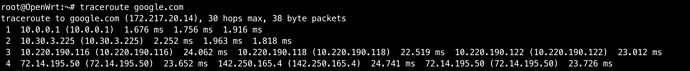
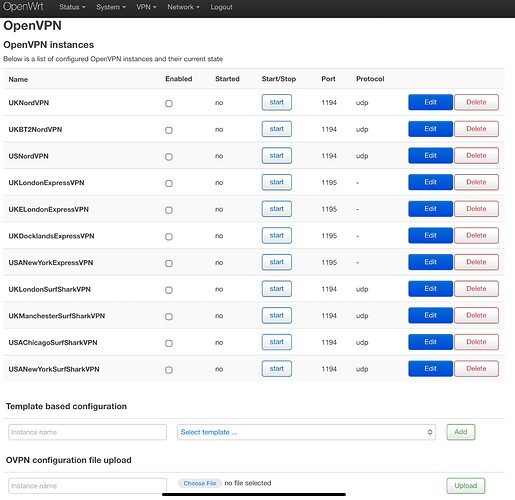
Ok I added that now to the file, still no connection but I did notice the attempt to reach a website seems to time out faster now since that addition
Try restarting your router to make sure that all the services are restarted properly.
Then, if it still doesn't work, try the ping test (8.8.8.8 and google.com) from your computer again.
Rebooted and then tried the ping, got different results for either ping:
Google getting:
Ttl: 64
Bytes: 56
Sent: 1
Received: 1
Lost: 0
But 8.8.8.8 getting the response of request timed out, no packets received etc.
That is very strange.
From your OpenWrt router (ssh session), let's see the following:
route
traceroute google.com
Then do the same from your computer.
And what does the openwrt system show for route?
It looks to me like you have a vpn active.
Sorry, how would I do the route on the system?
These are my VPNs, as far as I can tell they are switched off atm, perhaps it’s something in the firewall for VPNs?
Just type route Into an ssh session on your router.
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have
ubus call system board; \
iptables-save -c; ip6tables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
ip -6 addr ; ip -6 ro li tab all ; ip -6 ru; \
ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
Ok I did that, the results were:
* /tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "4.14.215",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT3200ACM",
"board_name": "linksys,rango",
"release": {
"distribution": "OpenWrt",
"version": "19.07.6",
"revision": "r11278-8055e38794",
"target": "mvebu/cortexa9",
"description": "OpenWrt 19.07.6 r11278-8055e38794"
}
}
# Generated by iptables-save v1.8.3 on Wed Jun 22 22:28:15 2022
*nat
:PREROUTING ACCEPT [4051:786637]
:INPUT ACCEPT [340:32851]
:OUTPUT ACCEPT [6057:436150]
:POSTROUTING ACCEPT [39:2764]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_vpnfirewall_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_vpnfirewall_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_vpnfirewall_postrouting - [0:0]
:zone_vpnfirewall_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[4051:786637] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[3904:779424] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i tun0 -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i eth1.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[147:7213] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_prerouting
[6213:444450] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[0:0] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o tun0 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o eth1.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[6174:441686] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_postrouting
[0:0] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[0:0] -A zone_lan_postrouting -s 192.168.1.0/24 -d 192.168.1.85/32 -p tcp -m tcp --dport 32400 -m comment --comment "!fw3: DT NAS Plex (reflection)" -j SNAT --to-source 192.168.1.1
[3904:779424] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[0:0] -A zone_lan_prerouting -s 192.168.1.0/24 -d 82.79.28.72/32 -p tcp -m tcp --dport 32400 -m comment --comment "!fw3: DT NAS Plex (reflection)" -j DNAT --to-destination 192.168.1.85:32400
[0:0] -A zone_vpnfirewall_postrouting -m comment --comment "!fw3: Custom vpnfirewall postrouting rule chain" -j postrouting_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_vpnfirewall_prerouting -m comment --comment "!fw3: Custom vpnfirewall prerouting rule chain" -j prerouting_vpnfirewall_rule
[6174:441686] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[6174:441686] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[147:7213] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 32400 -m comment --comment "!fw3: DT NAS Plex" -j DNAT --to-destination 192.168.1.85:32400
COMMIT
# Completed on Wed Jun 22 22:28:15 2022
# Generated by iptables-save v1.8.3 on Wed Jun 22 22:28:15 2022
*mangle
:PREROUTING ACCEPT [13659:2272453]
:INPUT ACCEPT [9989:1468651]
:FORWARD ACCEPT [124:60045]
:OUTPUT ACCEPT [7525:892091]
:POSTROUTING ACCEPT [7647:952056]
[0:0] -A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -o eth1.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i eth1.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[2:128] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[2:120] -A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone vpnfirewall MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone vpnfirewall MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Jun 22 22:28:15 2022
# Generated by iptables-save v1.8.3 on Wed Jun 22 22:28:15 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_vpnfirewall_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_vpnfirewall_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_vpnfirewall_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_vpnfirewall_dest_ACCEPT - [0:0]
:zone_vpnfirewall_dest_REJECT - [0:0]
:zone_vpnfirewall_forward - [0:0]
:zone_vpnfirewall_input - [0:0]
:zone_vpnfirewall_output - [0:0]
:zone_vpnfirewall_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[460:49947] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[9529:1418704] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[6476:1077790] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[179:8516] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[2860:331857] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i tun0 -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i eth1.2 -m comment --comment "!fw3" -j zone_wan_input
