I have posted previous related queries on this device/setup, and have received amazing assistance from the forum on those topics. Those items have each been individually sorted out, and this is the next stage.
I would like to just check if I'm headed (conceptually) in the right direction.
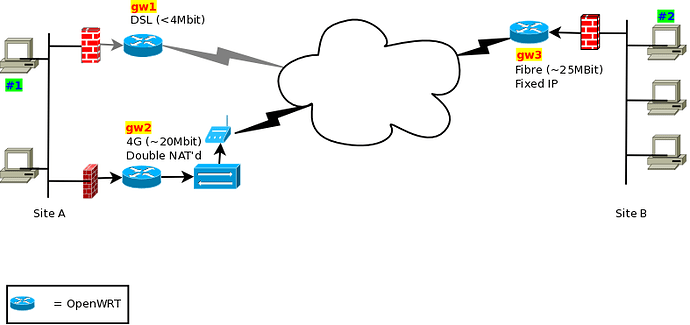
I have a double NAT'd USB LTE stick in an rpi3 device as WAN. I am told that rain(ISP) does not assign IP addresses to client devices (I don't know how anything works this way, but that's a discussion for elsewhere I guess) so "port forwarding is not possible". I do, however, need to get into the LAN from WAN side. The basic layout looks something like this (sorry the pic is created in dia, so the pics etc are kinda old)...
#Description:____________________________________________________________________
Site A: I currently have 2 OpenWRT pi's
- gw1 (192.168.1.1/25)- via DSL (LAN to eth0 and WAN via USB eth)
- reachable on various levels via port forwards
- also via wireguard VPN (site-2-site 192.168.1.0/25 <- -> 192.168.1.128/25)
- ssh port 2201 is open on firewall
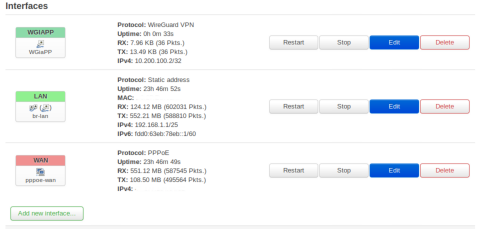
- gw2 (192.168.1.2/25) - via 4G/LTE usb modem huawei e3772h-320 (I have tried several possibilities to get past the double-NAT but this particular model does not allow usbmode adjustments, so it is in RNDIS mode and working fine except for the WAN inward access).
- ssh port 2202 is open on firewall
- I have not yet configured the WG here
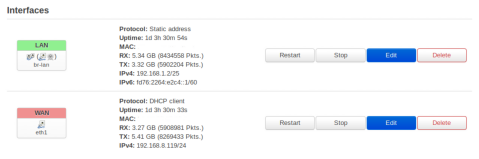
I have set up different routes on the LAN machines to use the speed of the 4G line if possible
- gw1 for everything
vs - gw2 for WAN traffic and gw1 for WG/LAN traffic
#Description:____________________________________________________________________
Site B: Here there is just 1 OpenWRT x86_64 PC
- gw3 (192.168.1.254/25) - via Fibre (LAN to eth0 and WAN via eth1)
- reachable on various levels via port forwards
- also via wireguard VPN (site-2-site 192.168.1.0/25 <- -> 192.168.1.128/25)
- this side I have 1 fixed IP
- ssh port 2203 is open on firewall
The above works OK in general, but, for example, when I try to sync my NextCloud to the instance on Site A, it can't be found (from outside/site B). If I initiate a connection from NextCloud to a device on the site A LAN (which has the fixed IP gw3), then the sync kicks in, but (for reasons unknown to me) by default it is not activate.
In addition, the speed on the DSL connection is very poor, so even if it was working, it is too slow.
I want to be able to access
• everything on site A from site B via the 4G link.
• some things on site A from WAN side (also via 4G link).
I plan to try tunnels to achieve this, but I am not quite sure at which level I should do so (PC-PC, LAN-LAN,gw-gw?).
I have looked at this post - and the concept seems to be viable. If anyone can advise me which of these is best/correct (if any)...
should I create
1. A tunnel into which the WG is channelled
for example, if I am using WG, with the listener on eg. port 3456
- an outgoing tunnel site A -> site B for WG
- on the OpenWRT(siteA:gw2) -> OpenWRT(siteB:gw3)
- ssh -R 3456:openwrtGW3-siteB.fixed.ip:3456 root@openwrt.fixed.ip -p 2203
- on the OpenWRT(siteB:gw3)
- endpoint for WG is then 127.0.0.1:3456 ?
- Then use WG for the site-2-site (open 3456 on firewall rules), something like...
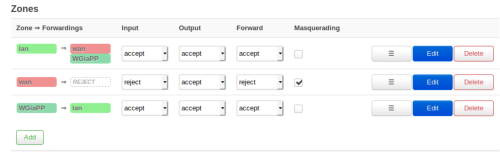
- on the OpenWRT(siteA:gw2) -> OpenWRT(siteB:gw3)
2. A tunnel per PortForward
or will it be better to create 1x “-R” tunnel per required port forward from Site A (to Site B)?
for example...
- if NextCloud is on say 192.168.1.130/25 port 443
- ssh -R 13443:openwrtGW3-siteB.fixed.ip:443 root@openwrt.fixed.ip -p 2203
- accessed via https://openwrtGW3-siteA.fixed.ip:13443 ?? with a port forward from “this device/WAN”:13443 -> 192.168.1.130:443
3. A tunnel per Host/Server
or would I need to create the outgoing tunnel for/at the actual host/server station?
- NextCloud machine (which is on say 192.168.1.130/25) creates a tunnel to external gw3,
- ssh -R 13443:openwrtGW3-siteB.fixed.ip:443 root@openwrt.fixed.ip -p 2203
- LAN stations on site B would access this via https://openwrtGW3-siteA.LAN.ip:13443 ??
Not sure if the explanations and theories are clear, but I will try to offer some 1-liners below...
To allow #2 to reach #1, is the tunnel created...
- #1 -> #2 (and then #2 connecting via localhost)
- #1 -> gw3 (with #2 connecting via gw3 with a port forward)
- gw2 -> gw3 (with a port forwards on both gw2/gw3)
- some other config that is above my pay grade?
Last part...
- WG uses UDP, while SSH is TCP. Would this have any affect in terms of tunneling UDP within TCP?
- Would it be advisable to use MoSH instead of SSH (since it is UDP), and is there any increased risk (in terms of UDP openings at the firewall) this way?


 - I didn't have the right PSK on the client/peer machine. As soon as I corrected that, everything worked perfectly.
- I didn't have the right PSK on the client/peer machine. As soon as I corrected that, everything worked perfectly.