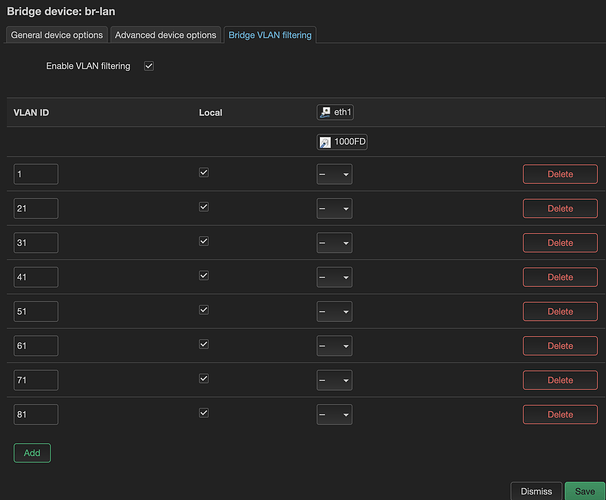
So are you saying that the other VLANs are used on other devices downstream of this router (i.e. a managed switch or a VLAN aware AP), but that these two networks are not? If that's the case, they do not need 802.1q stanzas because 802.1q is only relevant via wired ethernet (it doesn't apply to wifi, except in certain setups that are rather uncommon).
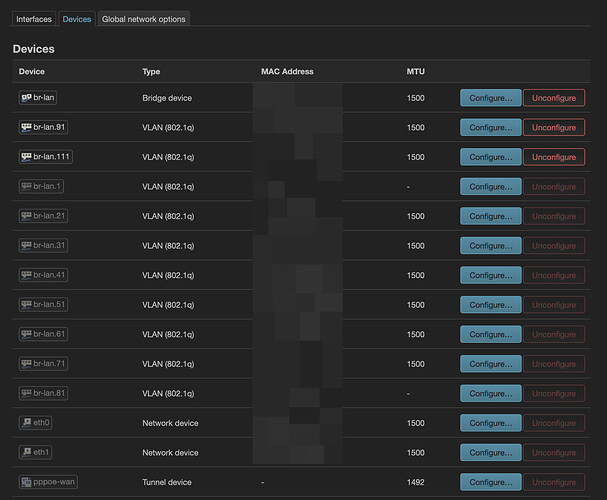
Like I said, the 802.1q device is created implicitly by means of the bridge-vlan.
As I mentioned above, they are only relevant if they are tied to a physical port -- and they are in fact tied, but indirectly:
the ifname line ties it to br-lan which in turn has a physical port defined under it:
If you have a managed switch downstream of this router and you configure it to expect VLANs 91 and 111 (both tagged), you'll see that the connection is indeed there.
Right, because they are implicitly generated, and they cannot be deleted because doing so would break the config since the 802.1q tags are necessary.
If they did, that would be explicitly defined. The implicit definition occurs because there is a higher level structure that relies on the 802.1q tags.
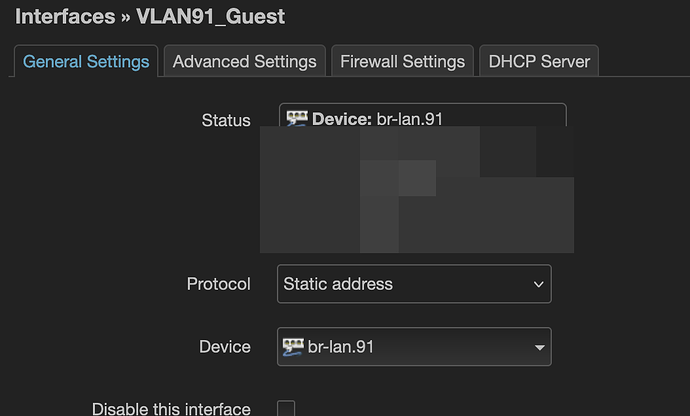
To be clear, if those two networks only exist for wifi on this exact device, you should remove the 802.1q stanzas and replace them with empty bridges. (technically, they aren't VLANs if they aren't connected to ethernet).
You would delete these:
And create empty bridges in their place:
config device
option name 'br-guest'
option type 'bridge'
option bridge_empty '1'
config device
option name 'br-general'
option type 'bridge'
option bridge_empty '1'
And then edit the network interfaces to use the new bridges:
config interface 'VLAN91_Guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.9.1'
option netmask '255.255.255.0'
...
config interface 'VLAN111_General'
option proto 'static'
option device 'br-general'
option ipaddr '192.168.11.1'
option netmask '255.255.255.0'
In fact, the bridge is only required if the network will be used on more than one physical interface. So a bridge is necessary if you are using wifi + ethernet, or 2 or more wifi radios. But it is not required when you are using only a single wifi radio. If that's the case, you can actually entirely omit the bridges I just suggested and then remove the device lines from those networks.