Hi Forum,
I herewith more or less revisit a problem that I have sought help about before (Failing (again) to get IPv6 working with PBR). To summarise, at the time my trials to have a policy route the traffic generated by my laptop both over IPv4 and IPv6 to a VPN server other than the one that acted as my default gateway, consistently failed. Thanks to the help of @egc I finally got things sorted out, and for some time I was able to let my laptop connect to a different server than my desktops which were not subject to my policy.
Things changed when I updated the pbr and luci-app-pbr packages from version 1.1.1-7 to the next. Now I not only noted the highly erratic behaviour of the policy routing tab under ‘Services' in LuCi that others have reported about as well (on which I’ll come back in a separate thread), I also couldn’t get my policy to work anymore, whatever I tried. I more or less gave up on the pbr package at the time, made the VPN server my laptop is supposed to connect to my default gateway, and sort of called it quits. Thereafter, however, I also began to run into trouble with the sinking ship that was my VPN provider (Perfect Privacy), which finally led me to switch this week to AirVPN. Now again being on a stable VPN, I decided to reinstall pbr and luci-app-pbr again, and see whether I could make things behave like I want.
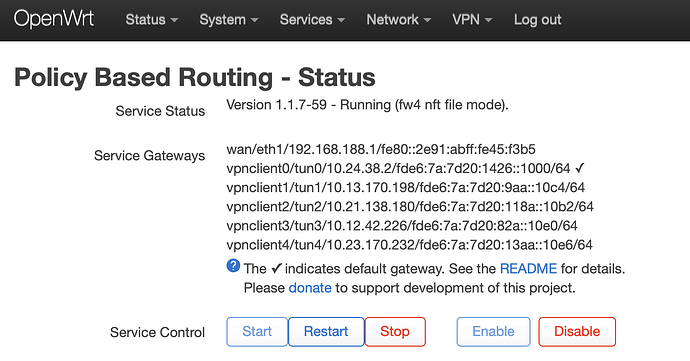
Unfortunately, I cannot. While assigning a default gateway seems to work, resulting in traffic generated by both my desktops being routed through the chosen server (both over IPv4 and IPv6), the policy that I created based on the MAC address of my laptop, and which is meant to route the latter’s traffic through a different server, simply doesn’t do anything; traffic from my laptop also consistently runs through my default gateway (both over IPv4 and IPv6, that is).
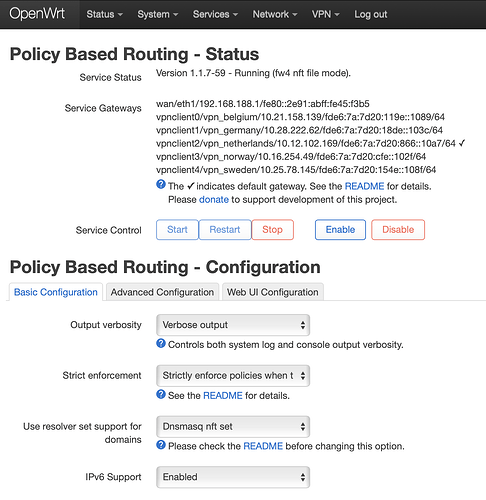
Please note that even while this screenshot shows pbr is running in 'fw4 nft file mode', in /etc/config/pbr the option enabled consistently shows as set to '0' (for which see the contents of this file at the end), which may well be the result of the erratic behaviour of the UI of luci-app-pbr package as referred to above. Setting it manually to '1' in Terminal doesn't solve my problem, however.
As per the advice of @egc, given in thread 204457, I amended AirVPN’s OpenVPN configuration script for what is meant to be my default gateway (‘the Netherlands’) with the following lines:
redirect-gateway def1redirect-gateway ipv6server-poll-timeout 10
whereas the following lines were added to AirVPN’s OpenVPN configuration scripts of all other VPN servers, and hence the server (‘Sweden’) traffic from my laptop is meant being routed through:
pull-filter ignore “redirect-gateway"pull-filter ignore "redirect-gateway ipv6”
Like said, while still on pbr version 1.1.1-7 this configuration worked, but now, while on version 1.1.7-59, it doesn’t. I haven’t got a clue as to why, and I am therefore warmly welcoming any suggestions that could help me to make my routing policy work .
