Hi guys, any advice is much appreciated for this weird issue that has bothered me days... I am no good with cmd so I am using Luci, if the solution can be applied from Luci, that would be great as I can remember how to resolve it easier.
My setup:
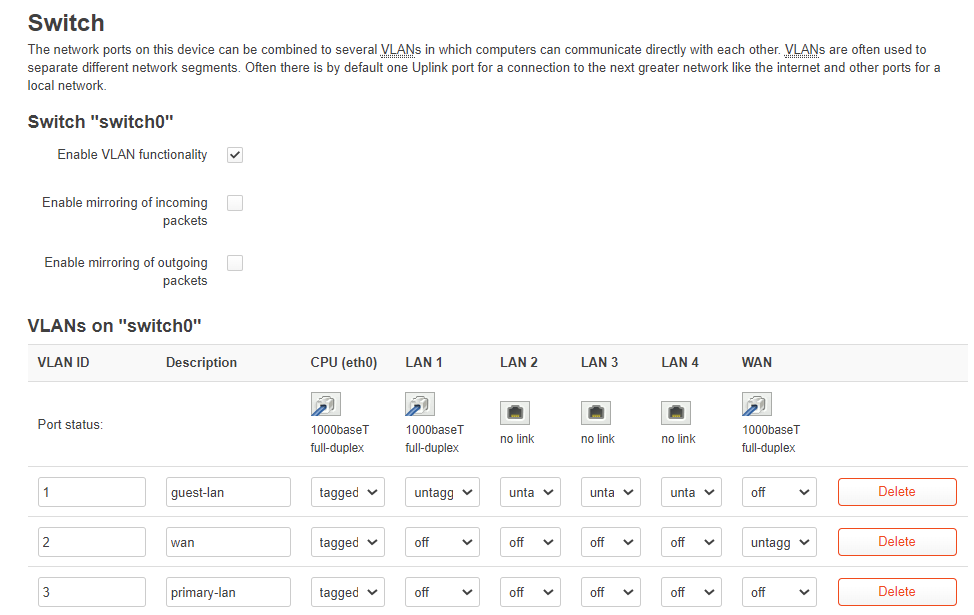
- I have added a new VLAN (ID 3) to have guest lan (with lan ethernet), wan and primary lan
- I have guest wifi (only 2.4G), and primary wifi (2.4G and 5G)
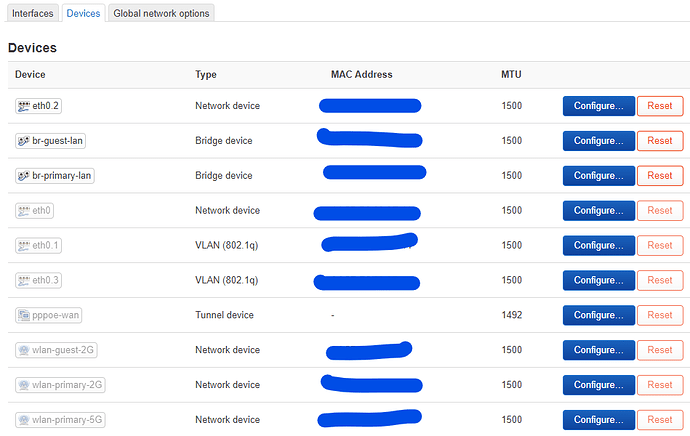
(screenshot in next posts due to new user restriction) - 2 bridges, one for guest lan + guest wifi, and one for primary wifi only for now (might use some ethernet ports in future)
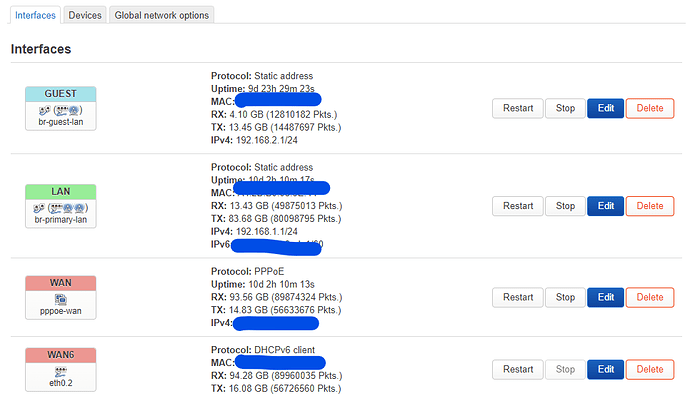
(screenshot in next posts due to new user restriction) - 4 interfaces
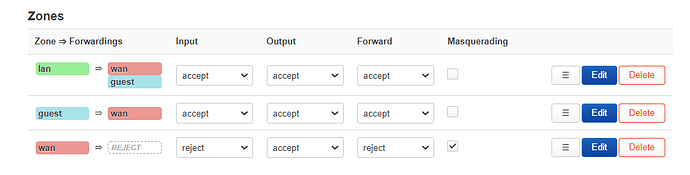
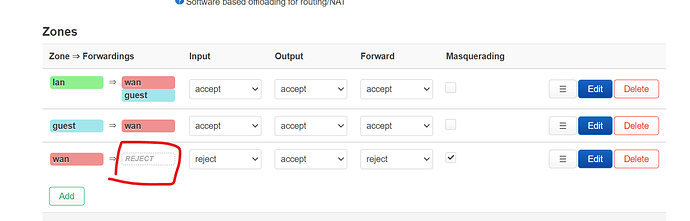
(screenshot in next posts due to new user restriction) - firewall zone, so that primary network can access guest but not the other way around. both primary and guest can access internet
(screenshot in next posts due to new user restriction) - a server connected via ethernet on the guest network (used to be on primary and working, then moved to guest network for IOT devices)
what I have tried:
- port forwarding from internet to primary network 192.168.1.x is working fine, to prove the router can forward internet traffic
- hit server on port 80 from primary or guest network is working fine, to prove server has port open
issue:
- port forwarding from internet to server on guest network 192.168.2.x is NOT working strangely
result of running:
ubus call system board; \
uci export network; uci export firewall; \
head -n -0 /etc/firewall.user; \
iptables-save -c; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru
is this:
{
"kernel": "5.4.188",
"hostname": "OpenWrt",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C7 v5",
"board_name": "tplink,archer-c7-v5",
"release": {
"distribution": "OpenWrt",
"version": "21.02.3",
"revision": "r16554-1d4dea6d4f",
"target": "ath79/generic",
"description": "OpenWrt 21.02.3 r16554-1d4dea6d4f"
}
}
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd8b:242a:b9ed::/48'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option device 'br-primary-lan'
config device
option name 'eth0.2'
option macaddr 'a4:2b:b0:03:9e:45'
config interface 'wan'
option proto 'pppoe'
option ipv6 'auto'
option device 'eth0.2'
option username '00008761793596@wba.nbnonline.com.au'
option password '00008761793596'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0t 2 3 4 5'
option vid '1'
option description 'guest-lan'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0t 1'
option vid '2'
option description 'wan'
config interface 'guest'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.2.1'
option type 'bridge'
option device 'br-guest-lan'
config switch_vlan
option device 'switch0'
option vlan '3'
option ports '0t'
option vid '3'
option description 'primary-lan'
config device
option type 'bridge'
option name 'br-guest-lan'
list ports 'eth0.1'
config device
option type 'bridge'
option name 'br-primary-lan'
list ports 'eth0.3'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option forward 'ACCEPT'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
config zone
