Hardware: TPLink Archer A7
Firmware: OpenWrt SNAPSHOT r8859-f36bc3f
I'm attempting to install by following the steps on the basic guide
The "Generating Certs" step appears to complete without issues. However, the "Server Config" step does not. Below is what I hope is all the relevant info:
Generating Certs step:
root@OpenWrt:~# wget --no-check-certificate -O /tmp/create-certs.sh "https://openwrt.org/_export/code/docs/guide-user/services/vpn/openvpn/bas
ic?codeblock=2"
Downloading 'https://openwrt.org/_export/code/docs/guide-user/services/vpn/openvpn/basic?codeblock=2'
Connecting to 2a03:b0c0:3:d0::1af1:1:443
Writing to '/tmp/create-certs.sh'
Download completed (2353 bytes)
root@OpenWrt:~# sh -v -x /tmp/create-certs.sh
#!/bin/sh
# Installing packages
opkg update
+ opkg update
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/packages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_core
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/packages/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/kmods/4.14.89-1-b23d765494fdf25faa5958d347a0564e/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_kmods
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/kmods/4.14.89-1-b23d765494fdf25faa5958d347a0564e/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/base/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_base
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/base/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/luci/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_luci
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/luci/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/packages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_packages
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/packages/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/routing/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_routing
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/routing/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/telephony/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_telephony
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/telephony/Packages.sig
Signature check passed.
opkg install openssl-util openvpn-openssl
+ opkg install openssl-util openvpn-openssl
Package openssl-util (1.0.2p-1) installed in root is up to date.
Package openvpn-openssl (2.4.6-3) installed in root is up to date.
# Creating Directory Structure
VPN_DIR="/etc/openvpn"
+ VPN_DIR=/etc/openvpn
PKI_DIR="$VPN_DIR/ssl"
+ PKI_DIR=/etc/openvpn/ssl
if [ -d "$PKI_DIR" ]
then
rm -rf "$PKI_DIR"
fi
+ '[' -d /etc/openvpn/ssl ]
mkdir -p "$PKI_DIR"
+ mkdir -p /etc/openvpn/ssl
chmod -R 600 "$PKI_DIR"
+ chmod -R 600 /etc/openvpn/ssl
cd "$PKI_DIR"
+ cd /etc/openvpn/ssl
touch index.txt index
+ touch index.txt index
echo 1000 > serial
+ echo 1000
cp -f /etc/ssl/openssl.cnf "$PKI_DIR"
+ cp -f /etc/ssl/openssl.cnf /etc/openvpn/ssl
# Customizing openssl.cnf
PKI_CONF="$PKI_DIR/openssl.cnf"
+ PKI_CONF=/etc/openvpn/ssl/openssl.cnf
sed -i "
s:\\\\:/:g
/^dir/ s:=.*:= $PKI_DIR:
/^new_certs_dir/ s:=.*:= $PKI_DIR:
/.*Name/ s:= match:= optional:
/organizationName_default/ s:= .*:= WWW Ltd.:
/stateOrProvinceName_default/ s:= .*:= London:
/countryName_default/ s:= .*:= GB:
/default_days/ s:=.*:= 3650:
/default_bits/ s:=.*:= 4096:
" "$PKI_CONF"
+ sed -i '
s:\\:/:g
/^dir/ s:=.*:= /etc/openvpn/ssl:
/^new_certs_dir/ s:=.*:= /etc/openvpn/ssl:
/.*Name/ s:= match:= optional:
/organizationName_default/ s:= .*:= WWW Ltd.:
/stateOrProvinceName_default/ s:= .*:= London:
/countryName_default/ s:= .*:= GB:
/default_days/ s:=.*:= 3650:
/default_bits/ s:=.*:= 4096:
' /etc/openvpn/ssl/openssl.cnf
cat << "EOF" >> "$PKI_CONF"
[ vpnserver ]
keyUsage = digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
[ vpnclient ]
keyUsage = digitalSignature
extendedKeyUsage = clientAuth
EOF
+ cat
# Generating Server PSK and CA, Server, & Client Certs
# Generating Certifcate Authority Cert & Key
openssl req -batch -nodes -new -keyout "ca.key" -out "ca.crt" -x509 -config "$PKI_CONF" -days "3650"
+ openssl req -batch -nodes -new -keyout ca.key -out ca.crt -x509 -config /etc/openvpn/ssl/openssl.cnf -days 3650
Generating a 4096 bit RSA private key
..........................................................................................................................................................++++
............................................................................................................++++
writing new private key to 'ca.key'
-----
# Generating Server Cert & Key
openssl req -batch -nodes -new -keyout "vpnserver.key" -out "vpnserver.csr" -subj "/CN=vpnserver" -config "$PKI_CONF"
+ openssl req -batch -nodes -new -keyout vpnserver.key -out vpnserver.csr -subj '/CN=vpnserver' -config /etc/openvpn/ssl/openssl.cnf
Generating a 4096 bit RSA private key
................................................................++++
...................................................................................................................................................................................................................................++++
writing new private key to 'vpnserver.key'
-----
# Signing Server Cert
openssl ca -batch -keyfile "ca.key" -cert "ca.crt" -in "vpnserver.csr" -out "vpnserver.crt" -config "$PKI_CONF" -extensions "vpnserver"
+ openssl ca -batch -keyfile ca.key -cert ca.crt -in vpnserver.csr -out vpnserver.crt -config /etc/openvpn/ssl/openssl.cnf -extensions vpnserver
Using configuration from /etc/openvpn/ssl/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4096 (0x1000)
Validity
Not Before: Dec 24 13:30:46 2018 GMT
Not After : Dec 21 13:30:46 2028 GMT
Subject:
commonName = vpnserver
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
Certificate is to be certified until Dec 21 13:30:46 2028 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
# Generating Client Cert & Key
# PASSPHRASE MUST BE SET (4 chars minimum, 16+ chars recommended)
openssl req -batch -new -keyout "vpnclient.key" -out "vpnclient.csr" -subj "/CN=vpnclient" -config "$PKI_CONF"