[193:9057] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_input
[124:60045] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[102:57105] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[22:2940] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i eth1.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[460:49947] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[7069:843328] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[1040:409250] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o eth1.2 -m comment --comment "!fw3" -j zone_wan_output
[6029:434078] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_output
[182:7636] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[7:1297] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[179:8516] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[0:0] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[22:2940] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[22:2940] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to vpnfirewall forwarding policy" -j zone_vpnfirewall_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2860:331857] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2860:331857] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[0:0] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[0:0] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2860:331857] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_vpnfirewall_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_vpnfirewall_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_vpnfirewall_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_vpnfirewall_forward -m comment --comment "!fw3: Custom vpnfirewall forwarding rule chain" -j forwarding_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_vpnfirewall_forward -m comment --comment "!fw3" -j zone_vpnfirewall_dest_REJECT
[0:0] -A zone_vpnfirewall_input -m comment --comment "!fw3: Custom vpnfirewall input rule chain" -j input_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_vpnfirewall_input -m comment --comment "!fw3" -j zone_vpnfirewall_src_REJECT
[0:0] -A zone_vpnfirewall_output -m comment --comment "!fw3: Custom vpnfirewall output rule chain" -j output_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_output -m comment --comment "!fw3" -j zone_vpnfirewall_dest_ACCEPT
[0:0] -A zone_vpnfirewall_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth1.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o eth1.2 -m comment --comment "!fw3" -j ACCEPT
[2:80] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[6049:436938] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o eth1.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[193:9057] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[4:124] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[189:8933] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[6029:434078] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[6029:434078] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i eth1.2 -m comment --comment "!fw3" -j reject
[189:8933] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Jun 22 22:28:15 2022
# Generated by ip6tables-save v1.8.3 on Wed Jun 22 22:28:15 2022
*mangle
:PREROUTING ACCEPT [1521545:1626834799]
:INPUT ACCEPT [9317:966747]
:FORWARD ACCEPT [1510840:1625406477]
:OUTPUT ACCEPT [9976:1636851]
:POSTROUTING ACCEPT [1520770:1627039696]
[0:0] -A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -o eth1.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i eth1.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[1105:90596] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[1163:93016] -A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -o tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone vpnfirewall MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i tun0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone vpnfirewall MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Wed Jun 22 22:28:15 2022
# Generated by ip6tables-save v1.8.3 on Wed Jun 22 22:28:15 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [14:1296]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_vpnfirewall_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_vpnfirewall_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_vpnfirewall_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_vpnfirewall_dest_ACCEPT - [0:0]
:zone_vpnfirewall_dest_REJECT - [0:0]
:zone_vpnfirewall_forward - [0:0]
:zone_vpnfirewall_input - [0:0]
:zone_vpnfirewall_output - [0:0]
:zone_vpnfirewall_src_REJECT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[32:6445] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[9285:960302] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[699:194546] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[8577:765260] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i tun0 -m comment --comment "!fw3" -j zone_wan_input
[2:104] -A INPUT -i eth1.2 -m comment --comment "!fw3" -j zone_wan_input
[7:392] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_input
[1510848:1625413085] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[1508900:1624669916] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1923:740957] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i eth1.2 -m comment --comment "!fw3" -j zone_wan_forward
