Then maybe a good step would be to make a backup of your existing configuration, then reset to defaults. Selectively restore the files (network, wireless, firewall, and then just the additional DHCP servers for the other networks in the DHCP file via copy and paste rather than file replacement).
Ok, so I actually tested a lot of things. The breakthrough is the following:
DNS works fine, DHCP is the one that does not work properly. If I use 192.168.1.1 (which is my adguard/rooter address) all works fine, blocklist are in action from adguard, I get internet connection. The problem is that DHCP does not setup automatically on the devices, and there is some issue with it.
Since I followed the installation script from the wiki and triple checked things, to my knowledge, things seem fine.
adguard runs on port 53, dnsmasq swapped to 54. Tried with both, though only 53 is needed as traffic rules for the guest network.
Now remember, I switch back to non-guest, no issues, DHCP works, 192.168.1.1 is automatically setup for me as the DNS. But moving it out to the guest network, or any other wifi interface that is not on the 192.168.1.1 subnet, it does not work, DHCP does not setup 192.168.1.1 automatically as the DNS on the device, it basically leaves you without any nameservers.
From the config files I've sent you, could you please check if there is anything that can cause the issue? Again, I have traffic rules for port 53, 67 and 68. DHCP server is not running on adguard, it's running on openwrt.
And here are some of the settings changed through the adguard installation script
# Get the first IPv4 and IPv6 Address of router and store them in following variables for use during the script.
NET_ADDR=$(/sbin/ip -o -4 addr list br-lan | awk 'NR==1{ split($4, ip_addr, "/"); print ip_addr[1] }')
NET_ADDR6=$(/sbin/ip -o -6 addr list br-lan scope global | awk 'NR==1{ split($4, ip_addr, "/"); print ip_addr[1] }')
echo "Router IPv4 : ""${NET_ADDR}"
echo "Router IPv6 : ""${NET_ADDR6}"
# 1. Enable dnsmasq to do PTR requests.
# 2. Reduce dnsmasq cache size as it will only provide PTR/rDNS info.
# 3. Disable rebind protection. Filtered DNS service responses from blocked domains are 0.0.0.0 which causes dnsmasq to fill the system log with possible DNS-rebind attack detected messages.
# 4. Move dnsmasq to port 54.
# 5. Set Ipv4 DNS advertised by option 6 DHCP
# 6. Set Ipv6 DNS advertised by DHCP
uci set dhcp.@dnsmasq[0].noresolv="0"
uci set dhcp.@dnsmasq[0].cachesize="1000"
uci set dhcp.@dnsmasq[0].rebind_protection='0'
uci set dhcp.@dnsmasq[0].port="54"
uci -q delete dhcp.@dnsmasq[0].server
uci add_list dhcp.@dnsmasq[0].server="${NET_ADDR}"
#Delete existing config ready to install new options.
uci -q delete dhcp.lan.dhcp_option
uci -q delete dhcp.lan.dns
# DHCP option 6: which DNS (Domain Name Server) to include in the IP configuration for name resolution
uci add_list dhcp.lan.dhcp_option='6,'"${NET_ADDR}"
#DHCP option 3: default router or last resort gateway for this interface
uci add_list dhcp.lan.dhcp_option='3,'"${NET_ADDR}"
Please elaborate...
Specifically, if you connect to the guest network, what happens?
Does the client get a DHCP lease? If so:
- what is the IP address
- what is the subnet mask
- what is the dns
- what is the gateway
If not, does it time out and result in an APIPA (169 address)?
I do get a proper IP address in the proper guest subnet, what I don't get is automatic DNS setup. The gateway is the same as the subnet. So everything is correct.
192.168.9.178 ip
192.168.9.1 subnet
192.168.9.1 gateway
no DNS
I don't get any time out.
This is the reason why my Fire TV stick worked out of the box, cause similarly to chromecast it bypasses provided DNS servers.
Some devices will bypass DHCP provided DNS servers e.g. Google Chromecast.
Setting up the DNS to 192.168.1.1 manually, everything is fixed.
This still indicates something wrong with the DNS configuration of your system. You have modified the normal dnsmasq DNS functions, so it's probably not happy with something you did there, but I'm not an expert with AGH/DoT/DoH.
But, you could try adding DHCP option 6 and the address of the router (or alternate DNS server) to the dhcp server config stanza and see if that helps.
I've also tried changing these on the VLAN, but it doesn't seem to work, plus it shouldn't be needed, as the traffic rules should help.
I'm going to return to what I said before...
I think that this is an issue with the DNS handling that you have configured... so...
