hi everybody I've created a script recently that allows you to identify the list of servers during matchmaking for example in call of duty and then block them in the firewall or authorize only a few.
insert the script in your root/
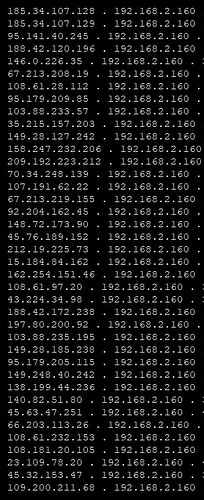
copy the address of your console instead of my ip which is 2.160
then launch your game wait for the online service connection then 15 seconds later you will see your server list
#!/bin/sh
############################################################
ipconsole={192.168.2.160} # ajoute ta console
#port={3074}
nft add table inet dopam # autorise
nft flush table inet dopam # nettoie les regles
nft -f /dev/stdin <<EOF
table inet dopam {
### change pour choisir ce que tu veux
set udp_meter4 {typeof ip saddr . ip daddr . udp sport . udp dport
timeout 5m
}
chain dopam {
type filter hook forward priority 0; policy accept;
#udp sport $port
#udp dport $port
ip protocol udp ip daddr $ipconsole
ip protocol udp ip saddr $ipconsole
#choisi ton protocole pour ce que tu veux
ip protocol udp ip daddr $ipconsole add @udp_meter4 {ip saddr . ip daddr . udp sport . udp dport}
#ip protocol udp udp sport $port add @udp_meter4 {ip saddr . ip daddr . udp sport . udp dport}
}
}
EOF
#### lancer la commande nft list ruleset
#### lancer la commande nft list ruleset
### Init Script ###
## Check if the file does not exist
if [ ! -f "/etc/init.d/DOPAMSERVER" ]; then
cat << "INITSCRIPT" > /etc/init.d/DOPAMSERVER
#!/bin/sh /etc/rc.common
USE_PROCD=1
START=99
STOP=99
service_triggers() {
procd_add_reload_trigger firewall
}
start_service() {
/etc/init.d/DOPAMSERVER enabled || exit 0
echo start
procd_open_instance
procd_set_param command /bin/sh "/root/DOPAMSERVER.sh"
procd_set_param stdout 1
procd_set_param stderr 1
procd_close_instance
}
restart() {
/etc/init.d/DOPAMSERVER enabled || exit 0
echo restart
/root/DOPAMSERVER.sh
}
stop_service() {
echo stop
############################################################
## Default warning settings
uci -q get dhcp.odhcpd.loglevel | grep "4" > /dev/null 2>&1 || {
uci set dhcp.odhcpd.loglevel="4"
uci commit && reload_config
}
############################################################
############################################################
exit 0
}
reload_service() {
start
}
INITSCRIPT
chmod 755 /etc/init.d/DOPAMSERVER > /dev/null 2>&1
/etc/init.d/DOPAMSERVER enable > /dev/null 2>&1
fi
############################################################
### Hotplug ###
## Check if the file does not exist
if [ ! -f "/etc/hotplug.d/iface/99-DOPAMSERVER" ]; then
cat << "HOTPLUG" > /etc/hotplug.d/iface/99-DOPAMSERVER
#!/bin/sh
[ "$ACTION" = ifup ] || [ "$ACTION" = ifupdate ] || exit 0
[ "$ACTION" = ifupdate ] && [ -z "$IFUPDATE_ADDRESSES" ] && [ -z "$IFUPDATE_DATA" ] && exit 0
# Ensure that the script is executable by Owner
if [ ! -x "/root/DOPAMSERVER.sh" ] || [ ! -x "/etc/init.d/DOPAMSERVER" ]; then
chmod 755 /root/DOPAMSERVER.sh
chmod 755 /etc/init.d/DOPAMSERVER
fi
# Check if the init script is enabled to reload the script
/etc/init.d/DOPAMSERVER enabled || exit 0
# Reloading the script
logger -t DOPAMSERVER "Reloading DOPAMSERVER.sh due to $ACTION of $INTERFACE ($DEVICE)"
sleep 10 && /etc/init.d/DOPAMSERVER restart
HOTPLUG
fi
I just can't seem to remove the dopam rules once the script has been run.
if @dlakelan has an idea I think it's in echo stop just after
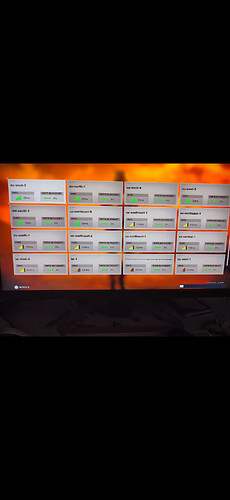
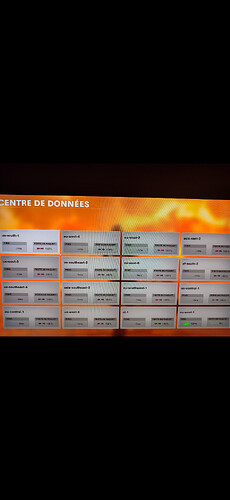
normally you can found the rules here like this in firewall
IPv4/IPv6 traffic table "dopam"
Traffic filter chain "dopam"
Hook: forward (Capture incoming packets addressed to other hosts), Priority: 0
Policy: accept (Continue processing unmatched packets)
Rule matches Rule actions
IP protocol is udpDestination IP is 192.168.2.160
IP protocol is udpSource IP is 192.168.2.160
IP protocol is udpDestination IP is 192.168.2.160{ set }