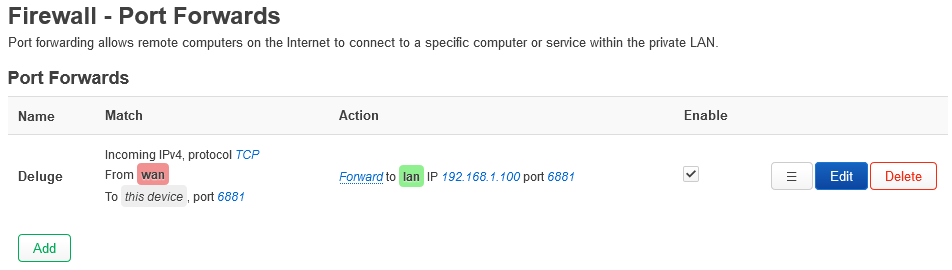
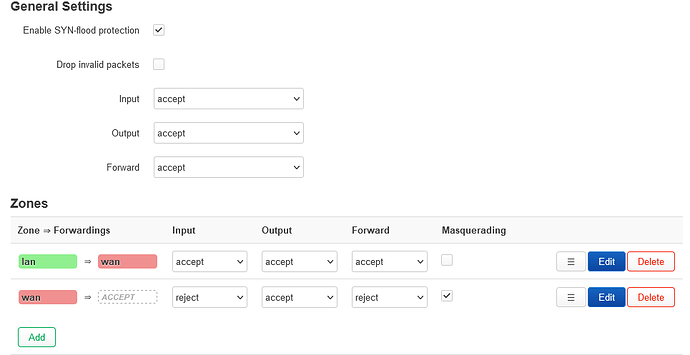
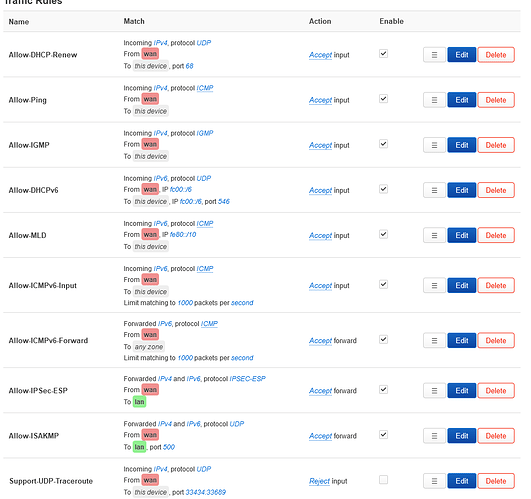
That has already been done or I wouldn't ask here.
Maybe this could be useful?
To me it means nothing, but maybe someone can help me translate?
I do notice that only udp ports seems to be used? It's TCP I have forwarded and need.
# tcpdump -i eth0 port 6881
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 262144 bytes
11:47:42.667701 IP c83-255-102-240.bredband.tele2.se.6881 > 191.96.168.163.26954: UDP, length 20
11:47:42.813905 IP 191.96.168.163.26954 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:42.814604 IP c83-255-102-240.bredband.tele2.se.6881 > 191.96.168.163.26954: UDP, length 88
11:47:42.965523 IP 191.96.168.163.26954 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:44.093875 IP 198.199.98.246.33175 > c83-255-102-240.bredband.tele2.se.6881: Flags [S], seq 304732107, win 14600, options [mss 1460,sackOK,TS val 2396823746 ecr 0,nop,wscale 8], length 0
11:47:44.094015 IP c83-255-102-240.bredband.tele2.se.6881 > 198.199.98.246.33175: Flags [R.], seq 0, ack 304732108, win 0, length 0
11:47:44.250204 IP 198.199.98.246.33176 > c83-255-102-240.bredband.tele2.se.6881: Flags [S], seq 738123338, win 14600, options [mss 1460,sackOK,TS val 2396823784 ecr 0,nop,wscale 8], length 0
11:47:44.250327 IP c83-255-102-240.bredband.tele2.se.6881 > 198.199.98.246.33176: Flags [R.], seq 0, ack 738123339, win 0, length 0
11:47:44.408649 IP 198.199.98.246.33177 > c83-255-102-240.bredband.tele2.se.6881: Flags [S], seq 2366862222, win 14600, options [mss 1460,sackOK,TS val 2396823824 ecr 0,nop,wscale 8], length 0
11:47:44.408797 IP c83-255-102-240.bredband.tele2.se.6881 > 198.199.98.246.33177: Flags [R.], seq 0, ack 2366862223, win 0, length 0
11:47:45.668234 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 20
11:47:45.794714 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:45.795333 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 88
11:47:45.924491 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:45.932521 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:45.933012 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 20
11:47:46.668254 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 20
11:47:46.796968 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:46.808588 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 548
11:47:46.940649 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:46.940650 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 355
11:47:46.941403 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 49
11:47:46.941487 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 20
11:47:47.066521 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:47.067145 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 363
11:47:47.194549 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:47.200732 IP cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:47.201243 IP c83-255-102-240.bredband.tele2.se.6881 > cpe105611a33503-cm105611a33501.cpe.net.cable.rogers.com.13685: UDP, length 20
11:47:47.668482 IP c83-255-102-240.bredband.tele2.se.6881 > n27-99-7-22.mrk1.qld.optusnet.com.au.57618: UDP, length 20
11:47:47.999636 IP n27-99-7-22.mrk1.qld.optusnet.com.au.57618 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:48.000385 IP c83-255-102-240.bredband.tele2.se.6881 > n27-99-7-22.mrk1.qld.optusnet.com.au.57618: UDP, length 88
11:47:48.331620 IP n27-99-7-22.mrk1.qld.optusnet.com.au.57618 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:48.331620 IP n27-99-7-22.mrk1.qld.optusnet.com.au.57618 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 26
11:47:48.332227 IP c83-255-102-240.bredband.tele2.se.6881 > n27-99-7-22.mrk1.qld.optusnet.com.au.57618: UDP, length 20
11:47:49.202886 IP 191.96.168.163.26954 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 88
11:47:49.203499 IP c83-255-102-240.bredband.tele2.se.6881 > 191.96.168.163.26954: UDP, length 20
11:47:49.203757 IP c83-255-102-240.bredband.tele2.se.6881 > 191.96.168.163.26954: UDP, length 220
11:47:49.203999 IP 191.96.168.163.26954 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 88
11:47:49.204446 IP c83-255-102-240.bredband.tele2.se.6881 > 191.96.168.163.26954: UDP, length 20
11:47:49.349726 IP 191.96.168.163.26954 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 20
11:47:49.349727 IP 191.96.168.163.26954 > c83-255-102-240.bredband.tele2.se.6881: UDP, length 26
11:47:49.350342 IP c83-255-102-240.bredband.tele2.se.6881 > 191.96.168.163.26954: UDP, length 20
^C
42 packets captured
42 packets received by filter
0 packets dropped by kernel
![]()