option name 'guest'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'guest'
option forward 'ACCEPT'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option proto 'esp'
option target 'ACCEPT'
option dest 'lan'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config include
option path '/etc/firewall.user'
config forwarding
option src 'guest'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'guest'
config redirect
option target 'DNAT'
option src 'wan'
option src_dport '443'
option dest_port '443'
option name 'Mini PC port 443'
option dest_ip '192.168.2.200'
list proto 'tcp'
list proto 'udp'
option dest 'guest'
config redirect
option target 'DNAT'
option name 'Mini PC port 80'
option src 'wan'
option src_dport '80'
option dest_port '80'
list proto 'tcp'
list proto 'udp'
option dest_ip '192.168.2.200'
config rule
option name 'Mini PC Port 80'
option src 'wan'
list dest_ip '192.168.2.200'
option dest_port '80'
option target 'ACCEPT'
option dest 'guest'
option enabled '0'
# Generated by iptables-save v1.8.7 on Sat Jun 25 10:25:04 2022
*nat
:PREROUTING ACCEPT [4165:497425]
:INPUT ACCEPT [1264:91364]
:OUTPUT ACCEPT [1057:74083]
:POSTROUTING ACCEPT [59:4408]
:postrouting_guest_rule - [0:0]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_guest_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_guest_postrouting - [0:0]
:zone_guest_prerouting - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[4196:499189] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[2618:287543] -A PREROUTING -i br-primary-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[1316:194517] -A PREROUTING -i br-guest-lan -m comment --comment "!fw3" -j zone_guest_prerouting
[262:17129] -A PREROUTING -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[2571:217691] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1:328] -A POSTROUTING -o br-primary-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[39:2748] -A POSTROUTING -o br-guest-lan -m comment --comment "!fw3" -j zone_guest_postrouting
[2512:213283] -A POSTROUTING -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[39:2748] -A zone_guest_postrouting -m comment --comment "!fw3: Custom guest postrouting rule chain" -j postrouting_guest_rule
[0:0] -A zone_guest_postrouting -s 192.168.2.0/24 -d 192.168.2.200/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: Mini PC port 443 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_guest_postrouting -s 192.168.2.0/24 -d 192.168.2.200/32 -p udp -m udp --dport 443 -m comment --comment "!fw3: Mini PC port 443 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_guest_postrouting -s 192.168.2.0/24 -d 192.168.2.200/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: Mini PC port 80 (reflection)" -j SNAT --to-source 192.168.2.1
[0:0] -A zone_guest_postrouting -s 192.168.2.0/24 -d 192.168.2.200/32 -p udp -m udp --dport 80 -m comment --comment "!fw3: Mini PC port 80 (reflection)" -j SNAT --to-source 192.168.2.1
[1316:194517] -A zone_guest_prerouting -m comment --comment "!fw3: Custom guest prerouting rule chain" -j prerouting_guest_rule
[0:0] -A zone_guest_prerouting -s 192.168.2.0/24 -d 218.214.184.63/32 -p tcp -m tcp --dport 443 -m comment --comment "!fw3: Mini PC port 443 (reflection)" -j DNAT --to-destination 192.168.2.200:443
