Hi. I am trying to achieve the same as you. I have a working router and working vpn connection. But i can not achiece forwarding to the tunnel. I can not even see anything in the web interface about fortivpn. Could you please explain what you see in it, or some more things about what you did? Thank you!
@ibravos - Your post has no details by which to recommend solutions... let's get some basic info:
- What VPN protocol are you using?
- And what are you connecting to (i.e. a commercial VPN service, to an office, or a road-warrior type setup)?
- Do you have any indication of the VPN connection status?
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
P.S. I'll probably also move your post to a new thread so that we can concentrate on your specific issue.
Thank you very much for the immediate reply
I am a sysadmin at a small company. Our users have to use the services of another company, provided through Forti VPN, which is configured to disallow split tunneling. Our users need internet access also, so we have deployed Windows VMs in every user, with the VPN running in the VMs along with the apps provided by this third company. This solution is full of problems and slow, so i try to implement a VPN gateway, to get rid of the VMs.
So, i installed latest OpenWRT in a VirtualBox VM, following the excellent guide provided by OpenWRT. Everything worked as expected and i was able to use the VM as a gateway for internet (this was just for testing). Then, i installed openfortivpn and i was able to connect to the VPN, but i lost the gateway functionality. As far as i understand now, i have to implement the forwarding of LAN packets to the ppp tunnel.
Then i installed the luci-proto-openfortivpn package, hoping that it will help me do the configuration, as described in the thread "Enable NAT for VPN Client". This is where i don't understand what's happening. I expected to see some changes in the web interface, an entry for openfortivpn or something but no. So i don't know if i did something wrong, if i'm missing something or if there is a problem with this package.
To sum up, the question is if and how i can configure OpenWRT as a Forti VPN gateway and what should i expect from luci-proto-openfortivpn package.
I will send the output of the commands you sent as soon as i get back to my work pc.
Thank you!
With OpenWrt as your main network router/gateway, you should be able to achieve this by using Policy Based Routing.
I don't think this requires PBR, it should work with conventional destination based routing. Route corporate LANs into the VPN tunnel and default route to the regular Internet.
Split tunneling is a security risk but most situations that don't allow it should still provide firewalled and restricted Internet access through the VPN.
Thank you both for the replies. I think i confused you. What i want is FULL tunneling of my LAN traffic through the VPN. At the moment no LAN traffic goes through the VPN. The poster of "Enable NAT for VPN Client" had the same problem and solved it just by using luci-proto-openfortvpn package, which i have difficulties to use. Also someone replied to him that he can add the VPN to a zone and allow traffic from LAN zone to VPN zone (and the reverse) in the firewall. I tried this and still no access to the VPN from the LAN. Maybe i need to add some routes also? But i would like to find out how to do this easily with the luci-proto-openfortivpn package. Maybe try older versions of OpenWrt and the package?
In order to symmetric route a LAN into a VPN, there must be a route back to your LAN installed on the other side. Corporate VPNs expect the user to be a road warrior, that is a laptop or phone holding a single IP assigned on the VPN tunnel-- not a router with a LAN behind it.
Thus you must NAT your LAN into the VPN so it appears to that side to be coming from the single IP that the VPN server has assigned to you.
The simplest way to do this in OpenWrt is to place the VPN tunnel device or network into the wan firewall zone. This zone by default has IPv4 NAT enabled.
Thank you very much, good explanation. I will try this as soon as i get back to work.
Hello! When connected to the VPN, I can see the ppp0 device in Luci. But i cant find a way to add the device or the VPN network to the WAN zone through Luci.. I guess i have to do it through command line?
Network-->Firewall, at the bottom of the page click on Edit button for wan. Click on Advanced tab. Pull down "Covered Devices" list. If ppp0 is not there click the blank space at the bottom of the list and type ppp0 and press Enter.
Thank you very much for the reply. I tried that when the tunnel was up and it didn't work. Probably i messed up something else. Now the tunnel is down and adding ppp0 by typing is not working. But i accidentally found another method in the guide "OpenVPN client using LuCI" (chapter 4. Firewall) and i am going to try now. I ll let you know for the result. Thanks!
Hello again. I switched to openvpn because it is easier for me to test the setup. My requirements are the same: forward all LAN traffic to the tunnel. I run latest OpenWrt on VirtualBox and i have 3 interfaces, LAN, WAN and MNG.
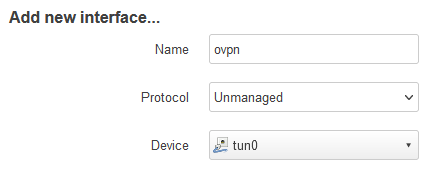
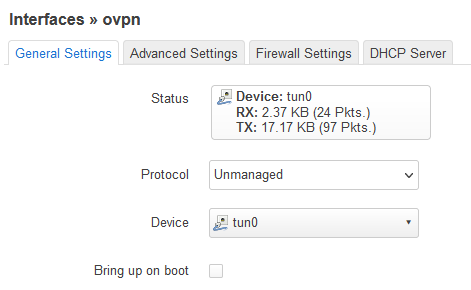
So, i added the tunnel to the WAN firewall zone by creating a new interface for the tun0 device:
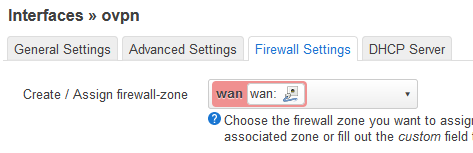
Then, this is what i see in the wan firewall zone settings:
After that i rebooted OpenWrt. It didn't work: i tried to reach an IP in the remote server from a LAN client and got nothing, no connectivity. Whereas if i disconnect from the VPN, my LAN client is able to use OpenWrt as a gatway and get out to the internet. Any help is very appreciated. Thank you for your time.