To enable you to analyse my current setup, the following output. In case any additional information is needed, feel free to let me know.
ubus call system board
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.167",
"hostname": "OpenWrt",
"system": "Intel(R) Celeron(R) J6412 @ 2.00GHz",
"model": "Protectli VP2420",
"board_name": "protectli-vp2420",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "23.05.5",
"revision": "r24106-10cc5fcd00",
"target": "x86/64",
"description": "OpenWrt 23.05.5 r24106-10cc5fcd00"
}
}
root@OpenWrt:~#
cat /etc/config/network
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth2'
list ports 'eth3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ip6assign '60'
option broadcast ‘redacted.255'
list ipaddr 'redacted.1/24'
list dns '45.90.28.234'
list dns '45.90.30.234'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
option peerdns '0'
list dns '45.90.28.234'
list dns '45.90.30.234'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '2a07:a8c0::49:2c58'
list dns '2a07:a8c1::49:2c58'
config device
option name 'tun0'
config device
option name 'eth0'
config interface 'vpnclient0'
option proto 'none'
option device 'vpn_belgium'
config interface 'vpnclient1'
option proto 'none'
option device 'vpn_germany'
config interface 'vpnclient2'
option proto 'none'
option device 'vpn_netherlands'
config interface 'vpnclient3'
option proto 'none'
option device 'vpn_norway'
config interface 'vpnclient4'
option proto 'none'
option device 'vpn_sweden'
root@OpenWrt:~#
cat /etc/config/dhcp
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option localservice '1'
option ednspacket_max '1232'
list dhcp_option '6,45.90.28.234,45.90.30.234'
list server '127.0.0.1#5054'
list server '/mask.icloud.com/'
list server '/mask-h2.icloud.com/'
list server '/use-application-dns.net/'
list server '127.0.0.1#5053'
option resolvfile '/tmp/resolv.conf.vpn'
option doh_backup_noresolv '-1'
option noresolv '1'
list doh_backup_server '127.0.0.1#5054'
list doh_backup_server '/mask.icloud.com/'
list doh_backup_server '/mask-h2.icloud.com/'
list doh_backup_server '/use-application-dns.net/'
list doh_backup_server '127.0.0.1#5053'
list doh_server '127.0.0.1#5053'
config dhcp 'lan'
option interface 'lan'
option start '2'
option limit '49'
option leasetime '2m'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option preferred_lifetime '12h'
option force '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
option preferred_lifetime '12h'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'MacBook-Pro-M3'
option ip ‘redacted.2’
list mac 'redacted'
option leasetime 'infinite'
option duid 'redacted'
config host
option name 'Mac-Mini-M1'
option ip 'redacted.15'
option duid 'redacted'
list tag 'Mac'
list mac 'redacted'
option leasetime 'infinite'
config host
option name 'Mac-Studio-M1-Max'
option ip 'redacted.29'
option duid 'redacted'
list mac 'redacted'
list tag 'Mac'
config host
option ip 'redacted.42'
option name 'iPhone-13-mini'
