What I intend to achieve.
Some devices in my network have hardcoded dns 8.8.8.8
Any device using any other DNS other than PiHole (at 192.168.1.2) should be redirected to PiHole
Redirection must be in such a way that PiHole sees the original IP of the device, else PiHole logs show the requesting device as the router itself (which is useless for tracking)
To do this, I tried these sets of iptables rules.
# I'm sorry, I forgot where I got this from, I think a reddit thread
iptables -t nat -A POSTROUTING -j MASQUERADE
iptables -t nat -I PREROUTING -i br-lan+ ! -s 192.168.1.2 -p tcp --dport 53 -j DNAT --to 192.168.1.2:53
iptables -t nat -I PREROUTING -i br-lan+ ! -s 192.168.1.2 -p udp --dport 53 -j DNAT --to 192.168.1.2:53
MASQUERADE is the cause of this, which basically is similar to what NAT does. Without MASQUERADE, DNS requests timeout (nslookup ads.google.com. 8.8.8.8)
I then tried this , from the OpenWrt form. Requests made from devices show up in the PiHole dashboard (instead of the router), but the device doesn't get back the response (dns timeout).
iptables -t nat -N dnshijack
# log packet - troubleshooting, remove "#"
# iptables -t nat -I dnshijack -j LOG --log-prefix "dnshijack4"
# send to pihole
iptables -t nat -A dnshijack -j DNAT --to-destination 192.168.1.2
# allow the PiHoles
iptables -t nat -A prerouting_lan_rule -m mac --mac-source b8:27:eb:4c:5a:ad -p udp --dport 53 -j ACCEPT
iptables -t nat -A prerouting_lan_rule -m mac --mac-source b8:27:eb:4c:5a:ad -p tcp --dport 53 -j ACCEPT
# allow queries for local addresses
iptables -t nat -A prerouting_lan_rule -p tcp --dport 53 -d 192.168.1.1 -j ACCEPT
iptables -t nat -A prerouting_lan_rule -p udp --dport 53 -d 192.168.1.1 -j ACCEPT# send the rest to PiHole
iptables -t nat -A prerouting_lan_rule -p udp --dport 53 -j dnshijack
iptables -t nat -A prerouting_lan_rule -p tcp --dport 53 -j dnshijack
What's the correct way to do this? I tried going through iptables and learning it, but looks like it's going to take me a while to fully understand it.
Thanks for the help everyone!
trendy
March 16, 2021, 3:22pm
2
You forgot the postrouting rule.
I'm sorry, I don't know what to add.
trendy
March 16, 2021, 3:48pm
5
Look at this post, it is more complete.
I tried this for my network, and I get "Query refused" (MAC address removed)
iptables -t nat -N dnshijack
# iptables -t nat -I dnshijack -j LOG --log-prefix "dnshijack4 "
iptables -t nat -A dnshijack -j DNAT --to-destination 192.168.1.2
# allow Pihole to query internet
iptables -t nat -A prerouting_lan_rule -m mac --mac-source 00:11:22:33:44:55 -p udp --dport 53 -j ACCEPT
iptables -t nat -A prerouting_lan_rule -m mac --mac-source 00:11:22:33:44:55 -p tcp --dport 53 -j ACCEPT
# allow queries to OpenWrt
iptables -t nat -A prerouting_lan_rule -p tcp --dport 53 -d 192.168.1.1 -j ACCEPT
iptables -t nat -A prerouting_lan_rule -p udp --dport 53 -d 192.168.1.1 -j ACCEPT
# anything else is hijacked
iptables -t nat -A prerouting_lan_rule -p udp --dport 53 -j dnshijack
iptables -t nat -A prerouting_lan_rule -p tcp --dport 53 -j dnshijack
# other zones
iptables -t nat -A prerouting_guest_rule -p tcp --dport 53 -d 192.168.1.2 -j ACCEPT
