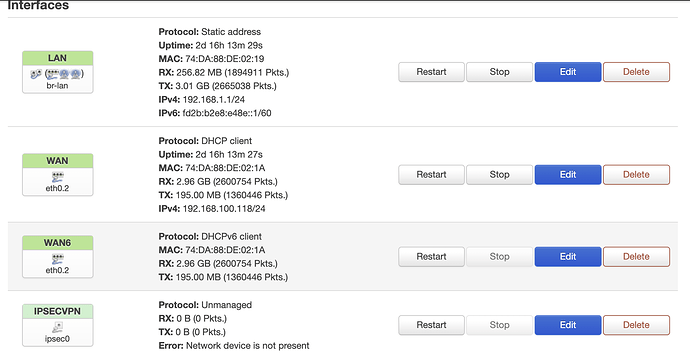
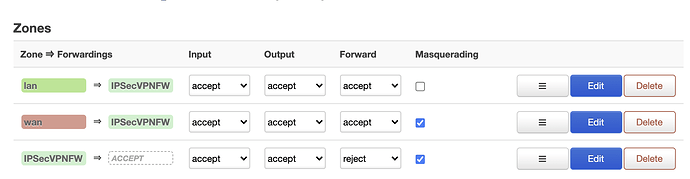
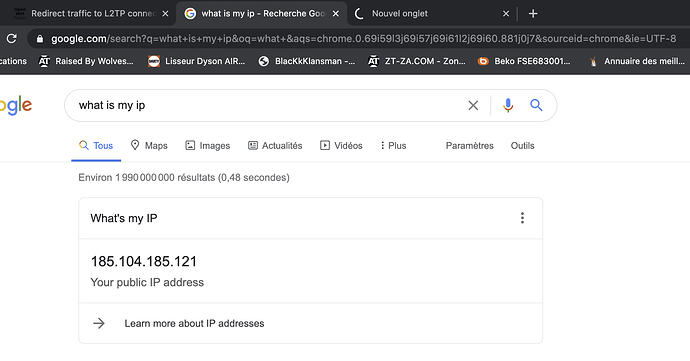
And when i try with pptp i have that:
Sun Sep 6 13:17:28 2020 daemon.info pppd[13673]: Plugin pptp.so loaded.
Sun Sep 6 13:17:28 2020 daemon.info pppd[13673]: PPTP plugin version 1.00
Sun Sep 6 13:17:28 2020 daemon.notice pppd[13673]: pppd 2.4.7 started by root, uid 0
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13674]: pptp: call manager for 185.104.185.124
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13674]: window size: 50
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13674]: call id: 116
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13674]: control connection
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13674]: unix_sock
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13675]: Sent control packet type is 1 'Start-Control-Connection-Request'
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13675]: Received Start Control Connection Reply
Sun Sep 6 13:17:28 2020 daemon.debug pppd[13675]: Client connection established.
Sun Sep 6 13:17:29 2020 daemon.debug pppd[13675]: Sent control packet type is 7 'Outgoing-Call-Request'
Sun Sep 6 13:17:29 2020 daemon.debug pppd[13675]: Received Outgoing Call Reply.
Sun Sep 6 13:17:29 2020 daemon.debug pppd[13675]: Outgoing call established (call ID 116, peer's call ID 56448).
Sun Sep 6 13:17:29 2020 daemon.debug pppd[13673]: using channel 116
Sun Sep 6 13:17:29 2020 kern.info kernel: [ 3635.007787] pptp-ExpressVPN: renamed from ppp0
Sun Sep 6 13:17:29 2020 daemon.info pppd[13673]: Renamed interface ppp0 to pptp-ExpressVPN
Sun Sep 6 13:17:29 2020 daemon.info pppd[13673]: Using interface pptp-ExpressVPN
Sun Sep 6 13:17:29 2020 daemon.notice pppd[13673]: Connect: pptp-ExpressVPN <--> pptp (185.104.185.124)
Sun Sep 6 13:17:29 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:32 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:35 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:38 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:41 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:44 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:47 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:50 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:53 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:56 2020 daemon.debug pppd[13673]: sent [LCP ConfReq id=0x1 <asyncmap 0x0> <magic 0xcfeb5fbf>]
Sun Sep 6 13:17:59 2020 daemon.warn pppd[13675]: read returned zero, peer has closed
Sun Sep 6 13:17:59 2020 daemon.debug pppd[13675]: Closing connection (shutdown)
Sun Sep 6 13:17:59 2020 daemon.debug pppd[13675]: Sent control packet type is 12 'Call-Clear-Request'
Sun Sep 6 13:17:59 2020 daemon.warn pppd[13675]: read returned zero, peer has closed
Sun Sep 6 13:17:59 2020 daemon.debug pppd[13675]: Closing connection (call state)
Sun Sep 6 13:17:59 2020 daemon.warn pppd[13673]: LCP: timeout sending Config-Requests
Sun Sep 6 13:17:59 2020 daemon.notice pppd[13673]: Connection terminated.
