The terminology is a bit confusing, and it's not helped by the fact that different vendors and/or firmware refers to things a bit differently, despite the fact that 802.1q VLANs are interoperable between pretty much all network hardware (i.e. anything that is standards based, which is almost almost everything). Even some aspects of OpenWrt's own terminology is confusing.
First, we'll talk about network interfaces. These are the L3 (routed) interfaces that have an address and a subnet, and they have no inherent connection against physical hardware (that comes next, of course). They can be connected purely as virtual interfaces, or they can be tied to physical ones.
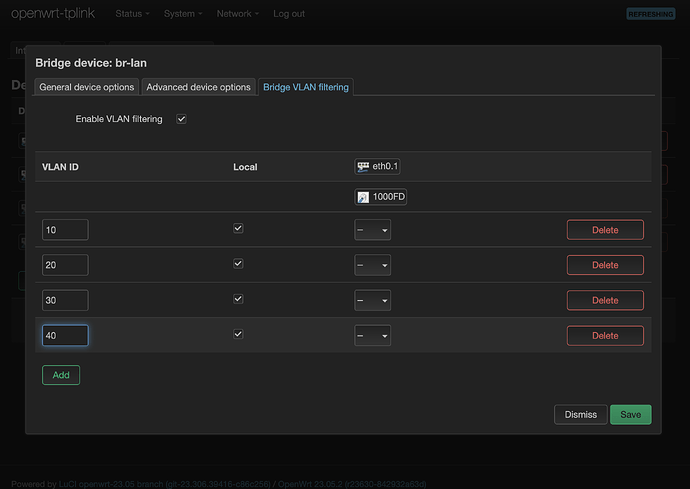
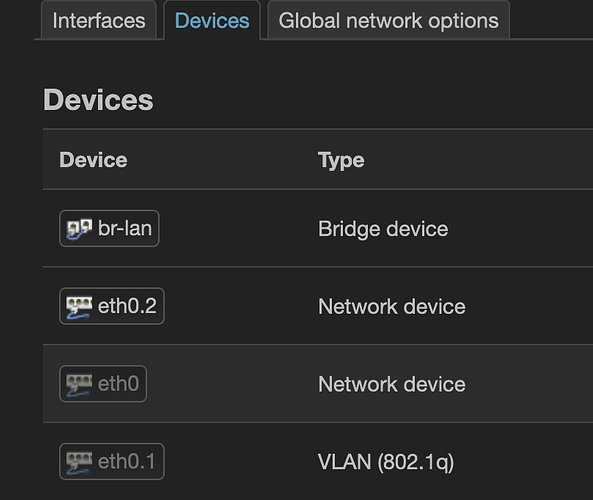
A physical interface is an L1 (phy/link layer) and L2 (switching) construct. This includes the ethernet (switch)/ports and wifi radios. It's fairly obvious what these are, of course. They are treated largely as devices, but there is nuance. In swconfig syntax (such as what you're using), the ethernet ports are actually referenced as a function of the SoC/CPU interface. So eth0 is the internal ethernet connection between the CPU and the switch chip. The base device here is eth0. Then, we can use dotted notation (in conjunction with the right switch config stanzas) to create VLANs that ride on the base device. For example, eth0.4 would represent VLAN 4 (tagged) on base device eth0. The switch can then assign VLAN 4 to the individual ports -- depending on the desired use of the port, it can be assigned as untagged or tagged. In the case of swconfig, you can actually have multiple physical ethernet ports assigned to a VLAN (and that VLAN associated with a network interface), and it counts as a single device.
Then we have bridge devices. A bridge is the software equivalent of an unmanaged switch. Bridges are required anytime you are connecting multiple physical interfaces. That means wifi + ethernet, or 2 or more wifi radios. (In DSA, each physical ethernet port is actually treated as a separate device, but that's another discussion). A bridge is then considered a device (and it may contain multiple devices). If it helps, you can think of each network interface as having just one port -- the bridge has one "port" that connects to the network interface and then additional "ports" for all the physical devices.
Bringing it all together, the switch has multiple VLANs defined, and those can be assigned to each port as needed. They are connected to the CPU by its internal eth0 port and designated as eth0.x where x is the VLAN ID. Those are in turn associated with the L3 network interfaces as devices.
If we want to put multiple VLANs on a single port/cable, it is the tags that make sure the switch (and the downstream device) knows what VLAN a given ethernet frame belongs. This makes it possible to differentiate (and keep separate at this layer) the traffic for each VLAN and assign it to the ports of interest.
Does that help explain the concept?