+ openssl req -batch -new -keyout vpnclient.key -out vpnclient.csr -subj '/CN=vpnclient' -config /etc/openvpn/ssl/openssl.cnf
Generating a 4096 bit RSA private key
................++++
.......................................................................................................................................................................++++
writing new private key to 'vpnclient.key'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
# Signing Client Cert
openssl ca -batch -keyfile "ca.key" -cert "ca.crt" -in "vpnclient.csr" -out "vpnclient.crt" -config "$PKI_CONF" -extensions "vpnclient"
+ openssl ca -batch -keyfile ca.key -cert ca.crt -in vpnclient.csr -out vpnclient.crt -config /etc/openvpn/ssl/openssl.cnf -extensions vpnclient
Using configuration from /etc/openvpn/ssl/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 4097 (0x1001)
Validity
Not Before: Dec 24 13:38:27 2018 GMT
Not After : Dec 21 13:38:27 2028 GMT
Subject:
commonName = vpnclient
X509v3 extensions:
X509v3 Key Usage:
Digital Signature
X509v3 Extended Key Usage:
TLS Web Client Authentication
Certificate is to be certified until Dec 21 13:38:27 2028 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
# Generating OpenVPN TLS PSK
openvpn --genkey --secret "tc.pem"
+ openvpn --genkey --secret tc.pem
# Generating Diffie-Hellman Cert
# May take a while to complete (~25m on WRT3200ACM)
openssl dhparam -out "dh.pem" 2048
+ openssl dhparam -out dh.pem 2048
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
.........................+.....................................................................................................................................................................+...........................................+.....................+...........................................................................................................................+.....+..........................................................................................................................................................+.......................................+......................................................+...................................+............................................................................................................+........................................................................................................................................................................................................................................................+........................................................................................+............................................................................................................................................................................................................................................................+......+........................................................................................................................................................................................................................................+...............................................................................................................................+...................................................+.................................................................................................................+.......................+........................................................................................+........................................................................................................................................................+........................................................................................+.....................+..+.....................................................................................................................+.............................................................................++*++*++*++*
# Correcting Permissions
chmod 600 tc.pem dh.pem ca.key vpnserver.key vpnclient.key
+ chmod 600 tc.pem dh.pem ca.key vpnserver.key vpnclient.key
# Copying Certs & Keys to $VPN_DIR
cp tc.pem dh.pem ca.crt vpnserver.* vpnclient.* "$VPN_DIR"
+ cp tc.pem dh.pem ca.crt vpnserver.crt vpnserver.csr vpnserver.key vpnclient.crt vpnclient.csr vpnclient.key /etc/openvpn
# Returning to initial working directory
cd -
+ cd -
/root
# Done
root@OpenWrt:~#
Server Config step:
root@OpenWrt:~# wget --no-check-certificate -O /tmp/create-configs.sh "https://openwrt.org/_export/code/docs/guide-user/services/vpn/openvpn/b
asic?codeblock=4"
Downloading 'https://openwrt.org/_export/code/docs/guide-user/services/vpn/openvpn/basic?codeblock=4'
Connecting to 2a03:b0c0:3:d0::1af1:1:443
Writing to '/tmp/create-configs.sh'
Download completed (2524 bytes)
root@OpenWrt:~# sh -v -x /tmp/create-configs.sh
#!/bin/sh
# Installing packages
opkg update
+ opkg update
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/packages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_core
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/packages/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/kmods/4.14.89-1-b23d765494fdf25faa5958d347a0564e/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_kmods
Downloading http://downloads.openwrt.org/snapshots/targets/ath79/generic/kmods/4.14.89-1-b23d765494fdf25faa5958d347a0564e/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/base/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_base
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/base/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/luci/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_luci
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/luci/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/packages/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_packages
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/packages/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/routing/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_routing
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/routing/Packages.sig
Signature check passed.
