Hello everyone,
After searching through plethora of similar topics, browsing internet for a potential solution I finally became clueless and decided to turn to you for help.
I'd call myself a newbie when it comes to OpenWrt administration, although I've managed to successfully configure my home network which is functioning to this day.
I am using PureVPN and wanted to configure wireguard interface (which I think I've partially succeeded in) in order to route traffic from a single wifi through it.
Previous configuration was using OpenVPN and it worked well, although it was pretty slow.
The problem I'm currently facing is that I can't route the traffic properly (mobile devices connected to the wifi ap report lack of internet access) despite wg interface being connected (RX/TX look well).
Below is my config:
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fddd:4e53:8a95::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
option ip6assign '60'
option defaultroute '0'
option delegate '0'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option hostname '*'
option type 'bridge'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option auto '0'
option reqaddress 'none'
option reqprefix 'auto'
config device
option name 'wan'
config device 'guest_dev'
option type 'bridge'
option name 'br-guest'
config interface 'guest'
option proto 'static'
option ipaddr '172.16.0.1'
option netmask '255.255.255.0'
option delegate '0'
config interface 'wg0_int'
option proto 'wireguard'
option private_key '---'
list addresses '10.1.125.110'
list dns '172.94.48.2'
list dns '172.94.48.4'
config wireguard_wg0_int
option description 'wireguard'
option public_key ''
option private_key ''
list allowed_ips '10.1.125.110/32'
list allowed_ips '172.16.0.0/24'
option endpoint_host ''
option endpoint_port '51820'
option persistent_keepalive '21'
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config zone
option name 'VPN_FW'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wg0_int'
config zone
option name 'guest'
option output 'ACCEPT'
option forward 'ACCEPT'
option input 'ACCEPT'
list network 'guest'
config forwarding
option src 'lan'
option dest 'wan'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config forwarding
option src 'guest'
option dest 'VPN_FW'
wifi ap config
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option ssid 'piwnica5'
option encryption 'psk2'
option key ''
option network 'guest'
Basically, what I want to do is to route traffic from wifi SSID whose subnet is '172.16.0.0/24' through wg0_int interface. The subnet is added in peer's allowed IPs, I have pbr set up for that subnet as well.
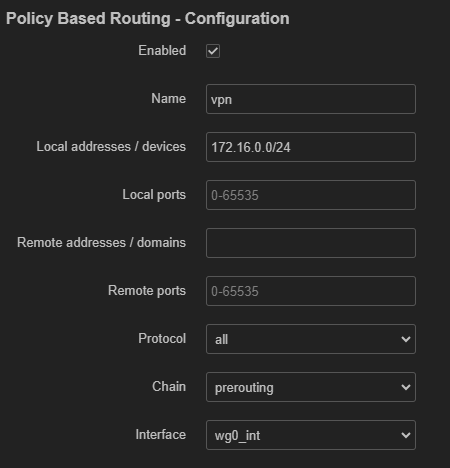
I'll be most grateful for any pointers in the direction of what I'm missing here.
Thanks in advance.