Hello everyone!
I'm having 2 big issues in setup since I started using VLANs:
-
Can't have my FreePBX (VLAN 30) to connect to a SIP Server in Port 5060 UDP (even though this port is forwarded in Openwrt "correctly"). If I remove this server from this VLAN and use a standard approach I get it to connect to this external SIP server. Even my Windows machine (that is not in vlan) can connect using the same credentials, so it's not a banned IP issue.
-
A Playstation 5 in different (VLAN 20) which I denominated as DMZ can't get Open NAT, and even though it's NAT 2, I'm having issues in "Apex Legends" lobbies where I can't sometimes connect to a game server with my party. If I press ready, my group need to wait a couple seconds (like 30+ seconds) until they see my character ready in their screen, otherwise they start the game without me. But I have forwarded either TCP and UDP protocols from this port range 1-65535 for this specific client in this VLAN 20. No luck so far. Would I be able to get an OPEN NAT? I have a valid fixed IP from my ISP, so I suppose I could? I just don't know how. I would love to have OPEN NAT in a separate VLAN, so I don't have to worry about this device, since it would be isolated in its own vlan.
So in my FreePBX server (VLAN 30) I have a random port forwarded to it to allow secure connection between my freepbx server and my remote clients (via TCP TLS). This port is forwarded and it's working great. Even in a mobile connection I can get connect to my FreePBX server and make local calls. So I suppose I have created the VLAN correctly and have done the port forwarding in the right way, but at the same time, why my server is not receiving a response from the SIP server?
tcpdump -i br-lan.30 host app.nvoip.com.br and port 5060
root@roteador:~# tcpdump -i br-lan.30 host app.nvoip.com.br and port 5060
tcpdump: verbose output suppressed, use -v[v]... for full protocol decode
listening on br-lan.30, link-type EN10MB (Ethernet), snapshot length 262144 bytes
19:00:27.856346 IP freepbx.home.myhome.com.5060 > ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060: SIP: REGISTER sip:app.nvoip.com.br:5060 SIP/2.0
19:00:27.870637 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:00:27.887427 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:00:50.742122 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 200 I am alive
19:00:57.904264 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:00:57.921359 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:01:27.939682 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:01:27.956519 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:01:50.741661 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 200 I am alive
19:01:57.973184 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
19:01:57.989403 IP ec2-54-233-253-44.sa-east-1.compute.amazonaws.com.5060 > freepbx.home.myhome.com.5060: SIP: SIP/2.0 401 Unauthorized
While in FreePBX this is what I get:
27098 [2025-01-17 22:00:27] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
27099 [2025-01-17 22:00:50] VERBOSE[141106] res_pjsip/pjsip_configuration.c: Endpoint NVOIP is now Reachable
27100 [2025-01-17 22:00:50] VERBOSE[141106] res_pjsip/pjsip_options.c: Contact NVOIP/sip:12345678@app.nvoip.com.br:5060 is now Reachable. RTT: 15.623 msec
27101 [2025-01-17 22:00:57] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
27102 [2025-01-17 22:01:28] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
27103 [2025-01-17 22:01:58] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
27104 [2025-01-17 22:02:28] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
27105 [2025-01-17 22:02:58] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
27106 [2025-01-17 22:03:28] WARNING[141106] res_pjsip_outbound_registration.c: Temporal response '401' received from 'sip:app.nvoip.com.br:5060' on registration attempt to 'sip:12345678@app.nvoip.com.br:5060', retrying in '30'
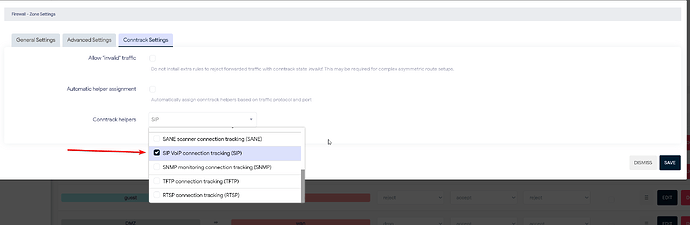
As I said, if I remove this FreePBX server from the VLAN, it can connect to the SIP server even without any port forwardind. I have tried to change the zone settings to ACCEPT, ACCEPT, ACCEPT, but it didn't help either. I've also tried to disable "Automatic helper assignment" for each firewall zone, because I heard of some issues with ALG SIP, but that didn't help either.
