I am trying to setup my three VPS services, but I cannot get the firewall settings correctly.
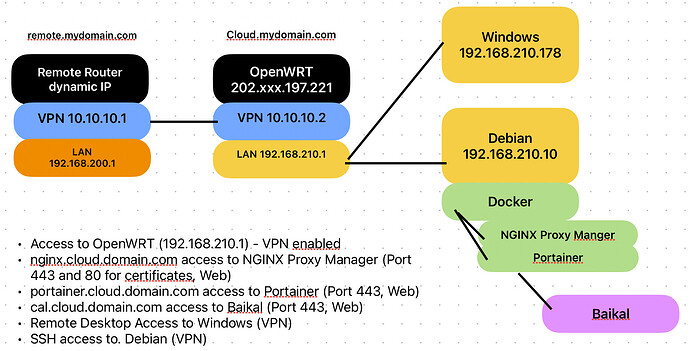
Setup
192.168.210.10, Debian running NGINX Proxy Manager
192.168.210.178, Windows Client
What I can: http://192.168.210.10 an get the Welcome Screen of NGINX.
What I cannot:
I cannot forward any HTTP/80 traffic to the address 192.168.210.10
Later on, I want to route my domain to the internal LAN computer (192.168.210.10).
What I have done in LUCI:
I entered a Forward to 192.168.210.10 (from WAN to LAN, 192.168.210.10, port 80)
I have setup a traffic route allowing the access from WAN to LAN on Port 80.
The Allow-HTTP to grant access to the LUCI GUI is deactivated.
Any hint, what to look at, would be great.
Another issue:
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
1 Like
ubus call system board
{
"kernel": "5.15.137",
"hostname": "Router",
"system": "QEMU Virtual CPU version 2.5+",
"model": "netcup KVM Server",
"board_name": "netcup-kvm-server",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "x86/64",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
}
}
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '****:1a40:0f4d::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.210.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'static'
option device 'eth0'
option ipaddr '202.xxx.197.221'
option netmask '255.255.0.0'
option gateway '202.xxx.196.1'
list dns '94.xxx.14.15'
config interface 'Remote'
option proto 'wireguard'
option private_key 'GEks2**********************'
option listen_port '45312'
list dns '192.168.210.1'
list addresses '10.10.10.2/32'
list addresses '192.168.200.0/24'
list addresses '192.168.210.0/24'
config wireguard_remote
option description 'Remote-Keenteic'
option public_key 'I7Pm*************'
option endpoint_host 'remote.mydomain.se'
option endpoint_port '45312'
option persistent_keepalive '25'
list allowed_ips '10.10.10.1/32'
list allowed_ips '192.168.200.0/24'
option route_allowed_ips '1'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Allow-HTTP'
option src 'wan'
option dest_port '80'
option target 'ACCEPT'
option enabled '0'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'Remote'
option masq '1'
config redirect
option dest 'vpn'
option target 'DNAT'
option name 'VPN Weiterleitung'
list proto 'udp'
option src 'wan'
option dest_ip '10.10.10.0/24'
option dest_port '45312'
option src_dport '45312'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
config rule
option name 'Allow-HTTPS'
option src 'wan'
option dest_port '443'
option target 'ACCEPT'
config rule
option name 'Allow-LAN-Portainer'
option dest 'lan'
list dest_ip '192.168.210.10'
option dest_port '9443'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'NGinx Port 443'
option src 'wan'
option src_dport '433'
option dest_ip '192.168.210.10'
option dest_port '433'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'NGinx Port 80'
option src 'wan'
option dest_ip '192.168.210.10'
list proto 'tcp'
list proto 'udp'
option src_dport '80'
option dest_port '80'
config rule
option name 'Allow-WAN-HTTPs'
option src_port '443'
list dest_ip '192.168.210.10'
option dest_port '443'
option target 'ACCEPT'
option src 'wan'
option dest 'lan'
config rule
option name 'Allow-WAN-HTTP'
option src_port '80'
option dest 'lan'
list dest_ip '192.168.210.10'
option dest_port '80'
option target 'ACCEPT'
option src 'wan'
krazeh
August 28, 2024, 3:34pm
4
Well there's a fair bit of misconfiguration to unpick here...
These entries are wrong. This should just be the address/subnet for the tunnel itself. 192.168.210.0/24 shouldn't be there as it's the local subnet. I'm going to guess 192.168.200.0/24 is subnet at the remote end? If so, it shouldn't be in this list. And if 10.10.10.2/32 is the address for the WG interface it'd be better to change it to a /24.
Masquerading shouldn't be necessary for this zone.
I assume this is to open the wireguard port? If so, then it should be a rule and not a redirect:
config rule
option target 'ACCEPT'
option src 'wan'
option dest_port '45312'
option name 'VPN Weiterleitung'
option proto 'udp'
This is an all round bad idea. Don't do it.
Is Nginx listening on port 433 on the device you're redirecting traffic to? Or the traffic you want to allow being sent to that port?
These won't work as you need to use a redirect (as you're forwarding the packets to a different address), not a traffic rule (which would be used if the packets were already addressed to the correct final destination).
