petkok
February 9, 2022, 8:45am
1
Hi folks,
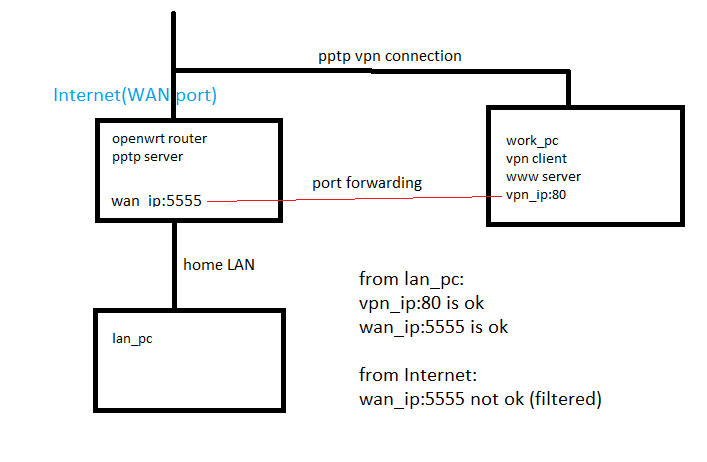
I have openwrt router at home
I set up pptp server on it so have connected my pc from work to my home lan
lan and vpn subnets are visible/routable to each other
I set up port forwarding from wan tcp port 5555 to my work pc port 80 (I need to show a web server outside) . I set up that using "luci\network\firewall\port forwards"
Is the firewall on your PC configured to accept incoming connections from a public IP address?
petkok
February 9, 2022, 2:57pm
3
Yes it is. If I forward port to pc from my home lan all is ok, problem exists only when forwarding is to pc from vpn subnet but firewall on my work-pc is set up properly
kukulo
February 9, 2022, 5:05pm
4
Are you trying to access web server from the same subnet that the web server works on?
petkok
February 9, 2022, 6:18pm
5
I'm trying to access server from internet, from lan and from vpn subnets it works.
kukulo
February 9, 2022, 7:05pm
6
Does the nmap on the open ports of your computer from internet show the port 80 open?
petkok
February 9, 2022, 7:25pm
7
I have forwarded port 5555 from router to port 80 at web server. nmap shows port 5555 as "filtered"
kukulo
February 9, 2022, 8:00pm
8
From wan connection is there an answer to http://ip_router_wan:5555 ? Put there you router's wan address. Is your wan connection to the web server a vpn connection? Or better, can you ping the web server from the computer?
kukulo
February 9, 2022, 8:59pm
10
Where is your public ip node? You need to forward from that node.
I would highly recommend that you remove PPTP and instead use something like Wireguard. PPTP is not secure -- it has many vulnerabilities that are so trivial to hack that it is deemed unsuitable for use on the internet.
But that said, looking at your config files will give us more insight into the potential issues.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/firewall
petkok
February 9, 2022, 10:16pm
13
psherman:
cat /etc/config/network
cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdad:daed:af63::/48'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device 'lan_eth0_1_dev'
option name 'eth0.1'
option macaddr 'ffffffffffff'
config interface 'wan'
option ifname 'eth0.2'
option proto 'pppoe'
option password 'xxxxxxxxx'
option ipv6 'auto'
option username 'xxxxxxxxxx'
config device 'wan_eth0_2_dev'
option name 'eth0.2'
option macaddr 'xxxxxxxxxxxxxxxx'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '4 2 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config route 'lan_vpn'
option interface 'vpn'
option target '192.168.1.0/24'
option gateway '192.168.6.1'
------------------------------------
cat /etc/config/firewall
config defaults
option output 'ACCEPT'
option synflood_protect '1'
option input 'ACCEPT'
option forward 'REJECT'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list device 'ppp+'
list network 'lan'
list network 'vpn'
config zone 'wan'
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'wan'
option input 'REJECT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option src '*'
option family 'ipv4'
option target 'ACCEPT'
list proto 'tcp'
option name 'Allow-Admin-Access'
option dest_port '22 80 8443'
list src_ip 'public_IP1/23'
list src_ip 'public_IP2/24'
list src_ip '192.168.0.0/16'
config include
option path '/etc/firewall.user'
config rule
list proto 'tcp'
option family 'ipv4'
option target 'REJECT'
option src '*'
option name 'Reject-Admin-Access'
option dest_port '22 80 8443'
config rule 'pptp'
option name 'Allow-PPTP'
option src 'wan'
option dest_port '1723'
option proto 'tcp'
option target 'ACCEPT'
config redirect
option dest_port '80'
option src 'wan'
option name 'www2work'
option src_dport '5555'
option target 'DNAT'
option dest_ip '192.168.6.3'
option dest 'lan'
This looks wrong. Your LAN is 192.168.1.0/24.
petkok
February 9, 2022, 10:40pm
15
192.168.6.1 is IP address of pptp server - it's from VPN subnet
Is the remote side (that has the server) using 192.168.1.0/24?
petkok
February 9, 2022, 10:56pm
17
remote side uses other subnet not 192.168.1.0/24. I have working routing between 192.168.1.0/24 and 192.168.6.3(vpn ip of remote side)
Ok... so that route doesn't seem like it belongs.
So the machine that hosts the server has the address 192.168.6.3? And it can be reached from the LAN of the far side network (192.168.1.0/24)?
Do you have a proper public IP on the WAN of your OpenWrt router? Have you tried port forwarding to a host on the 192.168.1.0/24 network to test if this is an ISP side issue or a problem with forwarding through the VPN?
petkok
February 9, 2022, 11:10pm
19
yes, yes and port forwarding to 192.168.1.0/24 works just fine
Just to verify, using the same ports, right (external 5555 > a host on 192.168.1.0/24 @ port 80)? And tested from outside the network?