[25:2212] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_forward
[25:2212] -A FORWARD -m comment --comment "!fw3" -j reject
[32:6445] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[9944:1630406] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[6997:1413073] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[2603:184752] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[0:0] -A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_wan_output
[23:3254] -A OUTPUT -o eth1.2 -m comment --comment "!fw3" -j zone_wan_output
[307:28031] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o tun0 -m comment --comment "!fw3" -j zone_vpnfirewall_output
[25:2212] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp6-port-unreachable
[0:0] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[2603:184752] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[1923:740957] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[1923:740957] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to vpnfirewall forwarding policy" -j zone_vpnfirewall_dest_ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[8577:765260] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[8577:765260] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[2603:184752] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[2603:184752] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[8577:765260] -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_vpnfirewall_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_vpnfirewall_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_vpnfirewall_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_vpnfirewall_forward -m comment --comment "!fw3: Custom vpnfirewall forwarding rule chain" -j forwarding_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_forward -m comment --comment "!fw3" -j zone_vpnfirewall_dest_REJECT
[0:0] -A zone_vpnfirewall_input -m comment --comment "!fw3: Custom vpnfirewall input rule chain" -j input_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_input -m comment --comment "!fw3" -j zone_vpnfirewall_src_REJECT
[0:0] -A zone_vpnfirewall_output -m comment --comment "!fw3: Custom vpnfirewall output rule chain" -j output_vpnfirewall_rule
[0:0] -A zone_vpnfirewall_output -m comment --comment "!fw3" -j zone_vpnfirewall_dest_ACCEPT
[0:0] -A zone_vpnfirewall_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_ACCEPT -o tun0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o tun0 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth1.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[23:3254] -A zone_wan_dest_ACCEPT -o eth1.2 -m comment --comment "!fw3" -j ACCEPT
[23:1524] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[2207:767464] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o eth1.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[25:2212] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 128 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 129 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 2 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 3 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 4/0 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p ipv6-icmp -m icmp6 --icmpv6-type 4/1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Forward" -j ACCEPT
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[25:2212] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[9:496] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -s fc00::/6 -d fc00::/6 -p udp -m udp --dport 546 -m comment --comment "!fw3: Allow-DHCPv6" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 130/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 131/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 132/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -s fe80::/10 -p ipv6-icmp -m icmp6 --icmpv6-type 143/0 -m comment --comment "!fw3: Allow-MLD" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 128 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 129 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 2 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 3 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 4/0 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 4/1 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[2:104] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 133 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 135 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[7:392] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 134 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -p ipv6-icmp -m icmp6 --icmpv6-type 136 -m limit --limit 1000/sec -m comment --comment "!fw3: Allow-ICMPv6-Input" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[330:31285] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[330:31285] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i tun0 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i eth1.2 -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Wed Jun 22 22:28:15 2022
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
13: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc fq_codel state UNKNOWN group default qlen 3
inet 82.79.28.72 peer 10.0.0.1/32 scope global pppoe-wan
valid_lft forever preferred_lft forever
default via 10.0.0.1 dev pppoe-wan proto static
10.0.0.1 dev pppoe-wan proto kernel scope link src 82.79.28.72
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
