Ok, i have to do this in A side then
Ok, i have to do this in A side then

Yes that will work. After that you'll need to restart the networking in all your LAN endpoint devices so they pick up the new IP.
On both sides?
Now im getting this:
"Invalid Argument"
I need to use a DDNS, is a problem?
EDIT: Dont think so.. i did systemctl stop wg-quick@wg0.service and then systemctl start wg-quick@wg0.service and im not getting DDNS error.
But still appearing "RTNETLINK answers: File exists" error
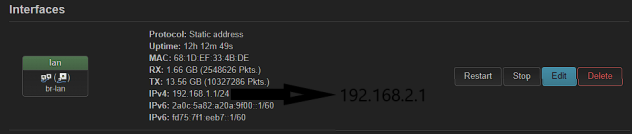
This I assume is happening at B. B is still trying to use 192.168.1.0 as allowed IP. It needs to instead use the new A LAN range 192.168.2.0/24.
Completely forgot that ![]() im in work doing both things sorry.
im in work doing both things sorry.
Now is working.
Now… how can i test the connection and how do i transfer the file?
If the tunnel is working, sharing files would be simply making a Windows to Windows connection. B would initiate a connection to the LAN IP of your machine at A.
I have checked i can execute ping between both points, but, for example, if i want to connect to RDP through this tunnel, how should i do that?
Edit: nevermind, i just got it, It's like I'm physically there.
Just one more question (hope so):
If i want to add a peer (my mobile phone). What should i do to configure this?
I mean, if the peers need to be configured inside the server side, if im not in home, i cant add my mobile phone IP, right? or is there a way to do this?
You'll configure it once... if you have access to your router (even if you are currently remote, but using that WG tunnel), you can create a new peer and then generate a QR code. Read the QR code with your phone and most of the stuff will populate through (you may need to change one or two fields on your phone).
You can set up additional peers on the same link by choosing a unique tunnel IP for each one, such as 192.168.9.3, 192.168.9.4 etc.
The server needs to have each client's public key and tunnel IP in a separate client section for each one. For road warrior clients the additional server configuration is just those two lines for each one. If you're not at home you could use an existing client that has VPN configured to log in and add additional ones.
Use Totalcmd split command or Winrar to split into multiple volumes. Winrar provides the possibility to encrypt the archives. I think 7zip or winzip provides the same too.
I think im not getting this...
[Interface]
PrivateKey = xxxxxxxx4Xs=
Address = 192.168.9.3/24
ListenPort = 51820
DNS = 192.168.2.1
[Peer]
PublicKey = xxxxxxx6ODCM=
# PresharedKey not used
AllowedIPs = 192.168.2.0, 192.168.9.0
Endpoint = xxxxxx.ddns.net:51820
# PersistentKeepAlive not defined
I did something that made me lose internet access, dont know what. I connected the router via HDMI and solved it in /etc/config/network. It was adding my iPhone to peers.
If im not missing anything:
AllowedIPs is the IPs that peer can access, right?
And Address is the address of that peer inside tunnel.
Then, why that config is not working?
Cant i access the tunnel via the internet of my data plan?
What device is that config form?
Kinda, if the source IP on a packet from the remote side matches the AllowedIPs then it's allowed out of the tunnel. If the destination IP on a packet on the local side matches then it's allowed into the tunnel.
Did you add the peer to the router's config... let's see the output of
cat /etc/config/network
(redact keys, of course).
Is the config of the new peer
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd75:07f1:eeb7::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '8.8.8.8'
list dns '8.8.4.4'
config interface 'wan'
option device 'eth1.20'
option proto 'pppoe'
option username 'xxxxxxxxx@digi'
option password 'xxxxxxxxx'
option ipv6 'auto'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config 192.168.1.2 'addr'
config device
option type '8021q'
option ifname 'eth1'
option vid '20'
option name 'eth1.20'
option mtu '1500'
config interface 'wg_vpn'
option proto 'wireguard'
option private_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx='
option listen_port '51820'
option mtu '1280'
list addresses '192.168.9.1/24'
config wireguard_wg_vpn
option description 'ServidorProxmoxPueblo'
option public_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx='
option route_allowed_ips '1'
list allowed_ips '192.168.9.2/32'
list allowed_ips '192.168.1.0/24'
config wireguard_wg_vpn
option description 'Iphone de Paco'
option public_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx='
option private_key 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx='
list allowed_ips '192.168.9.3/24'
option route_allowed_ips '1'
option endpoint_port '51820'
root@OpenWrt:~#
I have configured it with QR
Remove the endpoint port.
And critically, the allowed IPs should be 192.168.9.3/32 <--- /32 is the key.
Then restart your router and try again.
Should i change every IP with */24 to */32?
Why is this?
Only in the WG peer sections (specifically the allowed_ips in the subnet of the main interface's address) of the OpenWrt config. So in short, just the one I pointed out.
If you have multiple peers, you need to make sure that the traffic destined for each peer is routed properly. The /32 ensures that it is a singular address, where as /24 is all addresses from 1-254.
Understood.
I have rebooted the router and when i generate the QR, OpenWRT shows this on the QR information:
[Interface]
PrivateKey = xxxxxxxxxxxxxxxxxxxx=
Address = 192.168.9.3/32
# ListenPort not defined
DNS = 192.168.2.1
[Peer]
PublicKey = xxxxxxxxxxxxxxxxxxxxx=
# PresharedKey not used
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = xxxxxxxxx.ddns.net:51820
# PersistentKeepAlive not defined
Why AllowedIPs has 0.0.0.0/0, ::0 ?
Does that means that all IPs are allowed?
Which one should i set there?
This is the config that gets placed on the peer. Yes, it is all IPs -- and that is good if you want your phone (or other remote peer) to send all traffic through the tunnel.
You can change this if you want -- just edit the config on the phone itself if you only want remote access to the network.