Not sure what the purpose of this is, but it's not going to do much.
I have tried. To apply the changes:
Wireguard subnet setting
Removed useless traffic rules
HTTPS/443 to the device is still open for configuring.
On the client 192.168.210.10 I want to have three open ports:
80 and 443 von NGINX to route all subdomains to this device.
81 as this is the NGINX Proxy Manager configuration port.
Unfortunately entering the Public IP address (http://202.xxx.197.221:81 ) is leading to no result.
krazeh
August 28, 2024, 8:51pm
6
Again, really bad idea. If you want remote access to the router then use the VPN.
If you want further assistance you'll need to provide updated config files when you make changes.
Have you checked the .210 device responds correctly when connecting from a device in the same subnet?
These are the updates for network and firewall after the change:
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '****:1a40:0f4d::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.210.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'static'
option device 'eth0'
option ipaddr '202.xxx.197.221'
option netmask '255.255.0.0'
option gateway '202.xxx.196.1'
list dns '94.xxx.14.15'
config interface 'Remote'
option proto 'wireguard'
option private_key 'GEks2aupT****************'
option listen_port '45312'
list dns '192.168.210.1'
list addresses '192.168.200.0/24'
list addresses '10.10.10.0/24'
config wireguard_remote
option description 'Neckarsulm-Keenteic'
option public_key 'I7PmF+********'
option endpoint_host 'remote.mydomain.com'
option endpoint_port '45312'
option persistent_keepalive '25'
option route_allowed_ips '1'
list allowed_ips '192.168.200.0/24'
list allowed_ips '10.10.10.0/24'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'Neckarsulm'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'NGinx Port 443'
option src 'wan'
option src_dport '433'
option dest_ip '192.168.210.10'
option dest_port '433'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'NGinx Port 80'
option src 'wan'
option dest_ip '192.168.210.10'
list proto 'tcp'
list proto 'udp'
option src_dport '80'
option dest_port '80'
config rule
option name 'Allow-WireGuard-Neckarsulm'
list proto 'udp'
option src 'wan'
option src_port '45312'
option dest_port '45312'
option target 'ACCEPT'
What‘s currently working:
Windows and Debian have Internet through OpenWRT
Windows receives a DHCP lease from OpenWRT
Debians 192.168.210.10 is static defined
I can SSH from Debian to OpenWRT
I can LuCI from Windows to OpenWRT by IP address
VPN needs to be retested as Remote failed and I am not at home.
To give more idea, what‘s the setup, here is a very basic drawing. The Docker stuff is easy for me, once the routing works.
krazeh
August 29, 2024, 9:20pm
8
Pretty sure list dns doesn't do anything. And 192.168.200.0/24 should not be listed here.
The network here doesn't appear to match anything in the network config file.
The ports still look wrong.
Do you want to be able to access things from the wider internet or just from a remote location over the VPN?
Correct would be:
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'Remote'
I edited Names, IP addresses, MAC addresses before replying manually. My fault.
The basic idea is to access from the internet especially by smartphone to the Docker services, especially contacts/calendars/notes of baikal. AdGuard is another service I have in mind to avoid adverts on my cellular always.
I am struggling with the REDIRECT entry. I have created it by LuCi, but I am pretty unsure, how it has to look.
Is the request on ports 443/80 first on the OpenWRT device and then forwarded?
Is the request on ports 443/80 „marked“ as WAN request?
Do I need zones at all?
NGINX requests both ports, 443 and 80. It will route all port-80-requests to port 443 and if needed force SSL.
krazeh
August 29, 2024, 10:10pm
10
The redirect looks fine other than the port numbers.
Now I get, a typing error. 433 instead of 443. I feel pretty stupid in this minute.
Concerning the VPN, have tested the following yesterday night:
Ping from 192.168.200.10 to OpenWrt works
Ping from 192.168.200.10 to Debian (192.168.210.10) failed.
Same result other way around: Ping on the 192.168.2xx.1 router works, pinging a device in the subnet failed.
Traceroute command ends at 10.10.10.1 or 10.10.10.2
krazeh
August 30, 2024, 9:01am
12
Matthias17:
Concerning the VPN
What are the current WG configs at both ends of the tunnel? Network and firewall.
Also, have you checked whether the devices you're trying to ping have a local firewall that may be blocking traffic?
1 Like
I have updated the configuration, but still
cannot access the Debian NGINX service through ports 443/80 and
the LAN clients through VPN, e.g. from 192.168.200.53 to 192.168.210.10.
The WireGuard connection is up and running.
