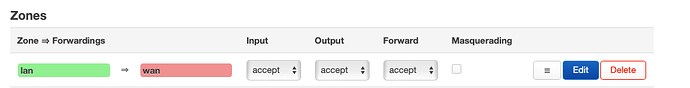
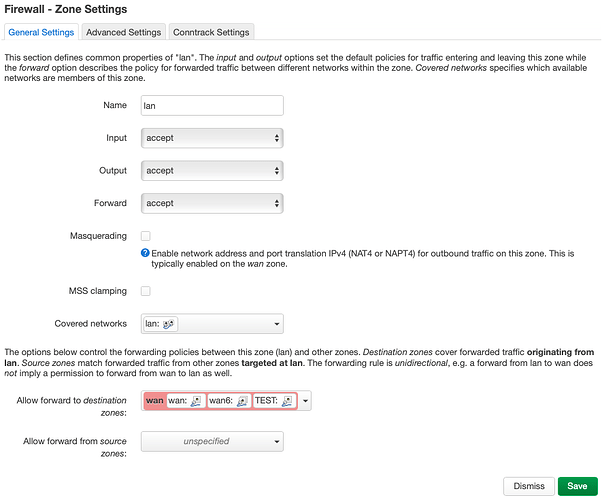
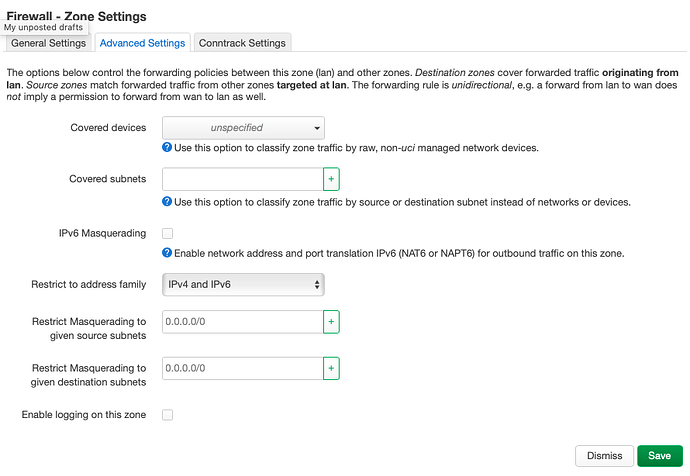
We already established:
- DNAT / port forwarding is working from WAN to LAN.
- Associated hairpin settings look correct.
- I am expecting these settings to not be an issue (for now)
There is no prohibiting rules forward chain (except the OpenWRT's defaults policy)
$ nft list ruleset | grep forward | grep -v "LAN_"
chain forward {
type filter hook forward priority filter; policy drop;
ct state established,related accept comment "!fw4: Allow forwarded established and related flows"
iifname "br-lan" jump forward_lan comment "!fw4: Handle lan IPv4/IPv6 forward traffic"
iifname { "eth0", "pppoe-wan" } jump forward_wan comment "!fw4: Handle wan IPv4/IPv6 forward traffic"
chain forward_lan {
jump accept_to_wan comment "!fw4: Accept lan to wan forwarding"
ct status dnat accept comment "!fw4: Accept port forwards"
chain forward_wan {
ct status dnat accept comment "!fw4: Accept port forwards"
ct status dnat accept comment "!fw4: Accept port forwards"
ct status dnat accept comment "!fw4: Accept port forwards"
chain mangle_forward {
type filter hook forward priority mangle; policy accept;
The router defines other zones named LAN_xxx such as for example LAN_IOT:
- Each zone is in a different
VLAN ID. That's why I removed them from the command output
lan has the "default" VLAN ID and the forward ruleset for it is displayed.
iptables (legacy) is installed, yet I don't recall explicitly installing it.
Both iptables binary version are the same.
$ iptables --version
iptables v1.8.8 (legacy)
$ iptables-legacy --version
iptables v1.8.8 (legacy)
Here are iptables binaries list.
$ ip<Tab>
ip ip6tables-legacy-restore ip6tables-save iptables iptables-legacy-save
ip6tables ip6tables-legacy-save ipcalc.sh iptables-legacy iptables-restore
ip6tables-legacy ip6tables-restore iperf3 iptables-legacy-restore iptables-save
$ ls -alh /usr/sbin/iptables
lrwxrwxrwx 1 root root 30 Nov 14 21:38 /usr/sbin/iptables -> /usr/sbin/xtables-legacy-multi
$ ls -alh /usr/sbin/iptables-legacy
lrwxrwxrwx 1 root root 20 Nov 14 21:38 /usr/sbin/iptables-legacy -> xtables-legacy-multi
xtables-legacy-multi is installed by package iptables-zz-legacy (commit)
I am not quite sure if the command below show package the user installed explicitly.
$opkg list-installed | grep "iptables"
ptables-mod-extra - 1.8.8-2
iptables-mod-ipopt - 1.8.8-2
iptables-zz-legacy - 1.8.8-2
Here are the packages depending on iptables instead of the nftables package, along with the status per package found
$ grep -E "Depends" /usr/lib/opkg/info/*.control | grep "iptables" | grep -v ".*iptables-mod-.*:.*"
> User installed packages.
/usr/lib/opkg/info/dockerd.control:Depends: libc, ca-certificates, containerd, iptables, iptables-mod-extra, ip6tables, kmod-ipt-nat6, libseccomp, kmod-ipt-nat, kmod-ipt-physdev, kmod-nf-ipvs, kmod-veth, tini, uci-firewall.
/usr/lib/opkg/info/fwknopd.control:Depends: libc, iptables, libfko, libpcap1
> Not installed manually:
/usr/lib/opkg/info/iptables-zz-legacy.control:Depends: libc, xtables-legacy
> Installed via luci-app-sqm:
/usr/lib/opkg/info/sqm-scripts.control:Depends: libc, tc, kmod-sched-cake, kmod-ifb, iptables, iptables-mod-ipopt
I uninstalled all packages listed above:
opkg remove fwknopd sqm-scripts dockerd iptables-zz-legacy --force-removal-of-dependent-packages
I rebooted OpenWRT device.
reboot
I can now reach http(s)://service.com from LAN (and reaching from WAN is still working as expected):
wget http(s)://service.com
...
HTTP request sent, awaiting response...
HTTP/1.1 302 Found
I thank you both @lleachii / @pavelgl for the instructions and intuition / experience to guide me through this.
Now the fun starts: which package (out of 4 uninstalled packages) caused srcnat rules not to be hit.
- luci-app-sqm (sqm-scripts): Installed + http(s)://service.com accessible from LAN
- dockerd: Installed + http(s)://service.com not accessible from LAN
- fknowpd: not tested
![]() )
)