I'm working on getting Wireguard setup with a 3rd party VPN provider (OVPN) on a GL.iNet Beryl (GL-MT1300). My intent is to eventually have 3 separate wg interfaces to support 3 hosts to 3 different VPN servers, however I'm stuck on getting the first configured.
I'm following this guide from OVPN to set up Wireguard through Luci: https://www.ovpn.com/en/guides/wireguard/openwrt
I first set up the connection through the gl.inet interface to ensure the VPN details were good. It worked, all traffic was routed through the VPN. I then reset the router to start fresh in luci.
I can see that a connection is being established to the server, however I'm unable to get to the internet from any hosts. I can ping from the router, though it isn't going through the vpn.
root@GL-MT1300:~# ip address show; ip route show table all; ip rule show; iptables-save; wg show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether 94:83:c4:16:72:20 brd ff:ff:ff:ff:ff:ff
inet6 fe80::9683:c4ff:fe16:7220/64 scope link
valid_lft forever preferred_lft forever
3: teql0: <NOARP> mtu 1500 qdisc noop state DOWN group default qlen 100
link/void
4: ra0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UP group default qlen 1000
link/ether 94:83:c4:16:72:23 brd ff:ff:ff:ff:ff:ff
5: br-guest: <BROADCAST,MULTICAST> mtu 1500 qdisc noqueue state DOWN group default qlen 1000
link/ether f2:d7:4d:b3:08:b3 brd ff:ff:ff:ff:ff:ff
inet 192.168.9.1/24 brd 192.168.9.255 scope global br-guest
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 94:83:c4:16:72:21 brd ff:ff:ff:ff:ff:ff
inet 192.168.8.1/24 brd 192.168.8.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default qlen 1000
link/ether 94:83:c4:16:72:21 brd ff:ff:ff:ff:ff:ff
9: ra1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
10: rax0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UNKNOWN group default qlen 1000
link/ether 94:83:c4:16:72:22 brd ff:ff:ff:ff:ff:ff
11: rax1: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 00:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
12: apcli0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 92:83:c4:16:72:22 brd ff:ff:ff:ff:ff:ff
13: apclix0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 92:93:c4:16:72:22 brd ff:ff:ff:ff:ff:ff
23: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 94:83:c4:16:72:20 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.117/24 brd 192.168.0.255 scope global eth0.2
valid_lft forever preferred_lft forever
24: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN group default qlen 1000
link/none
inet 146.70.58.163/32 brd 255.255.255.255 scope global wg0
valid_lft forever preferred_lft forever
default via 192.168.0.1 dev eth0.2 table 1 metric 10
192.168.0.0/24 dev eth0.2 table 1 proto static scope link metric 10
192.168.8.0/24 dev br-lan table 1 proto kernel scope link src 192.168.8.1
194.37.97.35 via 192.168.0.1 dev eth0.2 table 1 proto static metric 10
default dev wg0 proto static scope link
default via 192.168.0.1 dev eth0.2 proto static src 192.168.0.117 metric 10
192.168.0.0/24 dev eth0.2 proto static scope link metric 10
192.168.8.0/24 dev br-lan proto kernel scope link src 192.168.8.1
194.37.97.35 via 192.168.0.1 dev eth0.2 proto static metric 10
broadcast 127.0.0.0 dev lo table local proto kernel scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 146.70.58.163 dev wg0 table local proto kernel scope host src 146.70.58.163
broadcast 192.168.0.0 dev eth0.2 table local proto kernel scope link src 192.168.0.117
local 192.168.0.117 dev eth0.2 table local proto kernel scope host src 192.168.0.117
broadcast 192.168.0.255 dev eth0.2 table local proto kernel scope link src 192.168.0.117
broadcast 192.168.8.0 dev br-lan table local proto kernel scope link src 192.168.8.1
local 192.168.8.1 dev br-lan table local proto kernel scope host src 192.168.8.1
broadcast 192.168.8.255 dev br-lan table local proto kernel scope link src 192.168.8.1
local 192.168.9.1 dev br-guest table local proto kernel scope host src 192.168.9.1