I was told, that the allowed the IPs should be 10.10.10.0/24. I always thought, that naming precise IPs like 10.10.10.15/32 would be more secure.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'xxxx:1a40:0f4d::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.210.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option proto 'static'
option device 'eth0'
option ipaddr '202.xxx.197.221'
option netmask '255.255.0.0'
option gateway '202.xxx.196.1'
list dns '94.140.14.15'
config interface 'Remote'
option proto 'wireguard'
option private_key 'GEks2*******'
option listen_port '45312'
list addresses '10.10.10.2/32'
config wireguard_Remote
option description 'Remote-Keenetic'
option public_key 'I7Pm******'
option endpoint_host 'remote.mydomain.com'
option endpoint_port '45312'
option persistent_keepalive '25'
option route_allowed_ips '1'
list allowed_ips '192.168.200.0/24'
list allowed_ips '10.10.10.0/24'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Allow-HTTP'
option src 'wan'
option dest_port '80'
option target 'ACCEPT'
option enabled '0'
config zone
option name 'vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'Remote'
config forwarding
option src 'lan'
option dest 'vpn'
config forwarding
option src 'vpn'
option dest 'lan'
config rule
option name 'Allow-HTTPS'
option src 'wan'
option dest_port '443'
option target 'ACCEPT'
option enabled '0'
config redirect
option target 'DNAT'
option name 'NGinx Port 443'
option src 'wan'
option src_dport '443'
option dest_ip '192.168.210.10'
option dest_port '443'
option dest 'lan'
config redirect
option target 'DNAT'
option name 'NGinx Port 80'
option src 'wan'
option dest_ip '192.168.210.10'
list proto 'tcp'
list proto 'udp'
option src_dport '80'
option dest_port '80'
option dest 'lan'
config rule
option name 'Allow-WireGuard-Remote'
list proto 'udp'
option src 'wan'
option src_port '45312'
option dest_port '45312'
option target 'ACCEPT‘
krazeh
August 31, 2024, 9:59am
14
From where? The local LAN, remote LAN over VPN, or the internet?
Still need the configs from the other end of the VPN.
egc
August 31, 2024, 10:11am
15
you can remove option src_port '45312', it is not needed but it can block things (it could work but only if that port is the listen port on the other side)
The access to 192.168.210.10 is that both from connected WG "client" and from the Internet (WAN)?
I have removed the Source-Port-information in the WireGuard-Allowance rule.
So, here we are from the Windows Client 192.168.210.178 running in the LAN section of OpenWRT.
Ping to the Debian Client (192.168.210.10) works.
Ping to the OpenWRT router (192.168.210.1) works.
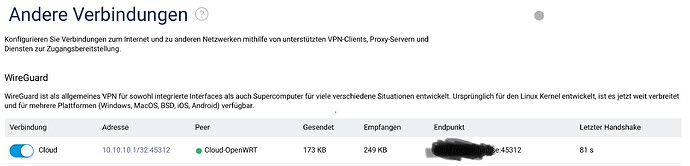
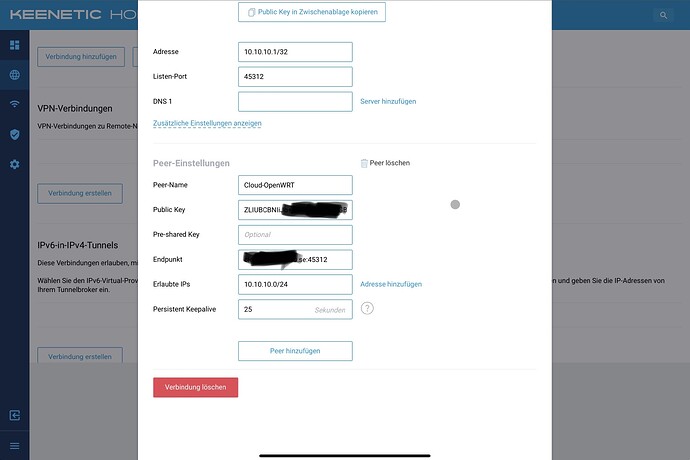
Ping to the Remote Router (192.168.200.1) fails as well as any client on the Remote-site (e.g. 192.168.200.10).
In my opinion the routing for the net 192.168.200.0/24 fails.
Attached are pictures of the remote router, showing, that the WireGuard connection is active and most of the settings.
Concerning the NGINX topic:
The requests on ports 443/80 are not forwarded to the Debian Client running in the LAN section with IP 192.168.210.10. I still cannot spot any reason for it.
Accessing the NGINX address from the intra-LAN-client 192.168.210.10 works by typing into the Browser http://192.168.210.10:80 .
The aim is to access these Docker Services from any point of the Internet, not necessarily through VPN
egc
August 31, 2024, 10:52am
18
On this remote site you also have to allow traffic from 192.168.210.0/24 and not only from 10.10.10.0/24, so put that also in the Allowed IPs, afterwards reboot, that should solve the problem.
Note most clients have their own firewall which will not allow traffic from other subnets so on the 192.168.200.0 side you have to make sure clients allow traffic from 192.168.210.0/24 and the other way around.
I guess, something is broken with the WireGuard VPN connection. When I go to Network > Diagnose in OpenWRT I cannot ping the remote WireGuard address 10.10.10.1, eventhough both routers indicate a connection.
I have a guessing concerning the forwarding:
The redirect is said for forward any 443/80 request to the Debian. But when I call this service in any way, I won‘t do it by IP address, I will call it by a subdomain. So I would have to send any *.cloud.mydomain.com request to the Debian system, correct?