Below are my OpenWRT config files (I have replaced some sensitive info and deleted some other non related port forwarding ports to not make it too big):
dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/home.myhome.com/'
option domain 'home.myhome.com'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list rebind_domain 'home.myhome.com'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
list dhcp_option '6,192.168.1.220,192.168.1.1'
list dhcp_option '42,192.168.1.1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'lan2'
option interface 'lan2'
option ignore '1'
config dhcp 'guest'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'guest'
config dhcp 'DMZ'
option interface 'DMZ'
option start '10'
option limit '90'
option leasetime '12h'
config dhcp 'PUBLICO_ISOLADO'
option interface 'PUBLICO_ISOLADO'
option start '10'
option limit '90'
option leasetime '12h'
config host
option name 'freepbx'
list mac '11:22:33:44:55:66'
option ip '192.168.30.10'
option leasetime 'infinite'
option hostid '0030'
config host
option name 'ps5'
list mac 'AA:BB:CC:DD:EE:FF'
option ip '192.168.20.50'
option leasetime 'infinite'
firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option drop_invalid '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vpn'
list network 'rooter'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'AndroidAP'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/firewall.include'
config zone
option forward 'REJECT'
option name 'guest'
option output 'ACCEPT'
option input 'REJECT'
list network 'guest'
config forwarding
option dest 'wan'
option src 'guest'
config rule
option target 'ACCEPT'
option src 'guest'
option name 'Guest DNS'
option dest_port '53'
config rule
option dest_port '67'
option src 'guest'
option name 'Guests DHCP'
option target 'ACCEPT'
list proto 'udp'
config rule 'wg'
option name 'Allow-WireGuard'
option dest_port '9999'
option proto 'udp'
option target 'ACCEPT'
option src '*'
config redirect
option dest 'PUBLICO_ISO'
option target 'DNAT'
option name 'FreePBX TLS'
list proto 'tcp'
option src 'wan'
option src_dport '20000'
option dest_ip '192.168.30.10'
option dest_port '20000'
config zone
option name 'DMZ'
option input 'DROP'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'DMZ'
option log '1'
config forwarding
option src 'lan'
option dest 'DMZ'
config zone
