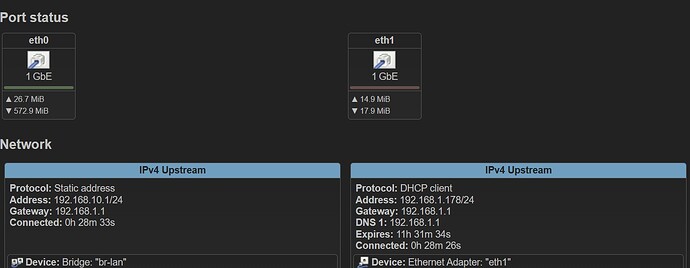
Hi. I am trying to separate my home lab environment from the house network. Attempting to learn.
Ive added a owrt mini pc with two ports, it now looks like this:
Main owrt router (x.x.1.x) ---> smart switch ---> Mini pc router (static x.x.10.x) ---> dumb switch ---> lab hosts
Everything seems to work fine, however in LuCl i see both of the available ports in the Network section of the Overview as IPv4 Upstream, when from what i understand I should be seeing only the eth1 port as upstream:
What am i doing wrong here? Presumably the dumb switch that connects all the lab hosts via eth0 in the br-lan shouldnt be shown there at all?
frollic
September 29, 2024, 6:23am
2
post your /etc/config/network file.
OpenWrt 23.05.5, r24106-10cc5fcd00
-----------------------------------------------------
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdcf:cbbd:4f07::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
option acceptlocal '1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.1'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config interface 'ZeroTier'
option proto 'none'
option device 'ztsdsfxce'
frollic
September 29, 2024, 6:37am
4
you probably don't need this.
post the firewall file too.
1 Like
OpenWrt 23.05.5, r24106-10cc5fcd00
-----------------------------------------------------
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdcf:cbbd:4f07::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
option acceptlocal '1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.1'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config interface 'ZeroTier'
option proto 'none'
option device 'ztfsdxdce'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option enabled '1'
option name 'Allow-ZeroTier-Inbound'
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '9993'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'ZeroTier'
config forwarding
option src 'vpn'
option dest 'lan'
config forwarding
option src 'vpn'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'wan'
option dest 'lan'
config forwarding
option src 'wan'
option dest 'vpn'
config include
option path '/etc/firewall.fail2ban'
option enabled '1'
option reload '1'
I have removed the default gateway and everythings looking normal thank you.
I think i understand whats going on there. I had been playing around with attaching a modem or 4g router in various ways for failover, trying gateway metrics. Thats where i needed it right?
Thanks for the help by the way.
system
October 9, 2024, 6:45am
7
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.