iptables -t nat -A prerouting_guest_rule -p udp --dport 53 -d 192.168.1.2 -j ACCEPT
iptables -t nat -A prerouting_guest_rule -p udp --dport 53 -j dnshijack
iptables -t nat -A prerouting_guest_rule -p tcp --dport 53 -j dnshijack
iptables -t nat -A prerouting_iot_rule -p tcp --dport 53 -d 192.168.1.2 -j ACCEPT
iptables -t nat -A prerouting_iot_rule -p udp --dport 53 -d 192.168.1.2 -j ACCEPT
iptables -t nat -A prerouting_iot_rule -p udp --dport 53 -j dnshijack
iptables -t nat -A prerouting_iot_rule -p tcp --dport 53 -j dnshijack
# fix "reply from unexpected source"
iptables -t nat -A postrouting_lan_rule -d 192.168.1.2 -p tcp -m tcp --dport 53 -m comment --comment "!fw3: DNS Pi-hole MASQUERADE" -j MASQUERADE
iptables -t nat -A postrouting_lan_rule -d 192.168.1.2 -p udp -m udp --dport 53 -m comment --comment "!fw3: DNS Pi-hole MASQUERADE" -j MASQUERADE
> nslookup ads.google.com 8.8.8.8 # this should work just like the one below
Server: UnKnown
Address: 8.8.8.8
*** UnKnown can't find ads.google.com: Query refused
> nslookup ads.google.com
Server: pihole
Address: 192.168.1.2
Name: ads.google.com
Addresses: ::
0.0.0.0
trendy
March 16, 2021, 4:04pm
7
This is an answer from Pihole, nothing wrong with the hijack script.
I get that for all requests, I can't DNS request anything, till I remove the snippet above from custom firewall rules. Then everything works again
> nslookup google.com
Server: pihole
Address: 192.168.1.2
*** pihole can't find google.com: Query refused
> nslookup google.com 8.8.8.8
Server: UnKnown
Address: 8.8.8.8
*** UnKnown can't find google.com: Query refused
Are you intercepting the pinholes DNS calls too, creating a loop?
(on cell, code snippets are hard to read)
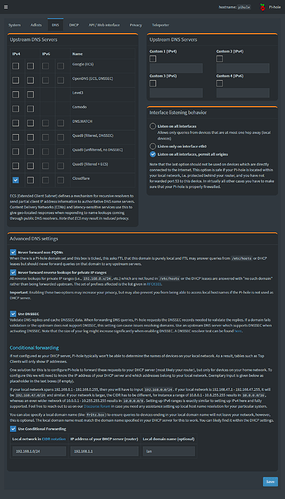
I hope not. I have conditional forwarding enabled on the pihole, and can assure you that it only forwards .lan zone to the router.
Run a traceroute from the pi to 8.8.8.8 or whatever DNS you use.
trendy
March 16, 2021, 4:26pm
12
Check Interface listening behavior to be Listen on all interfaces, permit all origins (in Pihole).iptables-save -c from OpenWrt.
1 Like
With the script removed, I get this
From pihole (the underlying ubuntu system)
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets
1 R7800.lan (192.168.1.1) 0.791 ms 0.486 ms 0.590 ms
2 10.190.0.1 (10.190.0.1) 1.749 ms 1.939 ms 1.808 ms
3 10.120.0.1 (10.120.0.1) 2.154 ms 2.028 ms 2.282 ms
* ISP stuff removed *
9 dns.google (8.8.8.8) 9.588 ms 9.351 ms 9.634 ms
From the docker container in which pihole actually runs with net=host setting
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets
1 R7800.lan (192.168.1.1) 0.839 ms 0.490 ms 0.439 ms
2 10.190.0.1 (10.190.0.1) 1.935 ms 1.994 ms 1.726 ms
3 10.120.0.1 (10.120.0.1) 2.799 ms 2.612 ms 2.988 ms
* ISP stuff removed *
9 dns.google (8.8.8.8) 9.620 ms 9.844 ms 10.164 ms
From a windows device connected via WiFi to OpenWrt router
Tracing route to dns.google [8.8.8.8]
over a maximum of 30 hops:
1 1 ms 1 ms <1 ms R7800.lan [192.168.1.1]
2 34 ms 2 ms 7 ms 10.190.0.1
3 2 ms 3 ms 2 ms 10.120.0.1
* * * * ISP stuff remvoed *
9 10 ms 10 ms 10 ms dns.google [8.8.8.8]
Trace complete.