Thanks. And I know that I keep asking, but I am so stuck on this and I have no idea where to head up next, I already reflashed with the router with a backup this morning, but to no avail. AGH it's crucial to my usecase and there is no way I can setup DNS manually on each device that enters the guest network.
I do know for a fact that I uninstalled AGH as per instructed on the wiki at one point, and in the uninstall commands these was included:
# Network Configuration
# Disable peer/ISP DNS
uci set network.wan.peerdns="0"
uci set network.wan6.peerdns="0"
# Configure DNS provider to Google DNS
uci -q delete network.wan.dns
uci add_list network.wan.dns="8.8.8.8"
uci add_list network.wan.dns="8.8.4.4"
Now I compared the installation script, and these were the only entries not included in it, so I wondered if I should switch these to 1 to peerdns and 192.168.1.1 for the home router, as it's where AGH listens? Does that make any sense?
let's see the current network and dhcp files.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '[redacted]'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan.71'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
config interface 'wan'
option device 'eth0'
option proto 'pppoe'
option username '[redacted]'
option password '[redacted]'
option ipv6 'auto'
option peerdns '1'
option dns '8.8.8.8 8.8.4.4'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '1'
list dns '2001:4860:4860::8888'
list dns '2001:4860:4860::8844'
config interface 'wwan'
option proto 'dhcp'
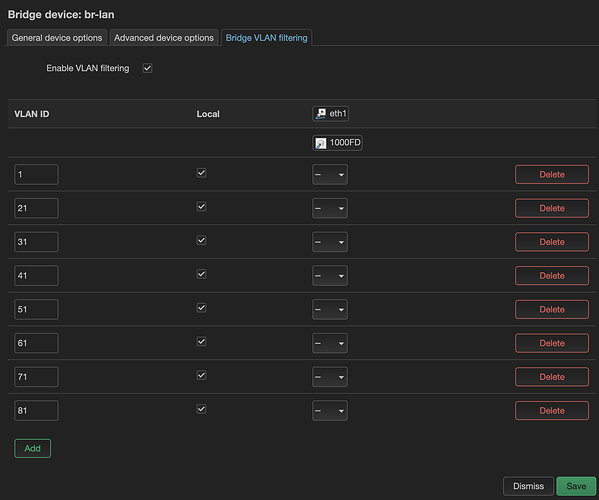
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '21'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '31'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '41'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '51'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '61'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '71'
list ports 'eth1:t'
config bridge-vlan
option device 'br-lan'
option vlan '81'
list ports 'eth1:t'
config interface 'VLAN21_admin'
option proto 'static'
option device 'br-lan.21'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
config interface 'VLAN41_NAS'
option proto 'static'
option device 'br-lan.41'
option ipaddr '192.168.4.1'
option netmask '255.255.255.0'
config interface 'VLAN31_PC'
option proto 'static'
option device 'br-lan.31'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'VLAN51_Server'
option proto 'static'
option device 'br-lan.51'
option ipaddr '192.168.5.1'
option netmask '255.255.255.0'
config device
option type '8021q'
option ifname 'br-lan'
option vid '91'
option name 'br-lan.91'
config interface 'VLAN61_IoT'
option proto 'static'
option device 'br-lan.61'
option ipaddr '192.168.6.1'
option netmask '255.255.255.0'
config interface 'VLAN91_Guest'
option proto 'static'
option device 'br-lan.91'
option ipaddr '192.168.9.1'
option netmask '255.255.255.0'
config device
option type '8021q'
option ifname 'br-lan'
option vid '111'
option name 'br-lan.111'
config interface 'VLAN111_General'
option proto 'static'
option device 'br-lan.111'
option ipaddr '192.168.11.1'
option netmask '255.255.255.0'
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '0'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
option noresolv '0'
option cachesize '1000'
option port '54'
list server '192.168.1.1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
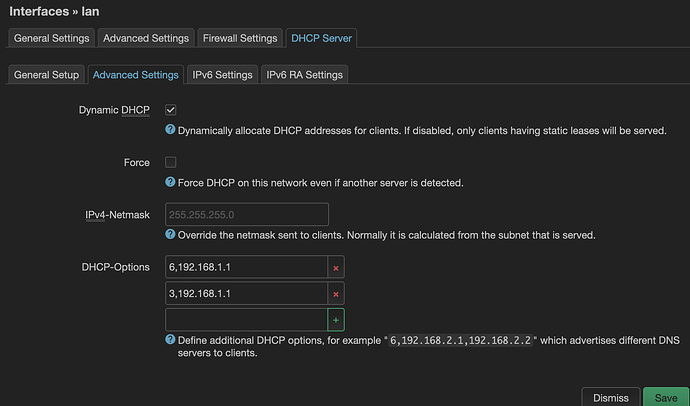
list dhcp_option '6,192.168.1.1'
list dhcp_option '3,192.168.1.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'VLAN21_admin'
option interface 'VLAN21_admin'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'VLAN41_NAS'
option interface 'VLAN41_NAS'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'VLAN31_PC'
option interface 'VLAN31_PC'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'VLAN51_Server'
option interface 'VLAN51_Server'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'VLAN61_IoT'
option interface 'VLAN61_IoT'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'VLAN91_Guest'
option interface 'VLAN91_Guest'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'VLAN111_General'
option interface 'VLAN111_General'
option start '100'
option limit '150'
option leasetime '12h'
I didn't remove the 802q vlans, I thought you never responded to me why removing them if I already have a switch also connect locally to them, but I see now that you did answer me that.