unreachable fde5:2097:791c::/48 dev lo proto static metric 2147483647 error 4294967148 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
local fe80::9683:c4ff:fe16:7220 dev eth0 table local proto kernel metric 0 pref medium
ff00::/8 dev eth0 table local proto kernel metric 256 pref medium
ff00::/8 dev wg0 table local proto kernel metric 256 pref medium
0: from all lookup local
1001: from all iif eth0.2 lookup 1
2001: from all fwmark 0x100/0x3f00 lookup 1
2061: from all fwmark 0x3d00/0x3f00 blackhole
2062: from all fwmark 0x3e00/0x3f00 unreachable
32766: from all lookup main
32767: from all lookup default
# Generated by iptables-save v1.8.3 on Fri Mar 18 16:09:16 2022
*nat
:PREROUTING ACCEPT [3768:348656]
:INPUT ACCEPT [50:3305]
:OUTPUT ACCEPT [484:37882]
:POSTROUTING ACCEPT [3172:127361]
:GL_SPEC_DMZ - [0:0]
:postrouting_guestzone_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_guestzone_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_OVPN_postrouting - [0:0]
:zone_OVPN_prerouting - [0:0]
:zone_guestzone_postrouting - [0:0]
:zone_guestzone_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
-A PREROUTING -j GL_SPEC_DMZ
-A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
-A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
-A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
-A PREROUTING -i wg0 -m comment --comment "!fw3" -j zone_OVPN_prerouting
-A PREROUTING -i br-guest -m comment --comment "!fw3" -j zone_guestzone_prerouting
-A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
-A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
-A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
-A POSTROUTING -o wg0 -m comment --comment "!fw3" -j zone_OVPN_postrouting
-A POSTROUTING -o br-guest -m comment --comment "!fw3" -j zone_guestzone_postrouting
-A zone_OVPN_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_guestzone_postrouting -m comment --comment "!fw3: Custom guestzone postrouting rule chain" -j postrouting_guestzone_rule
-A zone_guestzone_prerouting -m comment --comment "!fw3: Custom guestzone prerouting rule chain" -j prerouting_guestzone_rule
-A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
-A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
-A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
-A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
-A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Fri Mar 18 16:09:16 2022
# Generated by iptables-save v1.8.3 on Fri Mar 18 16:09:16 2022
*raw
:PREROUTING ACCEPT [5326:571548]
:OUTPUT ACCEPT [4784:485265]
:zone_guestzone_helper - [0:0]
:zone_lan_helper - [0:0]
-A PREROUTING -i br-lan -m comment --comment "!fw3: lan CT helper assignment" -j zone_lan_helper
-A PREROUTING -i br-guest -m comment --comment "!fw3: guestzone CT helper assignment" -j zone_guestzone_helper
-A OUTPUT -p tcp -m tcp --dport 1723 -j CT --helper pptp
-A zone_guestzone_helper -p udp -m comment --comment "!fw3: Amanda backup and archiving proto" -m udp --dport 10080 -j CT --helper amanda
-A zone_guestzone_helper -p tcp -m comment --comment "!fw3: FTP passive connection tracking" -m tcp --dport 21 -j CT --helper ftp
-A zone_guestzone_helper -p udp -m comment --comment "!fw3: RAS proto tracking" -m udp --dport 1719 -j CT --helper RAS
-A zone_guestzone_helper -p tcp -m comment --comment "!fw3: Q.931 proto tracking" -m tcp --dport 1720 -j CT --helper Q.931
-A zone_guestzone_helper -p tcp -m comment --comment "!fw3: IRC DCC connection tracking" -m tcp --dport 6667 -j CT --helper irc
-A zone_guestzone_helper -p tcp -m comment --comment "!fw3: PPTP VPN connection tracking" -m tcp --dport 1723 -j CT --helper pptp
-A zone_guestzone_helper -p tcp -m comment --comment "!fw3: SIP VoIP connection tracking" -m tcp --dport 5060 -j CT --helper sip
-A zone_guestzone_helper -p udp -m comment --comment "!fw3: SIP VoIP connection tracking" -m udp --dport 5060 -j CT --helper sip
