Little bit background
I am using GLinet AR-150. It has 3 interfaces: eth0 (single WAN port), eth1 (single LAN port), and wlan0 (WIFI). eth1 and wlan0 are bridged together (br-lan).
I recently got 2 connections from 2 different ISPs and thought to remove eth1 from the bridge and use it as a 2nd WAN port.
Both of my ISPs provided static IPs for router configuration.
ISP-1 (172.22.36.151/25) (Planned about connecting it to WAN-eth0)
ISP-2 (172.30.138.151/24) (Planned about connecting it to WAN2-eth1)
I used the following network config /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd22:bbe3:e6d8::/48'
config interface 'wan'
option ifname 'eth0'
option proto 'static'
option ipaddr '172.22.36.151'
option netmask '255.255.255.128'
option gateway '172.22.36.129'
option dns '8.8.8.8'
option metric '10'
config interface 'wan2'
option proto 'static'
option ifname 'eth1'
option ipaddr '172.30.138.151'
option netmask '255.255.255.0'
option gateway '172.30.138.1'
option dns '8.8.8.8'
option macaddr 'E4:95:6E:42:97:33'
option metric '20'
config interface 'wan6'
option ifname 'eth0'
option proto 'dhcpv6'
config interface 'lan'
#REMOVED THE ETH1 WLAN0 BRIDGE. I WILL USE THIS LOGICAL INTERFACE `LAN` IN /ETC/CONFIG/WIRELESS
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option hostname 'GL-AR150-732'
option ipaddr '192.168.8.1'

The outputs of ip a show and ip route show are attached at the end of this post.
Now, I connected the ISP cables to the respective pre-planned ports.

Now, I am specifying the interface to use for ping using:
ping -I eth0 8.8.8.8
ping -I eth1 8.8.8.8
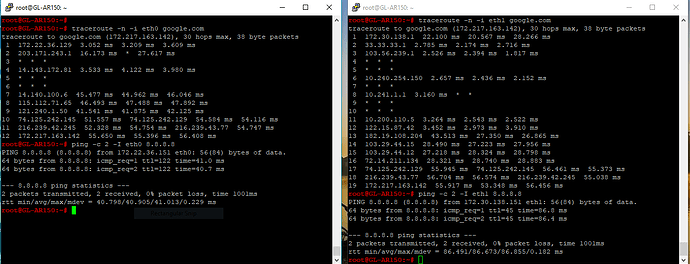
Expected outcome
In the above commands, the ping should be sent via eth0 and eth1 respectively. The expected outcome is also mentioned in the mwan3 documentation.
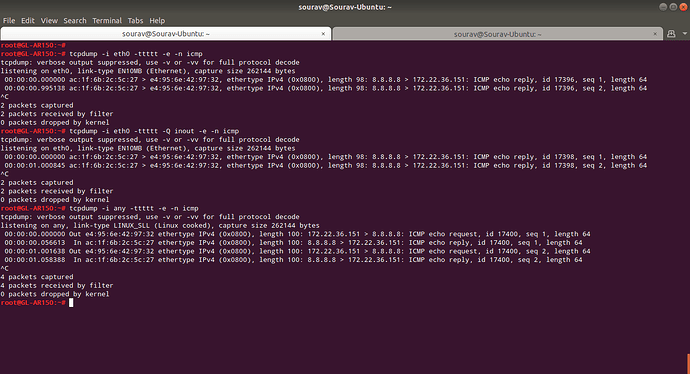
The problem I am facing
Both the ping commands are being sent from eth1
Most probably because eth1 gateway has a lower metric.
If I use lower metric for eth0 gateway, then all pings are being sent from eth0 regardless of what interface I specify.
This behavior is similar to IP aliasing on a single interface. But I am using 2 completely different interfaces and if I specify the interface to use, then the default gateway metric should not matter. (see the expected outcome screenshot, they have 2 gateway with different metrics) The ping should be sent from my specified interface.
Please help.
Output of "ip route show"
default via 172.30.138.1 dev eth1 src 172.30.138.151 metric 10
default via 172.22.36.129 dev eth0 src 172.22.36.151 metric 20
172.22.36.128/25 dev eth0 proto static scope link metric 10
172.30.138.0/24 dev eth1 proto static scope link metric 20
192.168.8.0/24 dev wlan0 proto kernel scope link src 192.168.8.1
Output of "ip a show"
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether e4:95:6e:42:97:32 brd ff:ff:ff:ff:ff:ff
inet 172.22.36.151/25 brd 172.22.36.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::e695:6eff:fe42:9732/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether e4:95:6e:42:97:33 brd ff:ff:ff:ff:ff:ff
inet 172.30.138.151/24 brd 172.30.138.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::e695:6eff:fe42:9733/64 scope link dadfailed tentative
valid_lft forever preferred_lft forever
4: teql0: <NOARP> mtu 1500 qdisc noop state DOWN group default qlen 100
link/void
9: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether e4:95:6e:42:97:32 brd ff:ff:ff:ff:ff:ff
inet 192.168.8.1/24 brd 192.168.8.255 scope global wlan0
valid_lft forever preferred_lft forever
inet6 fd22:bbe3:e6d8::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::e695:6eff:fe42:9732/64 scope link
valid_lft forever preferred_lft forever