list mac 'redacted'
option duid 'redacted'
list tag 'iPhone'
config host
option ip 'redacted.23'
option name 'MikroTik-CRS305-1G-4'
list mac 'redacted'
list tag 'Switch'
config host
option name 'QNAP-QSW-M408-4C'
option ip 'redacted.16'
list mac 'redacted'
list tag 'Switch'
config host
option name 'QNAP-TS453DU-NAS'
option ip 'redacted.19'
list tag 'NAS'
list mac 'redacted'
option leasetime 'infinite'
config host
option name 'Fitlet2-NAA'
option ip 'redacted.47'
list tag 'NAA'
list mac 'redacted'
option duid 'redacted'
config host
option name 'Apple-Airport-Time-Capsule'
option ip 'redacted.44'
option duid 'redacted'
list mac 'redacted'
list tag 'Airport'
config host
option duid 'redacted'
option mac 'redacted'
root@OpenWrt:~#
cat /etc/config/firewall
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option masq6 '1'
list network 'wan'
list network 'wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn_fw'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option masq6 '1'
option mtu_fix '1'
list network 'vpnclient0'
list network 'vpnclient1'
list network 'vpnclient2'
list network 'vpnclient3'
list network 'vpnclient4'
config forwarding
option src 'lan'
option dest 'vpn_fw'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/firewall.include'
root@OpenWrt:~#
cat /etc/config/pbr
root@OpenWrt:~# cat /etc/config/pbr
config pbr 'config'
option enabled '0'
option verbosity '2'
option strict_enforcement '1'
option resolver_set 'dnsmasq.nftset'
list resolver_instance '*'
option ipv6_enabled '1'
list ignored_interface 'vpnserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_boot_delay '0'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
option nft_rule_counter '0'
option nft_set_auto_merge '1'
option nft_set_counter '0'
option nft_set_flags_interval '1'
option nft_set_flags_timeout '0'
option nft_set_policy 'performance'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
list supported_interface 'vpn_belgium vpn_germany vpn_netherlands vpn_norway vpn_sweden'
config policy
option name 'MacBook Pro M3'
option src_addr ‘redacted'
option interface 'vpnclient4'
root@OpenWrt:~#
opkg list-installed
root@OpenWrt:~# opkg list-installed
ath10k-firmware-qca6174 - 20230804-1
attendedsysupgrade-common - 8
auc - 0.3.2-1
base-files - 1562-r24106-10cc5fcd00
bnx2-firmware - 20230804-1
busybox - 1.36.1-1
ca-bundle - 20230311-1
cgi-io - 2022-08-10-901b0f04-21
dnsmasq-full - 2.90-2
dropbear - 2022.82-6
e2fsprogs - 1.47.0-2
firewall4 - 2023-09-01-598d9fbb-1
fstools - 2023-02-28-bfe882d5-1
fwtool - 2019-11-12-8f7fe925-1
getrandom - 2022-08-13-4c7b720b-2
grub2 - 2.06-5
grub2-bios-setup - 2.06-5
grub2-efi - 2.06-5
hostapd-common - 2023-09-08-e5ccbfc6-8
https-dns-proxy - 2023.12.26-1
ip-full - 6.3.0-1
ipset - 7.17-1
iw - 5.19-1
iwinfo - 2023-07-01-ca79f641-1
jansson4 - 2.14-3
jshn - 2023-05-23-75a3b870-1
jsonfilter - 2024-01-23-594cfa86-1
kernel - 5.15.167-1-59d1431675acc6823a33c7eb2323daeb
kmod-amazon-ena - 5.15.167-1
kmod-amd-xgbe - 5.15.167-1
