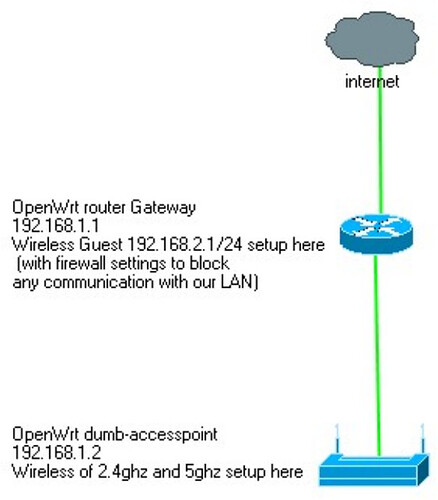
Hi I setup my new network like follow:
Basically the gateway is a Linksys WRT1900ACS because of wireless unstable I decided to do an AP DUMB for my wireless 2.4Ghz and 5Ghz (with TP-Link Archer C7 v5 ip 192.168.1.2) but I still left the Guest network on the 2.4Ghz of the Gateway because of firewall and isolation reason.
The Guest Network can not connect it doesn't get any ip
I Have in the log:
daemon.notice hostapd: wlan1: AP-STA-POSSIBLE-PSK-MISMATCH
But I allow the port 53 and port 67-68 in the firewall....
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
option masq '1'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding 'lan_wan'
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
>config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Guest DNS'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Guest DHCP'
list proto 'udp'
option src 'guest'
option target 'ACCEPT'
option dest_port '67-68'
option dest 'lan'
config rule
option name 'Block Guest To access Private Network'
option src 'guest'
option dest 'lan'
list dest_ip '192.168.1.0/24'
option target 'DROP'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config redirect
option target 'DNAT'
option name 'cam1'
option src 'wan'
option src_dport '7000'
option dest 'lan'
option dest_ip '192.168.1.251'
config redirect
option target 'DNAT'
option name 'cam2'
option src 'wan'
option dest 'lan'
option dest_ip '192.168.1.251'
option src_dport '35000'
config zone
option name 'guest'
option output 'ACCEPT'
option forward 'REJECT'
option input 'REJECT'
list network 'Guest'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
config forwarding
option src 'guest'
option dest 'wan'
/etc/config/network/
config interface 'Guest'
option proto 'static'
list dns '4.2.2.2'
list dns '8.8.8.8'
option device 'wlan1'
list ipaddr '192.168.2.1/24'
Did I miss something ?