Hi, I want to configure my Raspberry as an Access Point VPN to connect to the internet through my VPN. I connected my Raspberry Pi to the router via a LAN cable, installed OpenVPN and configured my VPN provider (NordVPN) following a tutorial they leave on their website.
https://nordvpn.com/es/tutorials/openwrt/openvpn/
The problem is that this tutorial is for routers with a WAN connection, which in my case does not exist. Therefore, after configuring OpenVPN I don't understand what to configure in Interfaces and Firewall. Can someone help me?
There is nothing WAN specific in that tutorial. Follow the steps as written for a functioning VPN.
I'm sorry for my questions, but I don't know about networks. How can I do steps two and three?
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fda8:f540:0bef::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.proto='dhcp'
network.lan.ipaddr='192.168.1.47'
network.lan.dns='103.86.96.100' '103.86.99.100'
network.lan.peerdns='0'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@zone[1].input='ACCEPT'
firewall.@zone[1].network=' '
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
Pituso
June 29, 2021, 5:55pm
10
I am interested in the topic.
Put the VPN as default gateway for the clients, in the DHCP, or intercept all (or some) traffic in the fw of the router, and reroute it through the tunnel.
Pituso
June 29, 2021, 7:34pm
12
thank you, but the problem is if I bridge the wireless with the vpn, the tun0 interface does not assign ip to the client.
Why would tun0 assign IPs?
mk24
June 29, 2021, 9:14pm
14
Set up a separate network called vpnuser. This network is like a guest network. It must have its own firewall zone. This network has a DHCP server. When users connect to the AP, they will receive a local IP address.
Also create a firewall zone for the VPN tunnel. Enable masquerade on that zone.
Then forward from vpnuser to vpntunnel. Since masquerade is set on the destination zone, multiple users can NAT to the one tunnel IP address you have from the VPN server.
2 Likes
Pituso
July 19, 2021, 12:09pm
15
Thanks
sorry to necro this but, can you explain what you did exactly to make it work?
do i create vpnuser network on interfaces? do i create firewall zone on firewall tab or whithin creating the new interface? wasnt firewall zone created already with nordvpn guide? do i create another one? where to forward vpnuser to vpntunnel?
system
September 29, 2023, 5:22pm
18
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.
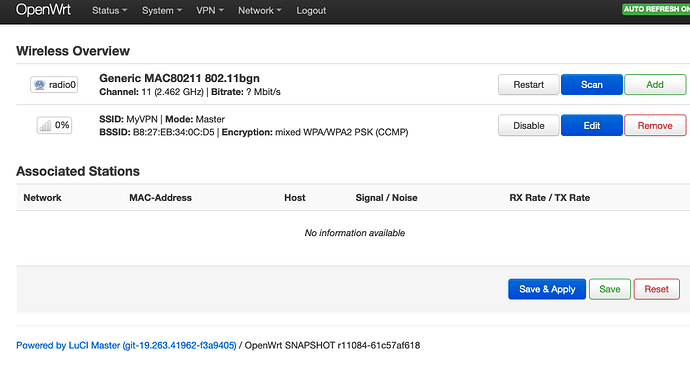
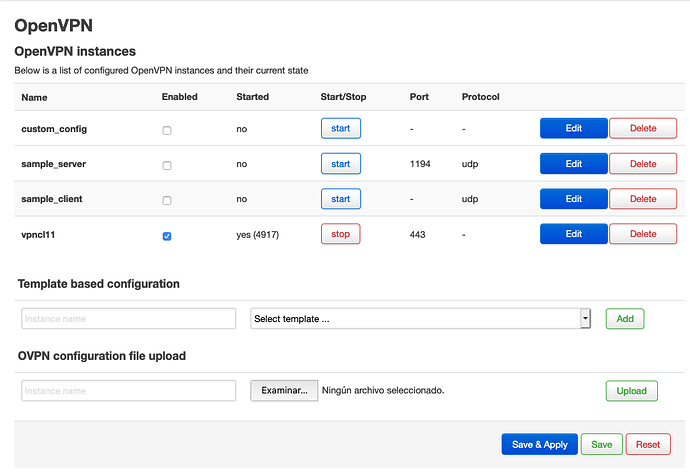
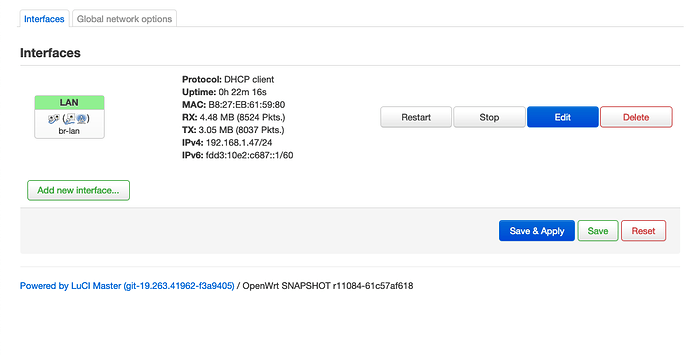
 . I got it .
. I got it .