kmod-ath - 5.15.167+6.1.110-1-1
kmod-ath10k - 5.15.167+6.1.110-1-1
kmod-bnx2 - 5.15.167-1
kmod-button-hotplug - 5.15.167-3
kmod-cfg80211 - 5.15.167+6.1.110-1-1
kmod-crypto-acompress - 5.15.167-1
kmod-crypto-aead - 5.15.167-1
kmod-crypto-ccm - 5.15.167-1
kmod-crypto-cmac - 5.15.167-1
kmod-crypto-crc32c - 5.15.167-1
kmod-crypto-ctr - 5.15.167-1
kmod-crypto-gcm - 5.15.167-1
kmod-crypto-gf128 - 5.15.167-1
kmod-crypto-ghash - 5.15.167-1
kmod-crypto-hash - 5.15.167-1
kmod-crypto-hmac - 5.15.167-1
kmod-crypto-manager - 5.15.167-1
kmod-crypto-null - 5.15.167-1
kmod-crypto-rng - 5.15.167-1
kmod-crypto-seqiv - 5.15.167-1
kmod-crypto-sha512 - 5.15.167-1
kmod-e1000 - 5.15.167-1
kmod-e1000e - 5.15.167-1
kmod-forcedeth - 5.15.167-1
kmod-fs-vfat - 5.15.167-1
kmod-hwmon-core - 5.15.167-1
kmod-i2c-algo-bit - 5.15.167-1
kmod-i2c-core - 5.15.167-1
kmod-igb - 5.15.167-1
kmod-igc - 5.15.167-1
kmod-input-core - 5.15.167-1
kmod-ip6tables - 5.15.167-1
kmod-ipt-conntrack - 5.15.167-1
kmod-ipt-core - 5.15.167-1
kmod-ipt-ipset - 5.15.167-1
kmod-ipt-nat - 5.15.167-1
kmod-ipt-nat6 - 5.15.167-1
kmod-ixgbe - 5.15.167-1
kmod-lib-crc-ccitt - 5.15.167-1
kmod-lib-crc32c - 5.15.167-1
kmod-lib-lzo - 5.15.167-1
kmod-libphy - 5.15.167-1
kmod-mac80211 - 5.15.167+6.1.110-1-1
kmod-mdio - 5.15.167-1
kmod-mdio-devres - 5.15.167-1
kmod-mii - 5.15.167-1
kmod-nf-conntrack - 5.15.167-1
kmod-nf-conntrack-netlink - 5.15.167-1
kmod-nf-conntrack6 - 5.15.167-1
kmod-nf-flow - 5.15.167-1
kmod-nf-ipt - 5.15.167-1
kmod-nf-ipt6 - 5.15.167-1
kmod-nf-log - 5.15.167-1
kmod-nf-log6 - 5.15.167-1
kmod-nf-nat - 5.15.167-1
kmod-nf-nat6 - 5.15.167-1
kmod-nf-reject - 5.15.167-1
kmod-nf-reject6 - 5.15.167-1
kmod-nfnetlink - 5.15.167-1
kmod-nft-core - 5.15.167-1
kmod-nft-fib - 5.15.167-1
kmod-nft-nat - 5.15.167-1
kmod-nft-offload - 5.15.167-1
kmod-nls-base - 5.15.167-1
kmod-nls-cp437 - 5.15.167-1
kmod-nls-iso8859-1 - 5.15.167-1
kmod-nls-utf8 - 5.15.167-1
kmod-phy-realtek - 5.15.167-1
kmod-ppp - 5.15.167-1
kmod-pppoe - 5.15.167-1
kmod-pppox - 5.15.167-1
kmod-pps - 5.15.167-1
kmod-ptp - 5.15.167-1
kmod-r8169 - 5.15.167-1
kmod-slhc - 5.15.167-1
kmod-tg3 - 5.15.167-1
kmod-tun - 5.15.167-1
libblkid1 - 2.39-2
libblobmsg-json20230523 - 2023-05-23-75a3b870-1
libbpf1 - 1.2.2-1
libc - 1.2.4-4
libcares - 1.27.0-1
libcomerr0 - 1.47.0-2
libcurl4 - 8.7.1-r1
libelf1 - 0.189-1
libev - 4.33-2
libext2fs2 - 1.47.0-2
libf2fs6 - 1.16.0-1
libgcc1 - 12.3.0-4
libgmp10 - 6.2.1-1
libipset13 - 7.17-1
libiwinfo-data - 2023-07-01-ca79f641-1
libiwinfo20230701 - 2023-07-01-ca79f641-1
libjson-c5 - 0.16-3
libjson-script20230523 - 2023-05-23-75a3b870-1
liblua5.1.5 - 5.1.5-11
liblucihttp-lua - 2023-03-15-9b5b683f-1
liblucihttp-ucode - 2023-03-15-9b5b683f-1
liblucihttp0 - 2023-03-15-9b5b683f-1
liblzo2 - 2.10-4
libmbedtls12 - 2.28.9-1
libmnl0 - 1.0.5-1
libncurses6 - 6.4-2
libnetfilter-conntrack3 - 1.0.9-2
libnettle8 - 3.9.1-1
libnfnetlink0 - 1.0.2-1
libnftnl11 - 1.2.6-1
libnghttp2-14 - 1.57.0-1
libnl-tiny1 - 2023-07-27-bc92a280-1