[0:0] -A zone_guest_prerouting -s 192.168.2.0/24 -d 218.214.184.63/32 -p udp -m udp --dport 443 -m comment --comment "!fw3: Mini PC port 443 (reflection)" -j DNAT --to-destination 192.168.2.200:443
[0:0] -A zone_guest_prerouting -s 192.168.2.0/24 -d 218.214.184.63/32 -p tcp -m tcp --dport 80 -m comment --comment "!fw3: Mini PC port 80 (reflection)" -j DNAT --to-destination 192.168.2.200:80
[0:0] -A zone_guest_prerouting -s 192.168.2.0/24 -d 218.214.184.63/32 -p udp -m udp --dport 80 -m comment --comment "!fw3: Mini PC port 80 (reflection)" -j DNAT --to-destination 192.168.2.200:80
[1:328] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[2618:287543] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
[2512:213283] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[2512:213283] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[262:17129] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
[22:1280] -A zone_wan_prerouting -p tcp -m tcp --dport 443 -m comment --comment "!fw3: Mini PC port 443" -j DNAT --to-destination 192.168.2.200:443
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 443 -m comment --comment "!fw3: Mini PC port 443" -j DNAT --to-destination 192.168.2.200:443
[9:484] -A zone_wan_prerouting -p tcp -m tcp --dport 80 -m comment --comment "!fw3: Mini PC port 80" -j DNAT --to-destination 192.168.2.200:80
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 80 -m comment --comment "!fw3: Mini PC port 80" -j DNAT --to-destination 192.168.2.200:80
COMMIT
# Completed on Sat Jun 25 10:25:04 2022
# Generated by iptables-save v1.8.7 on Sat Jun 25 10:25:04 2022
*mangle
:PREROUTING ACCEPT [96835:31436563]
:INPUT ACCEPT [8210:1048789]
:FORWARD ACCEPT [87214:30124450]
:OUTPUT ACCEPT [6557:3627184]
:POSTROUTING ACCEPT [93754:33750612]
[1123:69556] -A FORWARD -o pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[1194:68960] -A FORWARD -i pppoe-wan -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -o eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
[0:0] -A FORWARD -i eth0.2 -p tcp -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: Zone wan MTU fixing" -j TCPMSS --clamp-mss-to-pmtu
COMMIT
# Completed on Sat Jun 25 10:25:04 2022
# Generated by iptables-save v1.8.7 on Sat Jun 25 10:25:04 2022
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:forwarding_guest_rule - [0:0]
:forwarding_lan_rule - [0:0]
:forwarding_rule - [0:0]
:forwarding_wan_rule - [0:0]
:input_guest_rule - [0:0]
:input_lan_rule - [0:0]
:input_rule - [0:0]
:input_wan_rule - [0:0]
:output_guest_rule - [0:0]
:output_lan_rule - [0:0]
:output_rule - [0:0]
:output_wan_rule - [0:0]
:reject - [0:0]
:syn_flood - [0:0]
:zone_guest_dest_ACCEPT - [0:0]
:zone_guest_forward - [0:0]
:zone_guest_input - [0:0]
:zone_guest_output - [0:0]
:zone_guest_src_ACCEPT - [0:0]
:zone_lan_dest_ACCEPT - [0:0]
:zone_lan_forward - [0:0]
:zone_lan_input - [0:0]
:zone_lan_output - [0:0]
:zone_lan_src_ACCEPT - [0:0]
:zone_wan_dest_ACCEPT - [0:0]
:zone_wan_dest_REJECT - [0:0]
:zone_wan_forward - [0:0]
:zone_wan_input - [0:0]
:zone_wan_output - [0:0]
:zone_wan_src_REJECT - [0:0]
[962:79803] -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT
[7249:969026] -A INPUT -m comment --comment "!fw3: Custom input rule chain" -j input_rule
[4005:489504] -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[104:4640] -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood
