balumba
October 23, 2023, 10:56pm
1
Well, there're several topic - some solved - those describe this problem.
I'm running an OpenWRT router as client connected to an OpenVPN server (my VPS) in the internet.
This is what I want:
Unfortunately I'm not able to ping from the right side to any device behind the router on the left side.
Some configs:
On the VPS side:
# server.conf
server 10.8.0.0 255.255.255.0
route 192.168.11.0 255.255.255.0
push "route 192.168.11.0 255.255.255.0"
client-to-client
client-config-dir /etc/openvpn/ccd
# ccd/router
iroute 192.168.11.0 255.255.255.0
-------------------------
On the router:
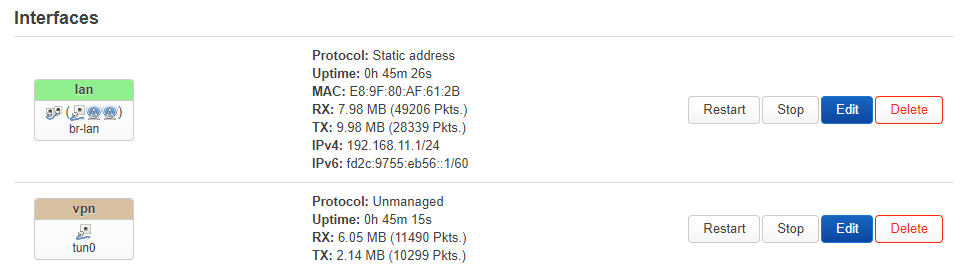
# /etc/config/network
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.11.1'
config interface 'vpn'
option proto 'none'
option device 'tun0'
# /etc/config/firewall
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
option masq '1'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
config zone
option name 'vpn'
option output 'ACCEPT'
option masq '1'
list network 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
This looks loke here:
Any hints how to get this working (to be able to ping fom a VPN client outside my LAN into my LAN)?
Your lan should not have masquerading enabled. Turn that off, restart, and try again.
balumba
October 23, 2023, 11:26pm
3
Thanks for that.
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
Collect the log from the VPN server when connecting the router.
balumba
October 23, 2023, 11:44pm
5
Server logs:
2023-10-23 23:42:40 37.63.23.167:15059 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2023-10-23 23:42:40 37.63.23.167:15059 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2023-10-23 23:42:40 37.63.23.167:15059 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2023-10-23 23:42:40 37.63.23.167:15059 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2023-10-23 23:42:40 37.63.23.167:15059 TLS: Initial packet from [AF_INET]37.63.23.167:15059, sid=ffed303a 0db9c5a5
2023-10-23 23:42:40 37.63.23.167:15059 VERIFY OK: depth=1, CN=cn_iVOkpGys9uqRg6MF
2023-10-23 23:42:40 37.63.23.167:15059 VERIFY OK: depth=0, CN=router
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_VER=2.5.7
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_PLAT=linux
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_PROTO=6
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_NCP=2
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_CIPHERS=AES-256-GCM:AES-128-GCM
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_LZ4=1
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_LZ4v2=1
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_LZO=1
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_COMP_STUB=1
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_COMP_STUBv2=1
2023-10-23 23:42:40 37.63.23.167:15059 peer info: IV_TCPNL=1
2023-10-23 23:42:40 37.63.23.167:15059 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, 256 bit EC, curve: prime256v1
2023-10-23 23:42:40 37.63.23.167:15059 [router] Peer Connection Initiated with [AF_INET]37.63.23.167:15059
2023-10-23 23:42:40 router/37.63.23.167:15059 MULTI_sva: pool returned IPv4=10.8.0.2, IPv6=(Not enabled)
2023-10-23 23:42:40 router/37.63.23.167:15059 OPTIONS IMPORT: reading client specific options from: /etc/openvpn/ccd/router
2023-10-23 23:42:40 router/37.63.23.167:15059 MULTI: Learn: 10.8.0.2 -> router/37.63.23.167:15059
2023-10-23 23:42:40 router/37.63.23.167:15059 MULTI: primary virtual IP for router/37.63.23.167:15059: 10.8.0.2
2023-10-23 23:42:40 router/37.63.23.167:15059 MULTI: internal route 192.168.11.0/24 -> router/37.63.23.167:15059
2023-10-23 23:42:40 router/37.63.23.167:15059 MULTI: Learn: 192.168.11.0/24 -> router/37.63.23.167:15059
2023-10-23 23:42:40 router/37.63.23.167:15059 REMOVE PUSH ROUTE: 'route 192.168.11.0 255.255.255.0'
2023-10-23 23:42:40 router/37.63.23.167:15059 Outgoing Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
2023-10-23 23:42:40 router/37.63.23.167:15059 Incoming Data Channel: Cipher 'AES-128-GCM' initialized with 128 bit key
2023-10-23 23:42:40 router/37.63.23.167:15059 SENT CONTROL [router]: 'PUSH_REPLY,dhcp-option DNS 94.140.14.14,dhcp-option DNS 94.140.15.15,redirect-gateway def1 bypass-dhcp,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.8.0.2 255.255.255.0,peer-id 0,cipher AES-128-GCM' (status=1)
1 Like
Check runtime settings on the server including firewall ruleset, routing tables and rules, IP forwarding.
balumba
October 24, 2023, 12:04am
7
I don't think this is anything on the server.
On the router:
$ service firewall stop
From any other device outside my LAN now:
$ ping 192.168.11.170
-> This is working now
On the router:
$ service firewall start
Now I'm no longer able to ping
Sorry, have you removed blank lines between sections?