-A zone_guestzone_helper -p udp -m comment --comment "!fw3: SNMP monitoring connection tracking" -m udp --dport 161 -j CT --helper snmp
-A zone_guestzone_helper -p udp -m comment --comment "!fw3: TFTP connection tracking" -m udp --dport 69 -j CT --helper tftp
-A zone_lan_helper -p udp -m comment --comment "!fw3: Amanda backup and archiving proto" -m udp --dport 10080 -j CT --helper amanda
-A zone_lan_helper -p tcp -m comment --comment "!fw3: FTP passive connection tracking" -m tcp --dport 21 -j CT --helper ftp
-A zone_lan_helper -p udp -m comment --comment "!fw3: RAS proto tracking" -m udp --dport 1719 -j CT --helper RAS
-A zone_lan_helper -p tcp -m comment --comment "!fw3: Q.931 proto tracking" -m tcp --dport 1720 -j CT --helper Q.931
-A zone_lan_helper -p tcp -m comment --comment "!fw3: IRC DCC connection tracking" -m tcp --dport 6667 -j CT --helper irc
-A zone_lan_helper -p tcp -m comment --comment "!fw3: PPTP VPN connection tracking" -m tcp --dport 1723 -j CT --helper pptp
-A zone_lan_helper -p tcp -m comment --comment "!fw3: SIP VoIP connection tracking" -m tcp --dport 5060 -j CT --helper sip
-A zone_lan_helper -p udp -m comment --comment "!fw3: SIP VoIP connection tracking" -m udp --dport 5060 -j CT --helper sip
-A zone_lan_helper -p udp -m comment --comment "!fw3: SNMP monitoring connection tracking" -m udp --dport 161 -j CT --helper snmp
-A zone_lan_helper -p udp -m comment --comment "!fw3: TFTP connection tracking" -m udp --dport 69 -j CT --helper tftp
COMMIT
# Completed on Fri Mar 18 16:09:16 2022
# Generated by iptables-save v1.8.3 on Fri Mar 18 16:09:16 2022
*mangle
:PREROUTING ACCEPT [5331:571796]
:INPUT ACCEPT [1693:232880]
:FORWARD ACCEPT [3198:192007]
:OUTPUT ACCEPT [4793:489981]
:POSTROUTING ACCEPT [4761:488071]
:mwan3_connected - [0:0]
:mwan3_hook - [0:0]
:mwan3_iface_in_wan - [0:0]
:mwan3_ifaces_in - [0:0]
:mwan3_policy_default_poli - [0:0]
:mwan3_rules - [0:0]
-A PREROUTING -j mwan3_hook
-A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -o wg0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone OVPN MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A FORWARD -i wg0 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone OVPN MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
-A OUTPUT -j mwan3_hook
-A mwan3_connected -m set --match-set mwan3_connected dst -j MARK --set-xmark 0x3f00/0x3f00
-A mwan3_hook -j CONNMARK --restore-mark --nfmask 0x3f00 --ctmask 0x3f00
-A mwan3_hook -m mark --mark 0x0/0x3f00 -j mwan3_ifaces_in
-A mwan3_hook -m mark --mark 0x0/0x3f00 -j mwan3_connected
-A mwan3_hook -m mark --mark 0x0/0x3f00 -j mwan3_rules
-A mwan3_hook -j CONNMARK --save-mark --nfmask 0x3f00 --ctmask 0x3f00
-A mwan3_hook -m mark ! --mark 0x3f00/0x3f00 -j mwan3_connected
-A mwan3_iface_in_wan -i eth0.2 -m set --match-set mwan3_connected src -m mark --mark 0x0/0x3f00 -m comment --comment default -j MARK --set-xmark 0x3f00/0x3f00
-A mwan3_iface_in_wan -i eth0.2 -m mark --mark 0x0/0x3f00 -m comment --comment wan -j MARK --set-xmark 0x100/0x3f00
-A mwan3_ifaces_in -m mark --mark 0x0/0x3f00 -j mwan3_iface_in_wan
-A mwan3_policy_default_poli -m mark --mark 0x0/0x3f00 -m comment --comment "wan 3 3" -j MARK --set-xmark 0x100/0x3f00
-A mwan3_rules -m mark --mark 0x0/0x3f00 -m comment --comment default_rule -j mwan3_policy_default_poli
COMMIT
# Completed on Fri Mar 18 16:09:16 2022
# Generated by iptables-save v1.8.3 on Fri Mar 18 16:09:16 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:GL_SPEC_OPENING - [0:0]
:forwarding_guestzone_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_guestzone_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_guestzone_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_OVPN_dest_ACCEPT - [0:0]
:zone_OVPN_dest_REJECT - [0:0]
:zone_OVPN_forward - [0:0]
:zone_OVPN_input - [0:0]
:zone_OVPN_output - [0:0]
:zone_OVPN_src_REJECT - [0:0]
:zone_guestzone_dest_ACCEPT - [0:0]
:zone_guestzone_dest_REJECT - [0:0]
:zone_guestzone_forward - [0:0]
:zone_guestzone_input - [0:0]
:zone_guestzone_output - [0:0]