Sun Sep 6 13:17:59 2020 daemon.notice pppd[13673]: Modem hangup
Sun Sep 6 13:17:59 2020 daemon.info pppd[13673]: Exit.
and:
root@OpenWrt:~# tcpdump -i eth0.2 | grep 185.104.185.124
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0.2, link-type EN10MB (Ethernet), capture size 262144 bytes
13:36:03.502421 IP 192.168.100.118 > 185.104.185.124: GREv1, call 63616, seq 6, length 32: LCP, Conf-Request (0x01), id 1, length 18
13:36:06.505721 IP 192.168.100.118 > 185.104.185.124: GREv1, call 63616, seq 7, length 32: LCP, Conf-Request (0x01), id 1, length 18
13:36:09.509071 IP 192.168.100.118 > 185.104.185.124: GREv1, call 63616, seq 8, length 32: LCP, Conf-Request (0x01), id 1, length 18
13:36:12.512430 IP 192.168.100.118 > 185.104.185.124: GREv1, call 63616, seq 9, length 32: LCP, Conf-Request (0x01), id 1, length 18
13:36:15.515735 IP 192.168.100.118 > 185.104.185.124: GREv1, call 63616, seq 10, length 32: LCP, Conf-Request (0x01), id 1, length 18
13:36:18.431115 IP 185.104.185.124.1723 > 192.168.100.118.46748: Flags [F.], seq 2337381372, ack 3497410056, win 22, options [nop,nop,TS val 2844190802 ecr 3032302489], length 0
13:36:18.431544 IP 192.168.100.118.46748 > 185.104.185.124.1723: Flags [P.], seq 1:17, ack 1, win 1892, options [nop,nop,TS val 3032332474 ecr 2844190802], length 16: pptp CTRL_MSGTYPE=CCRQ CALL_ID(11)
13:36:18.431786 IP 185.104.185.124.1723 > 192.168.100.118.46748: Flags [R], seq 2337381373, win 0, length 0
13:36:18.871686 IP 192.168.100.118.46750 > 185.104.185.124.1723: Flags [S], seq 2759416534, win 29200, options [mss 1460,sackOK,TS val 3032332914 ecr 0,nop,wscale 4], length 0
13:36:18.872014 IP 185.104.185.124.1723 > 192.168.100.118.46750: Flags [S.], seq 1880316010, ack 2759416535, win 43440, options [mss 1460,sackOK,TS val 2844191243 ecr 3032332914,nop,wscale 11], length 0
13:36:18.872170 IP 192.168.100.118.46750 > 185.104.185.124.1723: Flags [.], ack 1, win 1825, options [nop,nop,TS val 3032332915 ecr 2844191243], length 0
13:36:18.874247 IP 192.168.100.118.46750 > 185.104.185.124.1723: Flags [P.], seq 1:157, ack 1, win 1825, options [nop,nop,TS val 3032332917 ecr 2844191243], length 156: pptp CTRL_MSGTYPE=SCCRQ PROTO_VER(1.0) FRAME_CAP(AS) BEARER_CAP(DA) MAX_CHAN(65535) FIRM_REV(1) HOSTNAME(local) VENDOR(cananian)
13:36:18.874497 IP 185.104.185.124.1723 > 192.168.100.118.46750: Flags [.], ack 157, win 22, options [nop,nop,TS val 2844191245 ecr 3032332917], length 0
13:36:19.069159 IP 185.104.185.124.1723 > 192.168.100.118.46750: Flags [P.], seq 1:157, ack 157, win 22, options [nop,nop,TS val 2844191440 ecr 3032332917], length 156: pptp CTRL_MSGTYPE=SCCRP PROTO_VER(1.0) RESULT_CODE(1) ERR_CODE(0) FRAME_CAP() BEARER_CAP() MAX_CHAN(1) FIRM_REV(1) HOSTNAME(local) VENDOR(linux)
13:36:19.069283 IP 192.168.100.118.46750 > 185.104.185.124.1723: Flags [.], ack 157, win 1892, options [nop,nop,TS val 3032333112 ecr 2844191440], length 0
13:36:19.874244 IP 192.168.100.118.46750 > 185.104.185.124.1723: Flags [P.], seq 157:325, ack 157, win 1892, options [nop,nop,TS val 3032333917 ecr 2844191440], length 168: pptp CTRL_MSGTYPE=OCRQ CALL_ID(12) CALL_SER_NUM(0) MIN_BPS(2400) MAX_BPS(1000000000) BEARER_TYPE(Any) FRAME_TYPE(E) RECV_WIN(50) PROC_DELAY(0) PHONE_NO_LEN(0) PHONE_NO() SUB_ADDR()
13:36:19.874531 IP 185.104.185.124.1723 > 192.168.100.118.46750: Flags [.], ack 325, win 22, options [nop,nop,TS val 2844192245 ecr 3032333917], length 0
13:36:19.955202 IP 185.104.185.124.1723 > 192.168.100.118.46750: Flags [P.], seq 157:189, ack 325, win 22, options [nop,nop,TS val 2844192326 ecr 3032333917], length 32: pptp CTRL_MSGTYPE=OCRP CALL_ID(63872) PEER_CALL_ID(12) RESULT_CODE(1) ERR_CODE(0) CAUSE_CODE(0) CONN_SPEED(1000000000) RECV_WIN(50) PROC_DELAY(0) PHY_CHAN_ID(0)
13:36:19.955357 IP 192.168.100.118.46750 > 185.104.185.124.1723: Flags [.], ack 189, win 1892, options [nop,nop,TS val 3032333998 ecr 2844192326], length 0