Hi,
I'm new to OpenWRT, so first of all, I would like to say hello to everyone. I'm not new to - we can say - routing. Maybe I'm not an expert, but 8 years ago, I had a CCNA certificate. But time flies and everything has changed.
I've decided to start using VPN to enhance my security and privacy at home. However, my real problem is that some government services provided via the Internet are not accessible through the Mullvad VPN server in the country I've selected.
Additionally, there are some Internet websites that I would like to access via WAN.
I read an article about PBR. I have configured OpenVPN and PBR. But finally, all traffic goes through VPN.
Where should I find a solution? What kind of logs can the whole community use to resolve my problem?
uci export network; uci export dhcp; ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
is
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc3:82cb:4d29::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
config device
option name 'wan'
option macaddr '8C:DE:F9:92:E1:A4'
config device
option name 'phy0-ap0'
config interface 'MULLAD_VPN'
option proto 'none'
option device 'tun0'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
list dhcp_option '6,10.8.0.1,193.138.218.74'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'manwe-storage'
option dns '1'
option mac '00:11:32:48:74:E7'
option ip '192.168.1.100'
config host
option name 'manwe-storage-lan2'
option dns '1'
option mac '00:11:32:48:74:E8'
option ip '192.168.1.101'
lrwxrwxrwx 1 root root 16 May 16 20:54 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 47 May 18 14:07 /tmp/resolv.conf
-rw-r--r-- 1 root root 84 May 18 13:13 /tmp/resolv.conf.d/resolv.conf.auto
/tmp/resolv.conf.d:
-rw-r--r-- 1 root root 84 May 18 13:13 resolv.conf.auto
==> /etc/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf <==
search lan
nameserver 127.0.0.1
nameserver ::1
==> /tmp/resolv.conf.d <==
head: /tmp/resolv.conf.d: I/O error
==> /tmp/resolv.conf.d/resolv.conf.auto <==
# Interface wan
nameserver 212.75.96.2
nameserver 212.75.122.2
search supermedia.pl
root@OpenWrt:~# /etc/init.d/pbr restart
Activating traffic killswitch [✓]
Removing routing for 'wan/212.180.183.1/::/0' [✓]
Removing routing for 'MULLAD_VPN/tun0/10.10.0.12/fdda:d0d0:cafe:1196::100a/64' [✓]
Deactivating traffic killswitch [✓]
pbr 1.1.1-7 (nft) stopped [✓]
Activating traffic killswitch [✓]
Setting up routing for 'wan/212.180.183.1/::/0' [✓]
Setting up routing for 'MULLAD_VPN/tun0/10.10.0.12/fdda:d0d0:cafe:1196::100a/64' [✓]
Routing 'my ip' via wan [✓]
Routing 'gmail by wan' via wan [✓]
Routing 'speedtest to vpn' via wan [✓]
Routing 'Plex/Emby Remote Servers' via wan [✓]
Restarting dnsmasq [✓]
Deactivating traffic killswitch [✓]
pbr 1.1.1-7 monitoring interfaces: wan MULLAD_VPN
pbr 1.1.1-7 (nft) started with gateways:
wan/212.180.183.1/::/0
MULLAD_VPN/tun0/10.10.0.12/fdda:d0d0:cafe:1196::100a/64 [✓]
root@OpenWrt:~# cat /etc/config/pbr
config pbr 'config'
option enabled '1'
option verbosity '2'
option strict_enforcement '1'
option resolver_set 'dnsmasq.nftset'
option ipv6_enabled '1'
list ignored_interface 'vpnserver'
list ignored_interface 'wgserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
config include
option path '/usr/share/pbr/pbr.user.aws'
option enabled '0'
config include
option path '/usr/share/pbr/pbr.user.netflix'
option enabled '0'
config policy
option name 'my ip'
option dest_addr 'whatismyipaddress.com'
option interface 'wan'
config policy
option name 'gmail by wan'
option dest_addr 'mail.google.com'
option interface 'wan'
config policy
option name 'speedtest to vpn'
option dest_addr 'speedtest.pl'
option interface 'wan'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.emby.media'
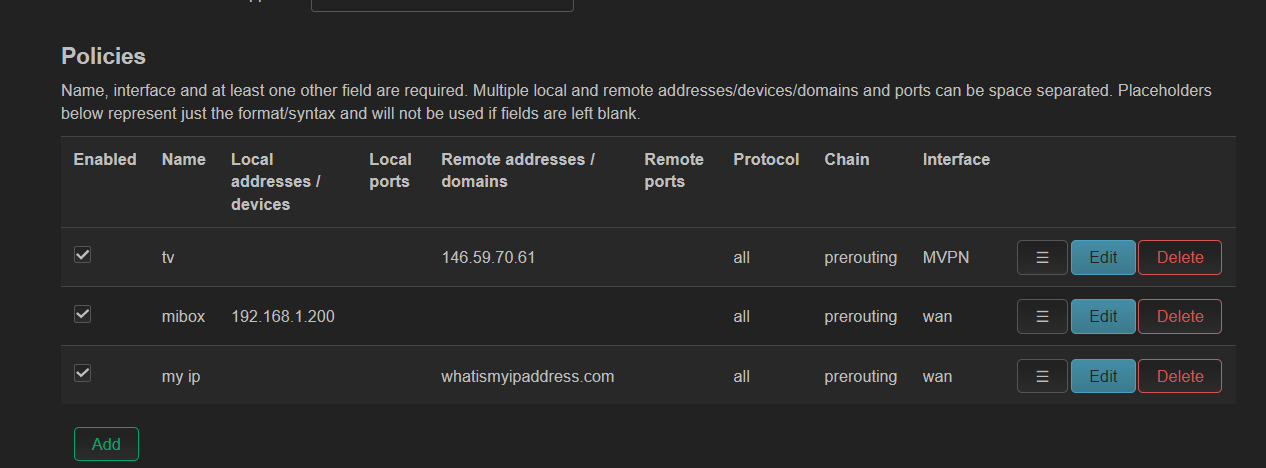
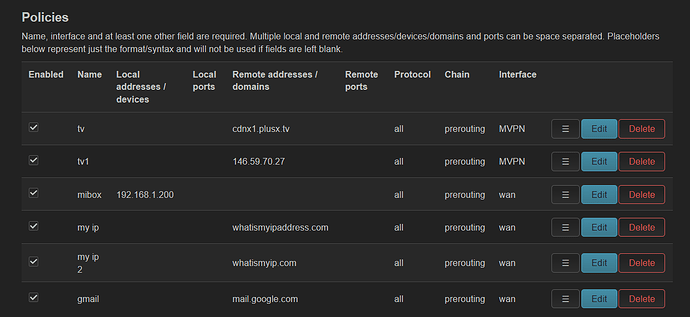
I woud like to add that when i add policy (using luci) based on source ip address (i.e. my laptop) everything works fine and traffic goes thru WAN
whatismyip.com in pbr should go by wan using domain name
ipaddress.my in pbr is should go by wan using ip adress