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/telephony/Packages.gz
Updated list of available packages in /var/opkg-lists/openwrt_telephony
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/telephony/Packages.sig
Signature check passed.
opkg install openvpn-openssl luci-app-openvpn
+ opkg install openvpn-openssl luci-app-openvpn
Package openvpn-openssl (2.4.6-3) installed in root is up to date.
Installing luci-app-openvpn (git-18.356.64384-31d259a-1) to root...
Downloading http://downloads.openwrt.org/snapshots/packages/mips_24kc/luci/luci-app-openvpn_git-18.356.64384-31d259a-1_all.ipk
Configuring luci-app-openvpn.
# Configuring network
uci set network.vpnserver="interface"
+ uci set 'network.vpnserver=interface'
uci set network.vpnserver.ifname="tun0"
+ uci set 'network.vpnserver.ifname=tun0'
uci set network.vpnserver.proto="none"
+ uci set 'network.vpnserver.proto=none'
uci commit network
+ uci commit network
# Configuring firewall
uci add firewall rule
+ uci add firewall rule
cfg2592bd
uci set firewall.@rule[-1].name="Allow-OpenVPN"
+ uci set 'firewall.@rule[-1].name=Allow-OpenVPN'
uci set firewall.@rule[-1].src="wan"
+ uci set 'firewall.@rule[-1].src=wan'
uci set firewall.@rule[-1].dest_port="1194"
+ uci set 'firewall.@rule[-1].dest_port=1194'
uci set firewall.@rule[-1].proto="tcp udp"
+ uci set 'firewall.@rule[-1].proto=tcp udp'
uci set firewall.@rule[-1].target="ACCEPT"
+ uci set 'firewall.@rule[-1].target=ACCEPT'
uci add firewall zone
+ uci add firewall zone
cfg26dc81
uci set firewall.@zone[-1].name="vpnserver"
+ uci set 'firewall.@zone[-1].name=vpnserver'
uci add_list firewall.@zone[-1].network="vpnserver"
+ uci add_list 'firewall.@zone[-1].network=vpnserver'
uci set firewall.@zone[-1].input="ACCEPT"
+ uci set 'firewall.@zone[-1].input=ACCEPT'
uci set firewall.@zone[-1].output="ACCEPT"
+ uci set 'firewall.@zone[-1].output=ACCEPT'
uci set firewall.@zone[-1].forward="REJECT"
+ uci set 'firewall.@zone[-1].forward=REJECT'
uci add firewall forwarding
+ uci add firewall forwarding
cfg27ad58
uci set firewall.@forwarding[-1].src="vpnserver"
+ uci set 'firewall.@forwarding[-1].src=vpnserver'
uci set firewall.@forwarding[-1].dest="wan"
+ uci set 'firewall.@forwarding[-1].dest=wan'
uci add firewall forwarding
+ uci add firewall forwarding
cfg28ad58
uci set firewall.@forwarding[-1].src="vpnserver"
+ uci set 'firewall.@forwarding[-1].src=vpnserver'
uci set firewall.@forwarding[-1].dest="lan"
+ uci set 'firewall.@forwarding[-1].dest=lan'
uci commit firewall
+ uci commit firewall
# Configuring OpenVPN Server
VPN_DIR="/etc/openvpn"
+ VPN_DIR=/etc/openvpn
uci set openvpn.vpnserver="openvpn"
+ uci set 'openvpn.vpnserver=openvpn'
uci: Entry not found
uci set openvpn.vpnserver.enabled="1"
+ uci set 'openvpn.vpnserver.enabled=1'
uci: Entry not found
uci set openvpn.vpnserver.verb="3"
+ uci set 'openvpn.vpnserver.verb=3'
uci: Entry not found
uci set openvpn.vpnserver.dev="tun0"
+ uci set 'openvpn.vpnserver.dev=tun0'
uci: Entry not found
uci set openvpn.vpnserver.topology="subnet"
+ uci set 'openvpn.vpnserver.topology=subnet'
uci: Entry not found
uci set openvpn.vpnserver.port="1194"
+ uci set 'openvpn.vpnserver.port=1194'