option name 'PUBLICO_ISO'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'PUBLICO_ISOLADO'
config forwarding
option src 'lan'
option dest 'PUBLICO_ISO'
config rule
option name 'Allow-DNS-DHCP-DMZ-NTP'
list proto 'udp'
option src 'DMZ'
option dest_port '53 67 123'
option target 'ACCEPT'
config forwarding
option src 'DMZ'
option dest 'wan'
config forwarding
option src 'PUBLICO_ISO'
option dest 'wan'
config rule
option name 'Allow-DNS-DHCP-NTP-PUBLICO-ISOLADO'
option src 'PUBLICO_ISO'
option dest_port '53 67 123'
option target 'ACCEPT'
list proto 'udp'
config redirect
option name 'FreePBX SIP'
option src 'wan'
option src_dport '5060'
option dest 'PUBLICO_ISO'
option dest_ip '192.168.30.10'
option dest_port '5060'
option target 'DNAT'
list proto 'udp'
config redirect
option name 'FreePBX RTP'
option src 'wan'
option src_dport '10000-20000'
option dest 'PUBLICO_ISO'
option dest_ip '192.168.30.10'
option dest_port '10000-20000'
option target 'DNAT'
list proto 'udp'
config redirect
option dest 'DMZ'
option target 'DNAT'
option name 'Playstation 5'
option src 'wan'
option dest_ip '192.168.20.50'
list proto 'tcp'
list proto 'udp'
option src_dport '1-65535'
option dest_port '1-65535'
network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'XXXXXXXXXXXXXXXXXX::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan.99'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
config device
option name 'wan'
option macaddr 'XXXXXXXXXXXXXXXXXXX'
config interface 'wan'
XXXXXXXXXXXXXXXXXXXXX
config interface 'guest'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.100.1'
config interface 'vpn'
XXXXXXXXXXXXXXXXXXXXX
config interface 'rooter'
XXXXXXXXXXXXXXXXXXXXX
config interface 'AndroidAP'
option proto 'dhcp'
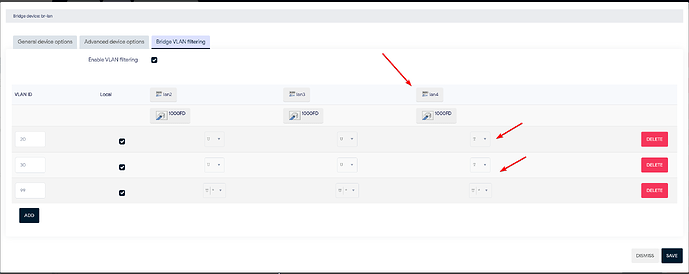
config bridge-vlan
option device 'br-lan'
option vlan '20'
list ports 'lan4:t'
config bridge-vlan
option device 'br-lan'
option vlan '30'
list ports 'lan4:t'
config bridge-vlan
option device 'br-lan'
option vlan '99'
list ports 'lan2:u*'
list ports 'lan3:u*'
list ports 'lan4:u*'
config interface 'DMZ'
option proto 'static'
option device 'br-lan.20'
option ipaddr '192.168.20.4'
option netmask '255.255.255.0'
config interface 'PUBLICO_ISOLADO'
option proto 'static'
option device 'br-lan.30'
option ipaddr '192.168.30.4'
option netmask '255.255.255.0'
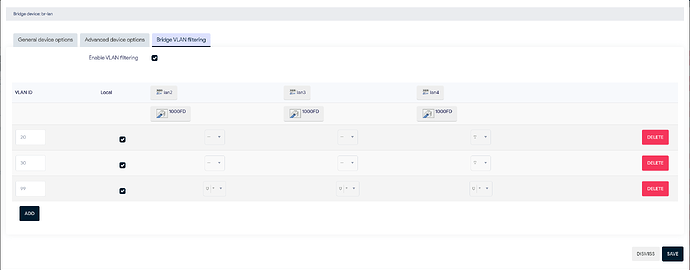
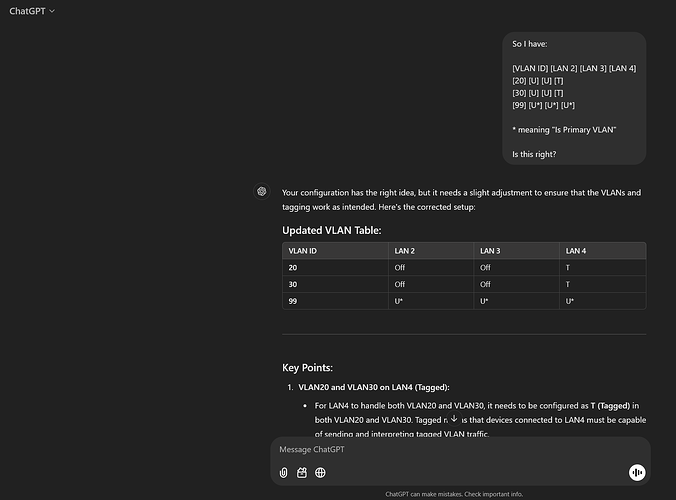
edit: *fixed network tagging