Well, just removed to copy/paste here, but I was not aware that this could confuse.
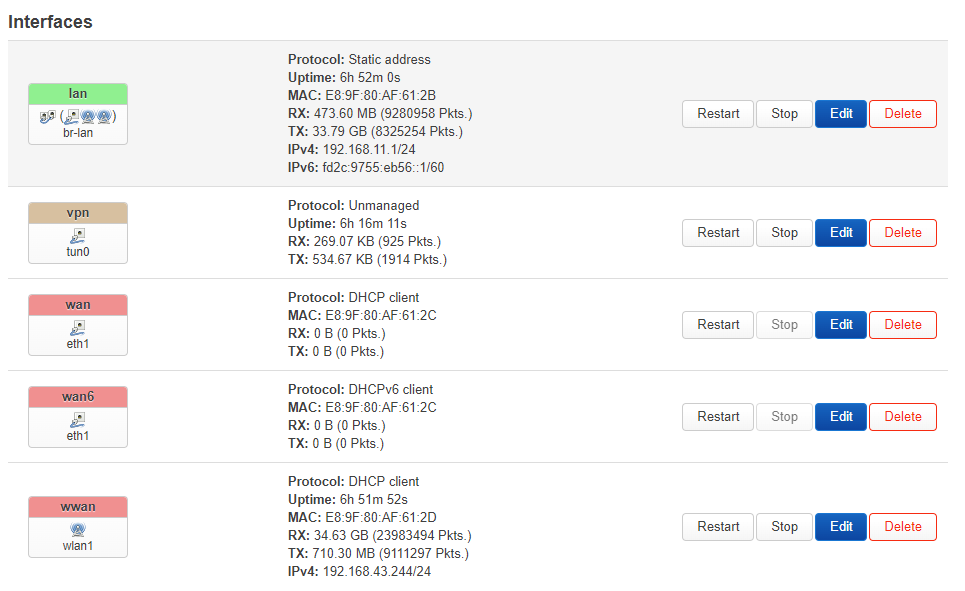
# /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd2c:9755:eb56::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.11.1'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 0'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '5 0'
config interface 'wwan'
option proto 'dhcp'
config interface 'vpn'
option proto 'none'
option device 'tun0'
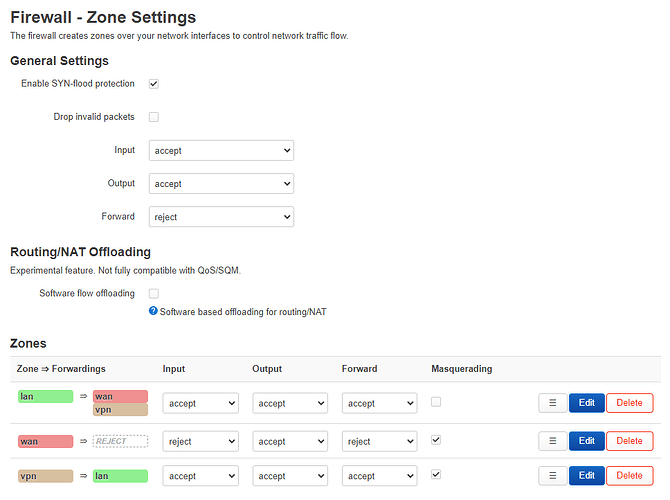
# /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option output 'ACCEPT'
option masq '1'
list network 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'vpn'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/pbr.firewall.include'
config forwarding
option src 'vpn'
option dest 'lan'
_bernd
October 24, 2023, 6:21am
10
Please don't recommend masquerade! There is a reason why we have routing! You just need proper routes on both sides and a firewall rule which allowed traffic from both directions. But there is no $$$$ing reason to use masquerade or any other kind of NAT in such a scenario.
ulmwind
October 24, 2023, 6:34am
11
OK, please, repeat test above with LAN IP: 192.168.11.1
Please, in firewall configuration place zone section after zone, and forwarding section after forwarding.
balumba
October 24, 2023, 6:45am
12
Please, in firewall configuration place zone section after zone, and forwarding section after forwarding.
Changed my config (hopefully that is what you mean):
# /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
config zone
option name 'vpn'
option output 'ACCEPT'
list network 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
config rule
[...]
OK, please, repeat test above with LAN IP: 192.168.11.1
Yes, I can ping the router itself from a computer outside my LAN.
balumba
October 24, 2023, 7:48am
13
Ha, I got it!
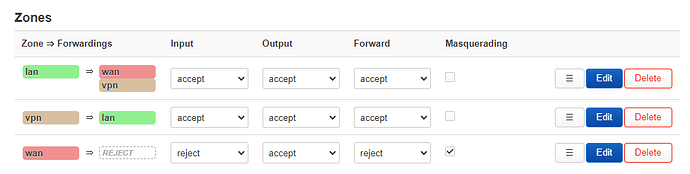
# /etc/config/firewall
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'vpn'
option output 'ACCEPT'
list network 'vpn'
option input 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
[...]
I was specifically saying that masquerading should not be enabled on the lan zone. Please reread my statement.
egc
October 24, 2023, 11:37am
15
For a site-to-site setup you can just add the tun interface to the LAN zone and Bob is your uncle (the LAN zone does not Masquerade normally
Maybe you are pushing the wrong route, you are pushing the route of the router and you should push a route to the LAN of the VPS
_bernd
October 24, 2023, 12:34pm
16
pardon. Maybe I should have finished my first coffee first
system
November 3, 2023, 12:34pm
17
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.