uci: Entry not found
uci set openvpn.vpnserver.proto="udp"
+ uci set 'openvpn.vpnserver.proto=udp'
uci: Entry not found
uci set openvpn.vpnserver.server="192.168.200.0 255.255.255.0"
+ uci set 'openvpn.vpnserver.server=192.168.200.0 255.255.255.0'
uci: Entry not found
uci set openvpn.vpnserver.client_to_client="1"
+ uci set 'openvpn.vpnserver.client_to_client=1'
uci: Entry not found
uci set openvpn.vpnserver.compress="lzo"
+ uci set 'openvpn.vpnserver.compress=lzo'
uci: Entry not found
uci set openvpn.vpnserver.keepalive="10 120"
+ uci set 'openvpn.vpnserver.keepalive=10 120'
uci: Entry not found
uci set openvpn.vpnserver.persist_tun="1"
+ uci set 'openvpn.vpnserver.persist_tun=1'
uci: Entry not found
uci set openvpn.vpnserver.persist_key="1"
+ uci set 'openvpn.vpnserver.persist_key=1'
uci: Entry not found
uci set openvpn.vpnserver.dh="$VPN_DIR/dh.pem"
+ uci set 'openvpn.vpnserver.dh=/etc/openvpn/dh.pem'
uci: Entry not found
uci set openvpn.vpnserver.tls_crypt="$VPN_DIR/tc.pem"
+ uci set 'openvpn.vpnserver.tls_crypt=/etc/openvpn/tc.pem'
uci: Entry not found
uci set openvpn.vpnserver.ca="$VPN_DIR/ca.crt"
+ uci set 'openvpn.vpnserver.ca=/etc/openvpn/ca.crt'
uci: Entry not found
uci set openvpn.vpnserver.cert="$VPN_DIR/vpnserver.crt"
+ uci set 'openvpn.vpnserver.cert=/etc/openvpn/vpnserver.crt'
uci: Entry not found
uci set openvpn.vpnserver.key="$VPN_DIR/vpnserver.key"
+ uci set 'openvpn.vpnserver.key=/etc/openvpn/vpnserver.key'
uci: Entry not found
uci add_list openvpn.vpnserver.push="redirect-gateway def1"
+ uci add_list 'openvpn.vpnserver.push=redirect-gateway def1'
uci: Entry not found
uci add_list openvpn.vpnserver.push="route 192.168.1.0 255.255.255.0"
+ uci add_list 'openvpn.vpnserver.push=route 192.168.1.0 255.255.255.0'
uci: Entry not found
uci add_list openvpn.vpnserver.push="dhcp-option DNS 192.168.1.1"
+ uci add_list 'openvpn.vpnserver.push=dhcp-option DNS 192.168.1.1'
uci: Entry not found
uci add_list openvpn.vpnserver.push="compress lzo"
+ uci add_list 'openvpn.vpnserver.push=compress lzo'
uci: Entry not found
uci add_list openvpn.vpnserver.push="persist-tun"
+ uci add_list 'openvpn.vpnserver.push=persist-tun'
uci: Entry not found
uci add_list openvpn.vpnserver.push="persist-key"
+ uci add_list 'openvpn.vpnserver.push=persist-key'
uci: Entry not found
VPN_DOMAIN="$(uci -q get dhcp.@dnsmasq[0].domain)"
+ uci -q get 'dhcp.@dnsmasq[0].domain'
+ VPN_DOMAIN=lan
if [ -n "$VPN_DOMAIN" ]
then
uci add_list openvpn.vpnserver.push="dhcp-option DOMAIN $VPN_DOMAIN"
fi
+ '[' -n lan ]
+ uci add_list 'openvpn.vpnserver.push=dhcp-option DOMAIN lan'
uci: Entry not found
uci commit openvpn
+ uci commit openvpn
uci: Entry not found
# Restarting services
service network restart
+ service network restart
/tmp/create-configs.sh: line 73: service: not found
sleep 5
+ sleep 5
service firewall restart
+ service firewall restart
/tmp/create-configs.sh: line 75: service: not found
sleep 5
+ sleep 5
service openvpn restart
+ service openvpn restart
/tmp/create-configs.sh: line 77: service: not found
# Done
root@OpenWrt:~#
Additional troubleshooting info:
root@OpenWrt:~# uci show firewall