:zone_guestzone_src_REJECT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
-A INPUT -j GL_SPEC_OPENING
-A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
-A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
-A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
-A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
-A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
-A INPUT -i wg0 -m comment --comment "!fw3" -j zone_OVPN_input
-A INPUT -i br-guest -m comment --comment "!fw3" -j zone_guestzone_input
-A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
-A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD --hw
-A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
-A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
-A FORWARD -i wg0 -m comment --comment "!fw3" -j zone_OVPN_forward
-A FORWARD -i br-guest -m comment --comment "!fw3" -j zone_guestzone_forward
-A FORWARD -m comment --comment "!fw3" -j reject
-A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
-A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
-A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
-A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
-A OUTPUT -o wg0 -m comment --comment "!fw3" -j zone_OVPN_output
-A OUTPUT -o br-guest -m comment --comment "!fw3" -j zone_guestzone_output
-A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
-A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
-A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
-A syn_flood -m comment --comment "!fw3" -j DROP
-A zone_OVPN_dest_ACCEPT -o wg0 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_OVPN_dest_ACCEPT -o wg0 -m comment --comment "!fw3" -j ACCEPT
-A zone_OVPN_dest_REJECT -o wg0 -m comment --comment "!fw3" -j reject
-A zone_OVPN_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_OVPN_forward -m comment --comment "!fw3" -j zone_OVPN_dest_REJECT
-A zone_OVPN_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_OVPN_input -m comment --comment "!fw3" -j zone_OVPN_src_REJECT
-A zone_OVPN_output -m comment --comment "!fw3" -j zone_OVPN_dest_ACCEPT
-A zone_OVPN_src_REJECT -i wg0 -m comment --comment "!fw3" -j reject
-A zone_guestzone_dest_ACCEPT -o br-guest -m comment --comment "!fw3" -j ACCEPT
-A zone_guestzone_dest_REJECT -o br-guest -m comment --comment "!fw3" -j reject
-A zone_guestzone_forward -m comment --comment "!fw3: Custom guestzone forwarding rule chain" -j forwarding_guestzone_rule
-A zone_guestzone_forward -m comment --comment "!fw3: Zone guestzone to wan forwarding policy" -j zone_wan_dest_ACCEPT
-A zone_guestzone_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_guestzone_forward -m comment --comment "!fw3" -j zone_guestzone_dest_REJECT
-A zone_guestzone_input -m comment --comment "!fw3: Custom guestzone input rule chain" -j input_guestzone_rule
-A zone_guestzone_input -p udp -m udp --dport 67:68 -m comment --comment "!fw3: guestzone_DHCP" -j ACCEPT
-A zone_guestzone_input -p tcp -m tcp --dport 53 -m comment --comment "!fw3: guestzone_DNS" -j ACCEPT
-A zone_guestzone_input -p udp -m udp --dport 53 -m comment --comment "!fw3: guestzone_DNS" -j ACCEPT
-A zone_guestzone_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_guestzone_input -m comment --comment "!fw3" -j zone_guestzone_src_REJECT
-A zone_guestzone_output -m comment --comment "!fw3: Custom guestzone output rule chain" -j output_guestzone_rule
-A zone_guestzone_output -m comment --comment "!fw3" -j zone_guestzone_dest_ACCEPT
-A zone_guestzone_src_REJECT -i br-guest -m comment --comment "!fw3" -j reject
-A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
-A zone_lan_forward -m comment --comment "!fw3: Zone lan to OVPN forwarding policy" -j zone_OVPN_dest_ACCEPT
-A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
