Okay, so I was bold enough to wipe that thing, but 
Setup as before:
LAN2 (10.0.10.x) <-> LAN:openWRT:WAN <-> LAN1 (10.0.0.x) <-> FritzBox <-> DSL/ISP/WWW
Current problem I need to solve first: Hosts behind openWRT can't ping (nor do anything else) to anywhere outside LAN1+LAN2, e.g.
ping 8.8.8.8 gives From XX.X.XX.XXX icmp_seq=1 Packet filtered (with the X's being the public (dynamic) IP address of my FritzBox DSL ISP connection).
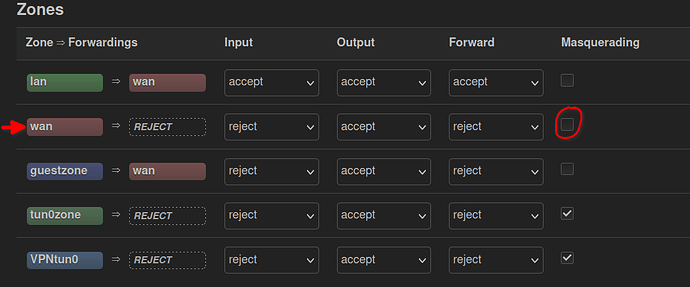
This time, it doesn't matter whether I activate masquerading on WAN in the Firewall (as it did before); keeping MASQ=OFF there now.
I guess you'll need these again instead of screenshots?:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
Here we go again.
root@SLATE:~# ubus call system board
{
"kernel": "5.15.137",
"hostname": "SLATE",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "GL.iNet GL-AR750S (NOR/NAND)",
"board_name": "glinet,gl-ar750s-nor-nand",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ath79/nand",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
root@SLATE:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd60:e069:b6c8::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ip6assign '60'
list ipaddr '10.0.10.1/24'
option gateway '10.0.0.1'
list dns '10.0.0.1'
list dns_search 'fritz.box'
config interface 'wan'
option device 'eth0.2'
option proto 'static'
option ipaddr '10.0.0.2'
option netmask '255.255.255.0'
option gateway '10.0.0.1'
list dns '10.0.0.1'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
option auto '0'
option reqaddress 'try'
option reqprefix 'auto'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config device
option name 'eth0.2'
option type '8021q'
option ifname 'eth0'
option vid '2'
option macaddr '94:83:C4:0F:B3:4F'
Note on the above last line option macaddr...:
There seems to be a bug I came across already in the past. WAN and LAN by default get the same (!) MAC address, i.e. the hardware address. This leads to various strange effects, e.g.:
- you can (after punching a hole into the FW) ping hosts behind the openWRT from LAN1. Pinging from a host behind the openWRT to a host on the WAN side gives ~90% packet losses.
- you can't ssh to any host behind the openWRT, even though a correct FW rule has been set
- others...
Fix: in LUCI, Network>Interfaces>Devices tab, for eth0.2, force a MAC address changed on the last digit to be different from the hardware MAC
Next, Firewall.
root@SLATE:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
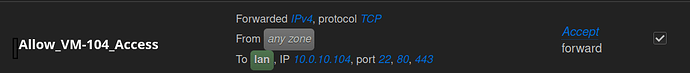
option name 'Allow_Web+SSH_WAN-to-LAN-IP'
list proto 'tcp'
option src 'wan'
option dest 'lan'
list dest_ip '10.0.10.1'
option dest_port '22 80 443'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow_WebIF_on-WAN-IP'
list proto 'tcp'
option src 'wan'
option dest_port '22 80 443'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow_VM-105_pihole'
option src 'wan'
option dest 'lan'
option dest_port '22 53 80 443 '
option target 'ACCEPT'
option family 'ipv4'
list dest_ip '10.0.10.105'
list proto 'tcp'
config rule
option name 'Allow_Ping_to_LAN'
option family 'ipv4'
list proto 'icmp'
option src 'wan'
option dest 'lan'
option target 'ACCEPT'
Have only added some few rules to gain access to the openWRT web if from both sides, ssh into it, and for one host (DNS server, .10.105) behind openWRT. Need to get that to speak to the outside world first, other machine specific rules will then be easy. Have not changed any of the default rules though eventually I want to lock down any and all IPv6 stuff cause I just don't master any of it yet and want to be sure anything I do always uses the IPv4 routes, not "bypassing" me (because something isn't right on IPv4 and the server/service/app silently falls back to IPv6 without me knowing).
So, what do I need to do now to get the machine on LAN2 to pass through openWRT via LAN1 to the world without my ISP blocking something?