Hi friends,
I have been frustrated working on this issue for over five days now, and despite my best efforts, I am unable to find a resolution. Having thoroughly researched guides, YouTube videos, and forum posts, I've reached a point where I feel it's necessary to turn to the community for assistance.
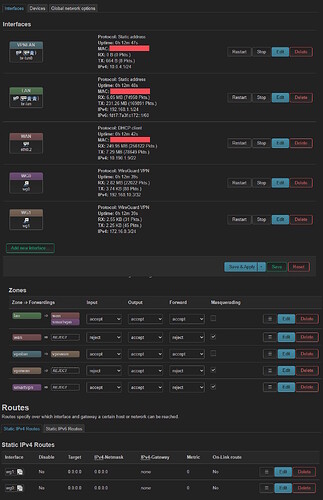
This is currently my setup. The VPNLAN and WG1 interfaces are connected and provide a separate internet connection over a Wi-Fi network that I can access on my Nintendo switch. This network works fine and can be ignored (no issues).
Picture for Router is Below
The issue I'm having is with my WG0 interface. I'm trying to create something called a "bounce server"
- “Router” - The machine that will serve as the gateway (inwards) to your LAN
- “Server” - The machine with a publicly accessible IP that all clients will connect to. Also known as a “Bounce Server”
- “Client” - You, trying to connect to your LAN remotely somewhere
Here's the guide I followed: Remote LAN access with WireGuard (laroberto.com)
In case you're wondering why I haven't opted for port forwarding, it's because I'm behind a NAT in my apartment complex, which prevents me from doing so. Moreover, employing this alternative method offers security benefits that I'd like to capitalize on.
The problem arises when I attempt to permit the 192.168.1.0/24 subnet as an Allowed IP through my WG0 interface. This action results in my router crashing and losing access to it. I suspect that this issue may be related to configuring split tunneling, which I believe needs to be set up (I'm unsure of how to do this).
The interesting part about this whole issue is that whenever I add 0.0.0.0/0 to the Allowed IPs in the WG0 interface and create a static route of
target: 0.0.0.0
IPv4-Netmask: 0.0.0.0
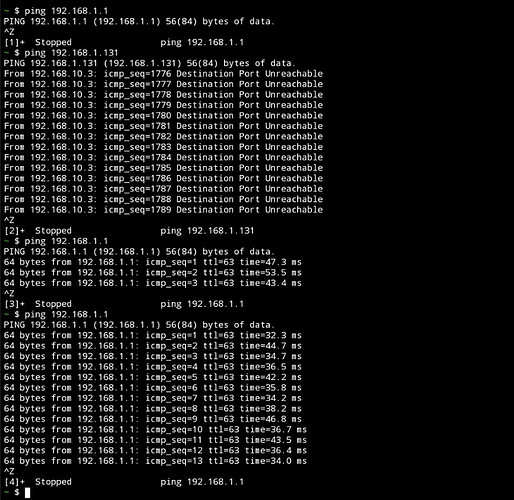
I can successfully ping my router's interface at 192.168.1.1 and access the OpenWRT homepage through the Wireguard tunnel established on my phone, all without losing my internet connection. This progress brings me closer to my ultimate objective; however, I require assistance in gaining access to the other local IPs without compromising my LAN internet connection.
Pings:
Thank you. I hope someone is able to help me with this issue.
Edit: I made some changes and added 192.168.1.0/24 to my allowed ips list for WG0 and changed the Input from accept to reject in the firewall for smartvpn but I now can't ping 192.168.1.1