local 82.79.28.72 dev pppoe-wan table local proto kernel scope host src 82.79.28.72
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
Continued:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 state UNKNOWN qlen 1000
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 532
inet6 fe80::ea9f:80ff:fe1a:410/64 scope link
valid_lft forever preferred_lft forever
3: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 532
inet6 fe80::e89f:80ff:fe1a:410/64 scope link
valid_lft forever preferred_lft forever
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a02:2f04:d33:9d00::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fd0a:b426:4e56::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::e89f:80ff:fe1a:410/64 scope link
valid_lft forever preferred_lft forever
10: eth1.2@eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::ea9f:80ff:fe1a:410/64 scope link
valid_lft forever preferred_lft forever
11: wlan1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::ea9f:80ff:fe1a:411/64 scope link
valid_lft forever preferred_lft forever
12: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 fe80::ea9f:80ff:fe1a:412/64 scope link
valid_lft forever preferred_lft forever
13: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 state UNKNOWN qlen 3
inet6 2a02:2f04:d:33d7::524f:1c48/128 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::524f:1c48/10 scope link
valid_lft forever preferred_lft forever
default from 2a02:2f04:d:33d7::524f:1c48 via fe80::1 dev pppoe-wan proto static metric 512 pref medium
default from 2a02:2f04:d33:9d00::/56 via fe80::1 dev pppoe-wan proto static metric 512 pref medium
2a02:2f04:d33:9d00::/64 dev br-lan proto static metric 1024 pref medium
unreachable 2a02:2f04:d33:9d00::/56 dev lo proto static metric 2147483647 error 4294967183 pref medium
fd0a:b426:4e56::/64 dev br-lan proto static metric 1024 pref medium
unreachable fd0a:b426:4e56::/48 dev lo proto static metric 2147483647 error 4294967183 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
fe80::/64 dev eth1 proto kernel metric 256 pref medium
fe80::/64 dev eth1.2 proto kernel metric 256 pref medium
fe80::/64 dev br-lan proto kernel metric 256 pref medium
fe80::/64 dev wlan1 proto kernel metric 256 pref medium
fe80::/64 dev wlan0 proto kernel metric 256 pref medium
fe80::/10 dev pppoe-wan metric 1 pref medium
fe80::/10 dev pppoe-wan proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
local 2a02:2f04:d:33d7::524f:1c48 dev pppoe-wan table local proto kernel metric 0 pref medium
anycast 2a02:2f04:d33:9d00:: dev br-lan table local proto kernel metric 0 pref medium
local 2a02:2f04:d33:9d00::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fd0a:b426:4e56:: dev br-lan table local proto kernel metric 0 pref medium
local fd0a:b426:4e56::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
anycast fe80:: dev eth1.2 table local proto kernel metric 0 pref medium
anycast fe80:: dev eth1 table local proto kernel metric 0 pref medium
anycast fe80:: dev pppoe-wan table local proto kernel metric 0 pref medium
anycast fe80:: dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan1 table local proto kernel metric 0 pref medium
anycast fe80:: dev wlan0 table local proto kernel metric 0 pref medium
local fe80::524f:1c48 dev pppoe-wan table local proto kernel metric 0 pref medium
local fe80::e89f:80ff:fe1a:410 dev eth0 table local proto kernel metric 0 pref medium
local fe80::e89f:80ff:fe1a:410 dev br-lan table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fe1a:410 dev eth1.2 table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fe1a:410 dev eth1 table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fe1a:411 dev wlan1 table local proto kernel metric 0 pref medium
local fe80::ea9f:80ff:fe1a:412 dev wlan0 table local proto kernel metric 0 pref medium
ff00::/8 dev eth0 table local metric 256 pref medium
ff00::/8 dev br-lan table local metric 256 pref medium
ff00::/8 dev eth1 table local metric 256 pref medium
ff00::/8 dev eth1.2 table local metric 256 pref medium
ff00::/8 dev pppoe-wan table local metric 256 pref medium
ff00::/8 dev wlan1 table local metric 256 pref medium
ff00::/8 dev wlan0 table local metric 256 pref medium
0: from all lookup local
32766: from all lookup main
4200000000: from 2a02:2f04:d33:9d00::1/60 iif br-lan unreachable
4200000001: from all iif lo failed_policy
4200000008: from all iif br-lan failed_policy
4200000013: from all iif pppoe-wan failed_policy
4200000013: from all iif pppoe-wan failed_policy
ls: /tmp/resolv.*/*: No such file or directory
lrwxrwxrwx 1 root root 16 Jan 19 2021 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 32 Jun 22 21:50 /tmp/resolv.conf
-rw-r--r-- 1 root root 146 Jun 22 21:50 /tmp/resolv.conf.auto
-rw-r--r-- 1 root root 50 Jun 22 21:50 /tmp/resolv.conf.ppp
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface wan
nameserver 193.231.252.1
nameserver 213.154.124.1
# Interface wan_6
nameserver 2a02:2f0c:8000:3::1
nameserver 2a02:2f0c:8000:8::1
==> /tmp/resolv.conf.ppp <==
nameserver 193.231.252.1
nameserver 213.154.124.1
head: /tmp/resolv.*/*: No such file or directory
I think it might be easiest to make a backup and then reset to defaults. From there, setup your wifi and the PPPoE WAN. Once those are done, test to see if you get a working connection.
Thanks so much for your help! When I woke up this morning I reset all settings and tried again and it worked! Not sure what it was,
Really appreciate your time and help
That is great news!
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.