With the script
From pihole (the underlying ubuntu system)
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets
1 R7800.lan (192.168.1.1) 0.640 ms 0.630 ms 0.581 ms
2 10.190.0.1 (10.190.0.1) 25.986 ms 25.816 ms 25.903 ms
3 10.120.0.1 (10.120.0.1) 2.149 ms 2.221 ms 1.843 ms
* ISP stuff removed *
9 dns.google (8.8.8.8) 9.995 ms 10.368 ms 9.941 ms
From the docker container in which pihole actually runs with net=host setting
traceroute to 8.8.8.8 (8.8.8.8), 30 hops max, 60 byte packets
1 R7800.lan (192.168.1.1) 0.935 ms 0.732 ms 0.652 ms
2 10.190.0.1 (10.190.0.1) 1.792 ms 1.874 ms 1.730 ms
3 10.120.0.1 (10.120.0.1) 2.336 ms 2.203 ms 2.299 ms
* ISP stuff removed *
9 dns.google (8.8.8.8) 20.963 ms 20.723 ms 20.672 ms
From a windows device connected via WiFi to OpenWrt router
Tracing route to dns.google [8.8.8.8]
over a maximum of 30 hops:
1 1 ms <1 ms <1 ms R7800.lan [192.168.1.1]
2 2 ms 1 ms 1 ms 10.190.0.1
3 2 ms 2 ms 2 ms 10.120.0.1
* * * * ISP stuff remvoed *
9 11 ms 10 ms 10 ms dns.google [8.8.8.8]
nslookup from the windows device
> nslookup google.com
Server: pihole
Address: 192.168.1.2
*** pihole can't find google.com: Query refused
Set pihole to listen on all interfaces
Without script
# Generated by iptables-save v1.8.3 on Tue Mar 16 22:18:41 2021
*nat
:PREROUTING ACCEPT [14:1557]
:INPUT ACCEPT [2:107]
:OUTPUT ACCEPT [6:417]
:POSTROUTING ACCEPT [4:277]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[14:1557] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[14:1557] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[16:1753] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[4:277] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[12:1476] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[4:277] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[14:1557] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[12:1476] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[12:1476] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Tue Mar 16 22:18:41 2021
# Generated by iptables-save v1.8.3 on Tue Mar 16 22:18:41 2021
*mangle
:PREROUTING ACCEPT [110:11061]
:INPUT ACCEPT [82:7268]
:FORWARD ACCEPT [26:3679]
:OUTPUT ACCEPT [83:9725]
:POSTROUTING ACCEPT [107:13248]
[4:208] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[6:308] -A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Tue Mar 16 22:18:41 2021
# Generated by iptables-save v1.8.3 on Tue Mar 16 22:18:41 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[0:0] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[83:7308] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[81:7201] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A INPUT -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[1:52] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[2:107] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[0:0] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[26:3679] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[14:2218] -A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD
[14:2218] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1:40] -A FORWARD -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[11:1421] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[0:0] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[84:10309] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[78:9892] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[3:189] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[3:228] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[1:52] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[4:277] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[11:1421] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[11:1421] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[1:88] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2:107] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2:107] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[3:189] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[3:189] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[2:107] -A zone_lan_src_ACCEPT -i br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[13:1561] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[0:0] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[0:0] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[3:228] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[3:228] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[0:0] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Tue Mar 16 22:18:41 2021
Then go went to router page, added the script to firewall page, hit save, then ran the command
With script
Note: MAC address remvoed
# Generated by iptables-save v1.8.3 on Tue Mar 16 22:22:46 2021
*nat
:PREROUTING ACCEPT [16:3131]
:INPUT ACCEPT [3:227]
:OUTPUT ACCEPT [9:717]
:POSTROUTING ACCEPT [1:109]
:dnshijack - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[19:3338] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[17:3088] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[2:250] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[19:2744] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[3:261] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[16:2483] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[2:152] -A dnshijack -j LOG --log-prefix "dnshijack4 "