[871:60828] -A INPUT -i br-primary-lan -m comment --comment "!fw3" -j zone_lan_input
[2107:401872] -A INPUT -i br-guest-lan -m comment --comment "!fw3" -j zone_guest_input
[266:16822] -A INPUT -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_input
[0:0] -A INPUT -i eth0.2 -m comment --comment "!fw3" -j zone_wan_input
[87214:30124450] -A FORWARD -m comment --comment "!fw3: Custom forwarding rule chain" -j forwarding_rule
[85499:29954740] -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[1191:97127] -A FORWARD -i br-primary-lan -m comment --comment "!fw3" -j zone_lan_forward
[481:70083] -A FORWARD -i br-guest-lan -m comment --comment "!fw3" -j zone_guest_forward
[43:2500] -A FORWARD -i pppoe-wan -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -i eth0.2 -m comment --comment "!fw3" -j zone_wan_forward
[0:0] -A FORWARD -m comment --comment "!fw3" -j reject
[962:79803] -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT
[5598:3548573] -A OUTPUT -m comment --comment "!fw3: Custom output rule chain" -j output_rule
[4555:3474446] -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT
[2:656] -A OUTPUT -o br-primary-lan -m comment --comment "!fw3" -j zone_lan_output
[5:1640] -A OUTPUT -o br-guest-lan -m comment --comment "!fw3" -j zone_guest_output
[1036:71831] -A OUTPUT -o pppoe-wan -m comment --comment "!fw3" -j zone_wan_output
[0:0] -A OUTPUT -o eth0.2 -m comment --comment "!fw3" -j zone_wan_output
[112:4693] -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset
[8:777] -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable
[104:4640] -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN
[0:0] -A syn_flood -m comment --comment "!fw3" -j DROP
[11:1952] -A zone_guest_dest_ACCEPT -o br-guest-lan -m comment --comment "!fw3" -j ACCEPT
[481:70083] -A zone_guest_forward -m comment --comment "!fw3: Custom guest forwarding rule chain" -j forwarding_guest_rule
[481:70083] -A zone_guest_forward -m comment --comment "!fw3: Zone guest to wan forwarding policy" -j zone_wan_dest_ACCEPT
[0:0] -A zone_guest_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_guest_forward -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
[2107:401872] -A zone_guest_input -m comment --comment "!fw3: Custom guest input rule chain" -j input_guest_rule
[0:0] -A zone_guest_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[2107:401872] -A zone_guest_input -m comment --comment "!fw3" -j zone_guest_src_ACCEPT
[5:1640] -A zone_guest_output -m comment --comment "!fw3: Custom guest output rule chain" -j output_guest_rule
[5:1640] -A zone_guest_output -m comment --comment "!fw3" -j zone_guest_dest_ACCEPT
[2107:401872] -A zone_guest_src_ACCEPT -i br-guest-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[2:656] -A zone_lan_dest_ACCEPT -o br-primary-lan -m comment --comment "!fw3" -j ACCEPT
[1191:97127] -A zone_lan_forward -m comment --comment "!fw3: Custom lan forwarding rule chain" -j forwarding_lan_rule
[1191:97127] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to wan forwarding policy" -j zone_wan_dest_ACCEPT
[6:312] -A zone_lan_forward -m comment --comment "!fw3: Zone lan to guest forwarding policy" -j zone_guest_dest_ACCEPT
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[871:60828] -A zone_lan_input -m comment --comment "!fw3: Custom lan input rule chain" -j input_lan_rule
