Hello, I just tried the luci-app-pppoe-server package to make my device a PPPoE Server. The router is connected. But can't provide Internet. How to handle it?
My device is NanoPi R5S
Screenshot in Router device.
Hello, I just tried the luci-app-pppoe-server package to make my device a PPPoE Server. The router is connected. But can't provide Internet. How to handle it?
My device is NanoPi R5S
Screenshot in Router device.

by looking at the client device, too ?
OpenWRT connection runs smoothly. But on the router side as above.
The topology...
ISP -> OpenWRT -> Router client
Add the pppoe interface (device) to the lan firewall zone.
uci set firewall.@zone[0].device='ppp+'
uci commit firewall
/etc/init.d/firewall restart
Thank You!
This works
Update:
Test ping from pppoe client
Why is the connection lost?, While it was working fine before.
Meanwhile, internet connection on OpenWRT is normal.
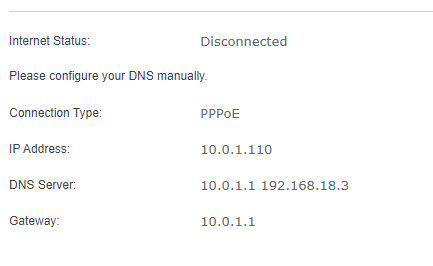
This is a DNS issue.
Try from the client:
nslookup google.com 10.0.1.1
nslookup google.com 192.168.18.1
nslookup google.com 8.8.8.8
This result
nslookup google.com 8.8.8.8
DNS request timed out.
timeout was 2 seconds.
Server: UnKnown
Address: 8.8.8.8
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
DNS request timed out.
timeout was 2 seconds.
*** Request to UnKnown timed-out
What about the DNS server you configured for pppoe clients (10.0.1.1)?
Do you have a DNS hijacking rule configured?
Do you have a firewall rule preventing LAN clients from initiating queries to public DNS servers?
I haven't edited the Firewall configuration at all. Still like the default from OpenWRT.
root@MikWrt:~# uci show firewall
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='REJECT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].flow_offloading='1'
firewall.@defaults[0].flow_offloading_hw='1'
firewall.@defaults[0].fullcone='1'
firewall.@defaults[0].synflood_protect='1'
firewall.@zone[0]=zone
firewall.@zone[0].name='lan'
firewall.@zone[0].network='lan'
firewall.@zone[0].input='ACCEPT'
firewall.@zone[0].output='ACCEPT'
firewall.@zone[0].forward='ACCEPT'
firewall.@zone[0].device='ppp+'
firewall.@zone[1]=zone
firewall.@zone[1].name='wan'
firewall.@zone[1].network='wan' 'wan6'
firewall.@zone[1].input='REJECT'
firewall.@zone[1].output='ACCEPT'
firewall.@zone[1].forward='REJECT'
firewall.@zone[1].masq='1'
firewall.@zone[1].mtu_fix='1'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@rule[9]=rule
firewall.@rule[9].name='Allow-LuCi'
firewall.@rule[9].src='*'
firewall.@rule[9].dest_port='80'
firewall.@rule[9].proto='tcp'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[10]=rule
firewall.@rule[10].name='Allow-SSH'
firewall.@rule[10].src='*'
firewall.@rule[10].dest_port='22'
firewall.@rule[10].target='ACCEPT'
firewall.pppoe_server=include
firewall.pppoe_server.type='script'
firewall.pppoe_server.path='/var/etc/pppoe-server.include'
firewall.pppoe_server.reload='1'
I took 10.0.1.1 just because that's the ip address of the pppoe server
If you are positive about that, then this must be some kind of OpenWrt fork.
The OpenWrt firewall does not accept connections on ports 22 and 80 from everywhere by default. Also, option 'fullcone' in the default section is unknown to me (and all my devices running different versions).
I can only give you general advice.
Verify that dnsmasq is listening on all interfaces (including 10.0.1.1) and check the contents of /var/etc/pppoe-server.include. Given that the include is in the temp directory, it should be some dynamically created rules by the pppoe server package.
Thank you very much! I killed a lot of time to solve this problem.