-A zone_lan_input -p tcp -m tcp --dport 137 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p tcp -m tcp --dport 138 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p tcp -m tcp --dport 139 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p tcp -m tcp --dport 445 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p udp -m udp --dport 137 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p udp -m udp --dport 138 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p udp -m udp --dport 139 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -p udp -m udp --dport 445 -m comment --comment "!fw3: @rule[12]" -j ACCEPT
-A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
-A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
-A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
-A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
-A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
-A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
-A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
-A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
-A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
-A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
-A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
-A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
-A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
-A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
-A zone_wan_input -p tcp -m tcp --dport 137 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p tcp -m tcp --dport 138 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p tcp -m tcp --dport 139 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p tcp -m tcp --dport 445 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p udp -m udp --dport 137 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p udp -m udp --dport 138 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p udp -m udp --dport 139 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -p udp -m udp --dport 445 -m comment --comment "!fw3: @rule[11]" -j DROP
-A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
-A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
-A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
-A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
-A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Fri Mar 18 16:09:16 2022
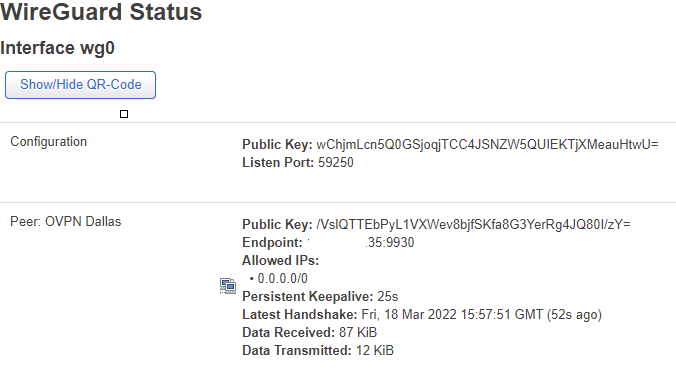
interface: wg0
public key: wChjmLcn5Q0GSjoqjTCC4JSNZW5QUIEKTjXMeauHtwU=
private key: (hidden)
listening port: 59250
peer: /VslQTTEbPyL1VXWev8bjfSKfa8G3YerRg4JQ80I/zY=
endpoint: 194.37.97.35:9930
allowed ips: 0.0.0.0/0
latest handshake: 49 seconds ago
transfer: 87.64 KiB received, 17.20 KiB sent
persistent keepalive: every 25 seconds
root@GL-MT1300:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option flow_offloading '1'
option flow_offloading_hw '1'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config zone
option network 'wg0'
option forward 'REJECT'
option name 'OVPN'
option output 'ACCEPT'
option input 'REJECT'
option masq '1'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
option reload '1'
config include 'gls2s'
option type 'script'
option path '/var/etc/gls2s.include'
option reload '1'
config include 'glfw'
option type 'script'
option path '/usr/bin/glfw.sh'
option reload '1'
config include 'glqos'
option type 'script'
option path '/usr/sbin/glqos.sh'
option reload '1'
config zone 'guestzone'
option name 'guestzone'
option network 'guest'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
config forwarding 'guestzone_fwd'
option src 'guestzone'
option dest 'wan'
config rule 'guestzone_dhcp'
option name 'guestzone_DHCP'
option src 'guestzone'
option target 'ACCEPT'
option proto 'udp'
option dest_port '67-68'
config rule 'guestzone_dns'
option name 'guestzone_DNS'
option src 'guestzone'
option target 'ACCEPT'
option proto 'tcp udp'
option dest_port '53'
config rule 'sambasharewan'
option src 'wan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'DROP'
config rule 'sambasharelan'
option src 'lan'
option dest_port '137 138 139 445'
option dest_proto 'tcpudp'
option target 'ACCEPT'
config forwarding
option dest 'OVPN'
option src 'lan'