firewall.@redirect[0]=redirect
firewall.@redirect[0].target='DNAT'
firewall.@redirect[0].src='wan'
firewall.@redirect[0].dest='lan'
firewall.@redirect[0].proto='tcp'
firewall.@redirect[0].src_dport='22222'
firewall.@redirect[0].dest_ip='192.168.1.106'
firewall.@redirect[0].dest_port='32400'
firewall.@redirect[0].name='PLEX'
firewall.@redirect[1]=redirect
firewall.@redirect[1].target='DNAT'
firewall.@redirect[1].src='wan'
firewall.@redirect[1].dest='lan'
firewall.@redirect[1].proto='tcp'
firewall.@redirect[1].src_dport='6081'
firewall.@redirect[1].dest_ip='192.168.1.106'
firewall.@redirect[1].dest_port='81'
firewall.@redirect[1].name='BLUE IRIS'
firewall.@redirect[2]=redirect
firewall.@redirect[2].target='DNAT'
firewall.@redirect[2].src='wan'
firewall.@redirect[2].dest='lan'
firewall.@redirect[2].proto='tcp'
firewall.@redirect[2].src_dport='9080'
firewall.@redirect[2].dest_ip='192.168.1.109'
firewall.@redirect[2].dest_port='80'
firewall.@redirect[2].name='PIAWARE'
firewall.@redirect[3]=redirect
firewall.@redirect[3].target='DNAT'
firewall.@redirect[3].src='wan'
firewall.@redirect[3].dest='lan'
firewall.@redirect[3].proto='tcp'
firewall.@redirect[3].src_dport='8888'
firewall.@redirect[3].dest_ip='192.168.1.106'
firewall.@redirect[3].dest_port='8080'
firewall.@redirect[3].name='CALIBRE'
firewall.@redirect[4]=redirect
firewall.@redirect[4].target='DNAT'
firewall.@redirect[4].src='wan'
firewall.@redirect[4].dest='lan'
firewall.@redirect[4].proto='tcp'
firewall.@redirect[4].src_dport='4990-4999'
firewall.@redirect[4].dest_ip='192.168.1.105'
firewall.@redirect[4].dest_port='4990-4999'
firewall.@redirect[4].name='DCC'
firewall.@redirect[5]=redirect
firewall.@redirect[5].target='DNAT'
firewall.@redirect[5].src='wan'
firewall.@redirect[5].dest='lan'
firewall.@redirect[5].proto='tcp'
firewall.@redirect[5].src_dport='113'
firewall.@redirect[5].dest_ip='192.168.1.105'
firewall.@redirect[5].dest_port='113'
firewall.@redirect[5].name='IDENT'
firewall.@defaults[0]=defaults
firewall.@defaults[0].syn_flood='1'
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@rule[9]=rule
firewall.@rule[9].name='Allow-OpenVPN'
firewall.@rule[9].src='wan'
firewall.@rule[9].dest_port='1194'
firewall.@rule[9].proto='tcp udp'
firewall.@rule[9].target='ACCEPT'
firewall.@zone[2]=zone
firewall.@zone[2].name='vpnserver'
firewall.@zone[2].network='vpnserver'
firewall.@zone[2].input='ACCEPT'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].forward='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].src='vpnserver'
firewall.@forwarding[1].dest='wan'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].src='vpnserver'
firewall.@forwarding[2].dest='lan'
firewall.@rule[10]=rule
firewall.@rule[10].name='Allow-OpenVPN'
firewall.@rule[10].src='wan'
firewall.@rule[10].dest_port='1194'
firewall.@rule[10].proto='tcp udp'
firewall.@rule[10].target='ACCEPT'
firewall.@zone[3]=zone
firewall.@zone[3].name='vpnserver'
firewall.@zone[3].network='vpnserver'
firewall.@zone[3].input='ACCEPT'
firewall.@zone[3].output='ACCEPT'
firewall.@zone[3].forward='REJECT'
firewall.@forwarding[3]=forwarding
firewall.@forwarding[3].src='vpnserver'
firewall.@forwarding[3].dest='wan'