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[871:60828] -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT
[2:656] -A zone_lan_output -m comment --comment "!fw3: Custom lan output rule chain" -j output_lan_rule
[2:656] -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT
[871:60828] -A zone_lan_src_ACCEPT -i br-primary-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT
[17:1022] -A zone_wan_dest_ACCEPT -o pppoe-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[2685:237707] -A zone_wan_dest_ACCEPT -o pppoe-wan -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP
[0:0] -A zone_wan_dest_ACCEPT -o eth0.2 -m comment --comment "!fw3" -j ACCEPT
[0:0] -A zone_wan_dest_REJECT -o pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_dest_REJECT -o eth0.2 -m comment --comment "!fw3" -j reject
[43:2500] -A zone_wan_forward -m comment --comment "!fw3: Custom wan forwarding rule chain" -j forwarding_wan_rule
[0:0] -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT
[0:0] -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT
[43:2500] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT
[266:16822] -A zone_wan_input -m comment --comment "!fw3: Custom wan input rule chain" -j input_wan_rule
[0:0] -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT
[146:11352] -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT
[0:0] -A zone_wan_input -p igmp -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[120:5470] -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT
[1036:71831] -A zone_wan_output -m comment --comment "!fw3: Custom wan output rule chain" -j output_wan_rule
[1036:71831] -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT
[120:5470] -A zone_wan_src_REJECT -i pppoe-wan -m comment --comment "!fw3" -j reject
[0:0] -A zone_wan_src_REJECT -i eth0.2 -m comment --comment "!fw3" -j reject
COMMIT
# Completed on Sat Jun 25 10:25:04 2022
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
8: br-primary-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-primary-lan
valid_lft forever preferred_lft forever
11: pppoe-wan: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1492 qdisc fq_codel state UNKNOWN qlen 3
inet 218.214.184.63 peer 202.138.24.193/32 scope global pppoe-wan
valid_lft forever preferred_lft forever
15: br-guest-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-guest-lan
valid_lft forever preferred_lft forever
default via 202.138.24.193 dev pppoe-wan
192.168.1.0/24 dev br-primary-lan scope link src 192.168.1.1
192.168.2.0/24 dev br-guest-lan scope link src 192.168.2.1
202.138.24.193 dev pppoe-wan scope link src 218.214.184.63
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev br-primary-lan table local scope link src 192.168.1.1
local 192.168.1.1 dev br-primary-lan table local scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-primary-lan table local scope link src 192.168.1.1
broadcast 192.168.2.0 dev br-guest-lan table local scope link src 192.168.2.1
local 192.168.2.1 dev br-guest-lan table local scope host src 192.168.2.1
broadcast 192.168.2.255 dev br-guest-lan table local scope link src 192.168.2.1
local 218.214.184.63 dev pppoe-wan table local scope host src 218.214.184.63
0: from all lookup local
32766: from all lookup main
32767: from all lookup default