Hi all,
I hope someone could assist me with some firewall and/or routing troubleshooting. I am trying to define 3 internal zones (each with their own distinct bridge device and interface):
- LAN (br-lan). Zone name:
lan - IOT (br-iot). Zone name:
iot - LVP (br-lan-vpn). Zone name:
lan_vpn
Furthermore I have the following 2 devices for access to the internet:
- WAN (eth0.2). Zone name:
wan - VPN (tun0). Zone name:
wan_vpn
I want devices from lan to be able to access zones: iot, lan_vpn, wan
I want devices from lan_vpn to be able to access zones: iot, lan, wan_vpn
I want devices from iot to be able to access zones: wan_vpn
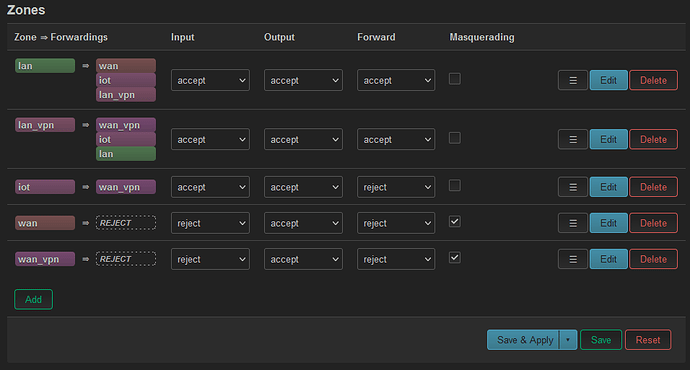
I have defined the firewall zones as shown here:
To be able to reach the internet from iot and lan_vpn over the wan_vpn zone, I need to override the default gateway for those routes. So I have defined the following routing rules:
config route
option interface 'vpn'
option target '0.0.0.0/0'
option table '10'
config rule
option in 'iot'
option lookup '10'
config rule
option in 'lvp'
option lookup '10'
Most of what I want is working. However, at this point I have no access from zone lan to iot or lan_vpn. I also have no access from lan_vpn to iot or lan.
I have tried different routing techniques, and with the following routes I am able to access zones iot and lan_vpn from lan, and zone iot from lan_vpn:
config rule
option in 'iot'
option dest '192.168.0.0/16'
option lookup 'main'
config rule
option in 'lvp'
option lookup 'main'
option dest '192.168.0.0/16'
Although I must admit, I'm not really sure, what I am doing with the rules above. What is still not working is from zone lan_vpn to lan.
Could someone assist me in getting access from lan_vpn to lan?
For completeness sake, I am attaching my network and firewall configs:
/etc/config/network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdf7:82cb:7fdb::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1.1'
option ipv6 '0'
config device
option name 'eth1.1'
option macaddr '58:ef:68:2d:4d:f0'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth0.2'
option macaddr '58:ef:68:2d:4d:f0'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '3 4 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 5'
option vid '2'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '1 6t'
option vid '3'
config device
option type 'bridge'
option name 'br-iot'
option ipv6 '0'
list ports 'eth1.3'
config interface 'iot'
option proto 'static'
option device 'br-iot'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option delegate '0'
config device
option name 'eth1.3'
option type '8021q'
option ifname 'eth1'
option vid '3'
option ipv6 '0'
config switch_vlan
option device 'switch0'
option vlan '4'
option ports '2 6t'
option vid '4'
config device
option type 'bridge'
option name 'br-lan-vpn'
list ports 'eth1.4'
option ipv6 '0'
config interface 'lvp'
option proto 'static'
option device 'br-lan-vpn'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
config interface 'vpn'
option device 'tun0'
option proto 'none'
config route
option interface 'vpn'
option target '0.0.0.0/0'
option table '10'
config rule
option in 'iot'
option dest '192.168.0.0/16'
option lookup 'main'
config rule
option in 'lvp'
option lookup 'main'
option dest '192.168.0.0/16'
config rule
option in 'iot'
option lookup '10'
config rule
option in 'lvp'
option lookup '10'
/etc/config/firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'lan_vpn'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'lvp'
option forward 'ACCEPT'
config zone
option name 'iot'
option output 'ACCEPT'
option forward 'REJECT'
option input 'ACCEPT'
list network 'iot'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'wan_vpn'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'vpn'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'iot'
option dest 'wan_vpn'
config forwarding
option src 'lan'
option dest 'iot'
config forwarding
option src 'lan_vpn'
option dest 'wan_vpn'
config forwarding
option src 'lan'
option dest 'lan_vpn'
config forwarding
option src 'lan_vpn'
option dest 'iot'
config forwarding
option src 'lan_vpn'
option dest 'lan'