firewall.@forwarding[4]=forwarding
firewall.@forwarding[4].src='vpnserver'
firewall.@forwarding[4].dest='lan'
firewall.@rule[11]=rule
firewall.@rule[11].name='Allow-OpenVPN'
firewall.@rule[11].src='wan'
firewall.@rule[11].dest_port='1194'
firewall.@rule[11].proto='tcp udp'
firewall.@rule[11].target='ACCEPT'
firewall.@zone[4]=zone
firewall.@zone[4].name='vpnserver'
firewall.@zone[4].network='vpnserver'
firewall.@zone[4].input='ACCEPT'
firewall.@zone[4].output='ACCEPT'
firewall.@zone[4].forward='REJECT'
firewall.@forwarding[5]=forwarding
firewall.@forwarding[5].src='vpnserver'
firewall.@forwarding[5].dest='wan'
firewall.@forwarding[6]=forwarding
firewall.@forwarding[6].src='vpnserver'
firewall.@forwarding[6].dest='lan'
firewall.@rule[12]=rule
firewall.@rule[12].name='Allow-OpenVPN'
firewall.@rule[12].src='wan'
firewall.@rule[12].dest_port='1194'
firewall.@rule[12].proto='tcp udp'
firewall.@rule[12].target='ACCEPT'
firewall.@zone[5]=zone
firewall.@zone[5].name='vpnserver'
firewall.@zone[5].network='vpnserver'
firewall.@zone[5].input='ACCEPT'
firewall.@zone[5].output='ACCEPT'
firewall.@zone[5].forward='REJECT'
firewall.@forwarding[7]=forwarding
firewall.@forwarding[7].src='vpnserver'
firewall.@forwarding[7].dest='wan'
firewall.@forwarding[8]=forwarding
firewall.@forwarding[8].src='vpnserver'
firewall.@forwarding[8].dest='lan'
firewall.@rule[13]=rule
firewall.@rule[13].name='Allow-OpenVPN'
firewall.@rule[13].src='wan'
firewall.@rule[13].dest_port='1194'
firewall.@rule[13].proto='tcp udp'
firewall.@rule[13].target='ACCEPT'
firewall.@zone[6]=zone
firewall.@zone[6].name='vpnserver'
firewall.@zone[6].network='vpnserver'
firewall.@zone[6].input='ACCEPT'
firewall.@zone[6].output='ACCEPT'
firewall.@zone[6].forward='REJECT'
firewall.@forwarding[9]=forwarding
firewall.@forwarding[9].src='vpnserver'
firewall.@forwarding[9].dest='wan'
firewall.@forwarding[10]=forwarding
firewall.@forwarding[10].src='vpnserver'
firewall.@forwarding[10].dest='lan'
root@OpenWrt:~#
root@OpenWrt:~# uci show network
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd06:7051:7eab::/48'
network.lan=interface
network.lan.type='bridge'
network.lan.ifname='eth0.1'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.wan=interface
network.wan.ifname='eth0.2'
network.wan.proto='dhcp'
network.wan.peerdns='0'
network.wan.dns='127.0.0.1'
network.wan6=interface
network.wan6.ifname='eth0.2'
network.wan6.proto='dhcpv6'
network.wan6.reqaddress='try'
network.wan6.reqprefix='auto'
network.wan6.peerdns='0'
network.wan6.dns='0::1'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].ports='2 3 4 5 0t'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].ports='1 0t'
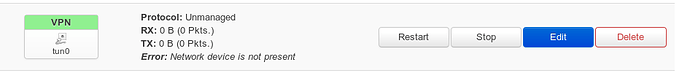
network.vpnserver=interface
network.vpnserver.ifname='tun0'
network.vpnserver.proto='none'
root@OpenWrt:~#
root@OpenWrt:~# uci show openvpn
uci: Entry not found
logread -l 250 -e openvpn https://pastebin.com/3uke4wEp

 Create an account and make the changes you think would have helped the “past you” when you followed it the first time.
Create an account and make the changes you think would have helped the “past you” when you followed it the first time.