Please do remove them. But I don't think it will solve the problem.
AGH is the cause from everything I can see. I am not an expert on how to configure it properly, but I believe that it is critical to prove (or disprove) my assertion that AGH is somehow preventing the DHCP server from handing out the correct (or any) DNS server.
I do see that you set option 6 for just one of the networks -- did it help on that one? If so, try implementing it on the others. However, if it doesn't fix the issue, it's time to reset to defaults and then selectively restore the files as I described previously. This will ensure that you can get everything setup aside from AGH. And yes, I understand that AGH is critical for you, but once we can demonstrate that AGH is the cause, you can start a new thread with a title about AGH issues on VLANs/DHCP server issues (this will hopefully draw in the people who know how to properly configure it for a scenario like yours).
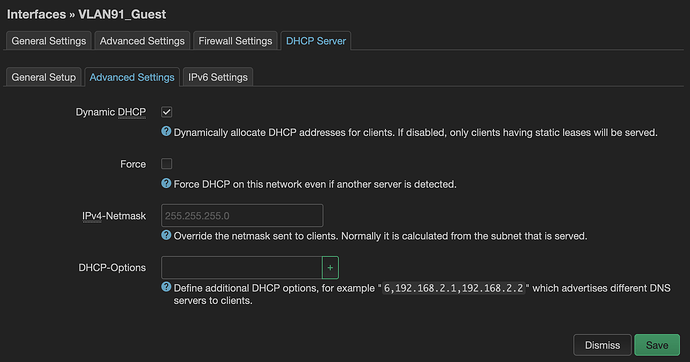
This is how my VLANs look for the DHCP:
If I try to set the same options to my lan interface (only interface that works and it's at 192.168.1.1), with or without option 6, my devices don't even get assigned an IP. On mac it connects, without no internet, no ip, no gateway, on android it just tries to reconnect all the time, to no avail.
I am confused since I followed the script closely and tested all varieties.
Maybe I can try uninstalling adguard following the script offered first:
https://openwrt.org/docs/guide-user/services/dns/adguard-home#uninstalling
Can you elaborate on that?
To me AGH looks somewhat bloated, I am happy wit HTTPS DNS proxy and adblock, so curious as to what I am missing ![]()
Blocklists, DoQ support, per client management, agh perfromance with parallel requests is great too. Stats less needed tbh.
A (mostly) fresh start will allow you to figure out what specifically caused things to break, and then you can zero in on that in order to resolve it. Otherwise, we're kinda just stabbing in the dark, knowing that AGH is almost certainly the problem, but without being able to identify why (at least on my end, I don't know AGH so I can't untangle any messes that it could cause).
Uninstalled AGH with the script that the wiki provides, everything went back to normal and all things worked. Re-installed AGH, with the instructions given on the wiki, same issue again as you say...
The only important thing I noticed is that I changed the br-lan to br-lan.71 in the installation script, due to my configuration with the managed switch. br-lan.71 device is assigned to my lan in my setup, and br-lan is just a bridged device assigned at eth1 with the following setup:
As I expected. Glad that we can confirm this. That does conclusively point to AGH as the root cause.
This sounds like the correct modification.
I would suggest that we close this thread (mark as solved) insofar as we have found a solution (although not desirable in your case) of removing AGH. Since the problem is now indeed identified, a new thread can be created specifically asking for help with AGH across multiple networks with the observed behavior that once AGH is installed and running, the DHCP server doesn't send a DNS server via option 6.
Thank you, before closing this down I will use your knowledge on two things that you referred before, and I am still not 100% clear on the reasoning:
But how come I VLAN off the managed switch ports if I do this?
In what cases these can be useful if you think they are unnecesary in most cases?