libopenssl3 - 3.0.15-1
libpcre2 - 10.42-1
libpthread - 1.2.4-4
librt - 1.2.4-4
libsmartcols1 - 2.39-2
libss2 - 1.47.0-2
libubox20230523 - 2023-05-23-75a3b870-1
libubus-lua - 2023-06-05-f787c97b-1
libubus20230605 - 2023-06-05-f787c97b-1
libuci20130104 - 2023-08-10-5781664d-1
libuclient20201210 - 2023-04-13-007d9454-1
libucode20230711 - 2024-07-11-1a8a0bcf-3
libustream-mbedtls20201210 - 2023-02-25-498f6e26-1
libuuid1 - 2.39-2
logd - 2022-08-13-4c7b720b-2
lua - 5.1.5-11
luci - git-24.322.79771-ee4c08d
luci-app-attendedsysupgrade - git-24.322.79771-ee4c08d
luci-app-firewall - git-24.322.79771-ee4c08d
luci-app-https-dns-proxy - 2023.12.26-1
luci-app-openvpn - git-24.322.79771-ee4c08d
luci-app-opkg - git-24.322.79771-ee4c08d
luci-app-pbr - 1.1.7-59
luci-base - git-24.322.79771-ee4c08d
luci-compat - git-24.322.79771-ee4c08d
luci-lib-base - git-24.322.79771-ee4c08d
luci-lib-ip - git-24.322.79771-ee4c08d
luci-lib-jsonc - git-24.322.79771-ee4c08d
luci-lib-nixio - git-24.322.79771-ee4c08d
luci-light - git-24.322.79771-ee4c08d
luci-lua-runtime - git-24.322.79771-ee4c08d
luci-mod-admin-full - git-24.322.79771-ee4c08d
luci-mod-network - git-24.322.79771-ee4c08d
luci-mod-status - git-24.322.79771-ee4c08d
luci-mod-system - git-24.322.79771-ee4c08d
luci-proto-ipv6 - git-24.322.79771-ee4c08d
luci-proto-ppp - git-24.322.79771-ee4c08d
luci-ssl - git-24.322.79771-ee4c08d
luci-theme-bootstrap - git-24.322.79771-ee4c08d
mkf2fs - 1.16.0-1
mtd - 26
nano-full - 8.2-1
netifd - 2024-01-04-c18cc79d-2
nftables-json - 1.0.8-1
odhcp6c - 2023-05-12-bcd28363-20
odhcpd-ipv6only - 2023-10-24-d8118f6e-1
openvpn-openssl - 2.5.8-5
openwrt-keyring - 2022-03-25-62471e69-2
opkg - 2022-02-24-d038e5b6-2
partx-utils - 2.39-2
pbr - 1.1.7-59
ppp - 2.4.9.git-2021-01-04-4
ppp-mod-pppoe - 2.4.9.git-2021-01-04-4
procd - 2023-06-25-2db83655-2
procd-seccomp - 2023-06-25-2db83655-2
procd-ujail - 2023-06-25-2db83655-2
px5g-mbedtls - 10
r8169-firmware - 20230804-1
resolveip - 2
rpcd - 2023-07-01-c07ab2f9-1
rpcd-mod-file - 2023-07-01-c07ab2f9-1
rpcd-mod-iwinfo - 2023-07-01-c07ab2f9-1
rpcd-mod-luci - 20240305-1
rpcd-mod-rpcsys - 2023-07-01-c07ab2f9-1
rpcd-mod-rrdns - 20170710
rpcd-mod-ucode - 2023-07-01-c07ab2f9-1
terminfo - 6.4-2
ubox - 2022-08-13-4c7b720b-2
ubus - 2023-06-05-f787c97b-1
ubusd - 2023-06-05-f787c97b-1
uci - 2023-08-10-5781664d-1
uclient-fetch - 2023-04-13-007d9454-1
ucode - 2024-07-11-1a8a0bcf-3
ucode-mod-fs - 2024-07-11-1a8a0bcf-3
ucode-mod-html - 1
ucode-mod-lua - 1
ucode-mod-math - 2024-07-11-1a8a0bcf-3
ucode-mod-nl80211 - 2024-07-11-1a8a0bcf-3
ucode-mod-rtnl - 2024-07-11-1a8a0bcf-3
ucode-mod-ubus - 2024-07-11-1a8a0bcf-3
ucode-mod-uci - 2024-07-11-1a8a0bcf-3
ucode-mod-uloop - 2024-07-11-1a8a0bcf-3
uhttpd - 2023-06-25-34a8a74d-2
uhttpd-mod-ubus - 2023-06-25-34a8a74d-2
urandom-seed - 3
urngd - 2023-11-01-44365eb1-1
usign - 2020-05-23-f1f65026-1
wget-ssl - 1.21.4-1
wireless-regdb - 2024.10.07-1
wpad-mini - 2023-09-08-e5ccbfc6-8
zlib - 1.2.13-1
root@OpenWrt:~#