output - [0:0]
:zone_ovpn_src_REJECT - [0:0]
:zone_vpnse_dest_ACCEPT - [0:0]
:zone_vpnse_dest_REJECT - [0:0]
:zone_vpnse_forward - [0:0]
:zone_vpnse_input - [0:0]
:zone_vpnse_output - [0:0]
:zone_vpnse_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i wlan0 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i tun0 -m comment --comment "!fw3" -j zone_ovpn_input
-A INPUT -i vpn_se -m comment --comment "!fw3" -j zone_vpnse_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i wlan0 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_ovpn_forward
-A FORWARD -i vpn_se -m comment --comment "!fw3" -j zone_vpnse_forward
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o wlan0 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_ovpn_output
-A OUTPUT -o vpn_se -m comment --comment "!fw3" -j zone_vpnse_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_dest_REJECT -o br-lan -m comment --comment "!fw3" -j reject
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to ovpn forwarding policy" -j zone_ovpn_dest_ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to vpnse forwarding policy" -j zone_vpnse_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_REJECT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_ovpn_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_ovpn_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
-A zone_ovpn_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
-A zone_ovpn_forward -m comment --comment "!fw3: Custom ovpn forwarding rule chain" -j forwarding_ovpn_rule
-A zone_ovpn_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_ovpn_forward -m comment --comment "!fw3" -j zone_ovpn_dest_REJECT
-A zone_ovpn_input -m comment --comment "!fw3: Custom ovpn input rule chain" -j input_ovpn_rule
-A zone_ovpn_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_ovpn_input -m comment --comment "!fw3" -j zone_ovpn_src_REJECT
-A zone_ovpn_output -m comment --comment "!fw3: Custom ovpn output rule chain" -j output_ovpn_rule
-A zone_ovpn_output -m comment --comment "!fw3" -j zone_ovpn_dest_ACCEPT
-A zone_ovpn_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
-A zone_vpnse_dest_ACCEPT -o vpn_se -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_vpnse_dest_ACCEPT -o vpn_se -m comment --comment "!fw3" -j ACCEPT
-A zone_vpnse_dest_REJECT -o vpn_se -m comment --comment "!fw3" -j reject
-A zone_vpnse_forward -m comment --comment "!fw3: Custom vpnse forwarding rule chain" -j forwarding_vpnse_rule
-A zone_vpnse_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_vpnse_forward -m comment --comment "!fw3" -j zone_vpnse_dest_REJECT
-A zone_vpnse_input -m comment --comment "!fw3: Custom vpnse input rule chain" -j input_vpnse_rule
-A zone_vpnse_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_vpnse_input -m comment --comment "!fw3" -j zone_vpnse_src_REJECT
-A zone_vpnse_output -m comment --comment "!fw3: Custom vpnse output rule chain" -j output_vpnse_rule
-A zone_vpnse_output -m comment --comment "!fw3" -j zone_vpnse_dest_ACCEPT
-A zone_vpnse_src_REJECT -i vpn_se -m comment --comment "!fw3" -j reject
-A zone_wan_dest_ACCEPT -o wlan0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o wlan0 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o wlan0 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j DROP
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i wlan0 -m comment --comment "!fw3" -j reject
COMMIT
system
August 21, 2019, 9:32am
18
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.