[2:152] -A dnshijack -j DNAT --to-destination 192.168.1.2
[0:0] -A postrouting_lan_rule -d 192.168.1.2/32 -p tcp -m tcp --dport 53 -m comment --comment "!fw3: DNS Pi-hole MASQUERADE" -j MASQUERADE
[2:152] -A postrouting_lan_rule -d 192.168.1.2/32 -p udp -m udp --dport 53 -m comment --comment "!fw3: DNS Pi-hole MASQUERADE" -j MASQUERADE
[0:0] -A prerouting_lan_rule -p udp -m mac --mac-source 00:11:22:33:44:55 -m udp --dport 53 -j ACCEPT
[0:0] -A prerouting_lan_rule -p tcp -m mac --mac-source 00:11:22:33:44:55 -m tcp --dport 53 -j ACCEPT
[0:0] -A prerouting_lan_rule -d 192.168.1.1/32 -p tcp -m tcp --dport 53 -j ACCEPT
[1:55] -A prerouting_lan_rule -d 192.168.1.1/32 -p udp -m udp --dport 53 -j ACCEPT
[2:152] -A prerouting_lan_rule -p udp -m udp --dport 53 -j dnshijack
[0:0] -A prerouting_lan_rule -p tcp -m tcp --dport 53 -j dnshijack
[3:261] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[17:3088] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[16:2483] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[16:2483] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[2:250] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Tue Mar 16 22:22:46 2021
# Generated by iptables-save v1.8.3 on Tue Mar 16 22:22:46 2021
*mangle
:PREROUTING ACCEPT [90:20269]
:INPUT ACCEPT [56:6239]
:FORWARD ACCEPT [28:13116]
:OUTPUT ACCEPT [64:10353]
:POSTROUTING ACCEPT [91:23365]
[3:156] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[3:148] -A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Tue Mar 16 22:22:46 2021
# Generated by iptables-save v1.8.3 on Tue Mar 16 22:22:46 2021
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[0:0] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[56:6239] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[51:5762] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A INPUT -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[1:52] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[3:227] -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input
[2:250] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[28:13116] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[18:1006] -A FORWARD -m comment --comment "!fw3: Traffic offloading" -m conntrack --ctstate RELATED,ESTABLISHED -j FLOWOFFLOAD
[18:1006] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A FORWARD -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[10:12110] -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward
[0:0] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[0:0] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[64:11057] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[54:8840] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[0:0] -A OUTPUT -m conntrack --ctstate INVALID -m comment --comment "!fw3" -j DROP
[2:1609] -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output
[8:608] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[2:250] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[0:0] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[1:52] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[2:1609] -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT
[10:12110] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[10:12110] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[2:152] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[3:227] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[3:227] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[2:1609] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[2:1609] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[3:227] -A zone_lan_src_ACCEPT -i br-lan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[16:12566] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[2:250] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[0:0] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2:250] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[8:608] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[8:608] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[2:250] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Tue Mar 16 22:22:46 2021
trendy
March 16, 2021, 5:54pm
15
You have misconfigured something:
I can see 2 packets being intercepted by hijack script. However the rule to allow the mac address of the Pihole has 0 hits. Which means that either the mac address you have there is wrong or the pihole is not asking upstream.
1 Like
Hmm I see, how do I test this?
There also seems to be some sort of loop going on, I get hundreds of requests sometimes on the pihole log
Are the settings okay?
trendy
March 16, 2021, 6:09pm
18
Turn off DNSSEC for a test. Or add a few more forwarders.
1 Like
you could try disabling DNSSEC, for the time being, to have one less source of error
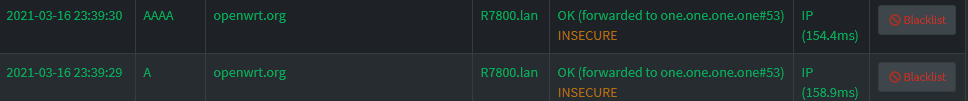
You're right! I had the WiFi mac instead of the eth0 mac. Stupid me. Thank you for pointing it out. I'm really sorry, I should've looked closer. I fixed it. It works now, but the requests still seem to come from the router instead of the device.
> nslookup openwrt.org 8.8.8.8
Server: dns.google
Address: 8.8.8.8
Non-authoritative answer:
Name: openwrt.org
Addresses: 2a03:b0c0:3:d0::1af1:1
139.59.209.225