am very bad at 'title' generation but if you have a good one and if the "title" can be changed, please recommend one.
anyways, this may really sound weird or maybe it is already...
so i have a router running in AP mode & disabled services like: "dnsmasq", "firewall" and "odhcpd"..., it also has a bunch of 'vlans' on it.
i have created multiple SSID's & linked them to whatever 'vlans' i need, & so far, everything is working wonderful, have internet access & without issues!
please refer to the pics below for more info.
as you can see from the pic, i have made vlan404 as PVID (not sure if i sound right here...) as to make the AP 'configurably' accessible via the 'wan' port.
my motive is to prevent and/or disable internet access to this 'non-vlan' group [w/c is vlan404 (ironic..., i know), & please forgive me for being a noob]
i consider vlan404 as my 'management interface' and therefore, should not have internet access since the other 'vlans' i have created has/have proper internet access already defined.
vlan404 also serves DHCP as i sometimes need this functionality, but it should not serve dns or pass a gateway (btw, i have configured dhcp/dnsmasq like below)
note #1: hint in dhcp_option '3' & dhcp_option '6'
note #2: vlan404 DHCP is located on my 'main' OpenWRT x86 router.
config dhcp 'core'
option interface 'core'
option start '100'
option limit '149'
option leasetime '12h'
list dhcp_option '3'
list dhcp_option '6'
and as expected..., it is not showing DNS nor Gateway (issued 'ipconfig /all')
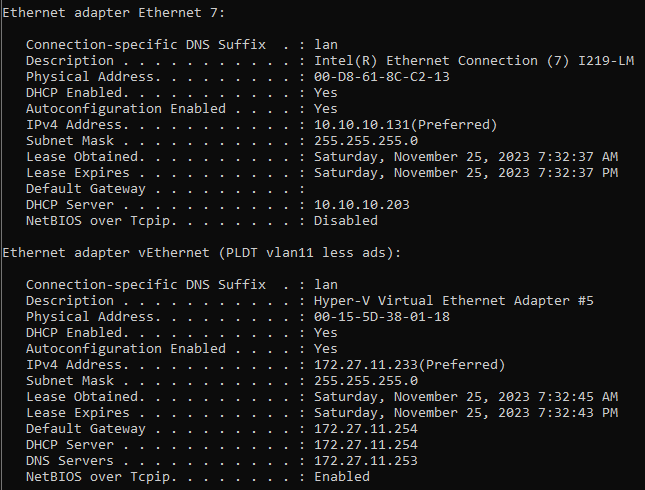
Now the 'fun' part..., i just realized that the AP itself does not have internet access...
how do i provide internet access to the AP? while preventing internet access to anything that connects to vlan404?

