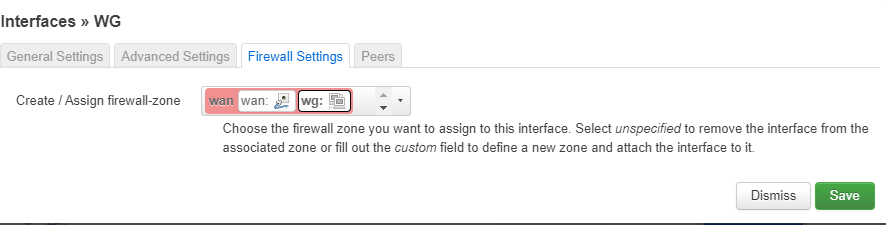
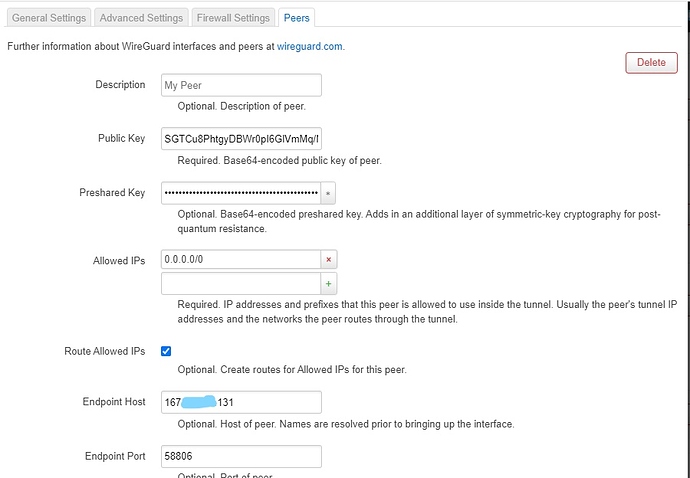
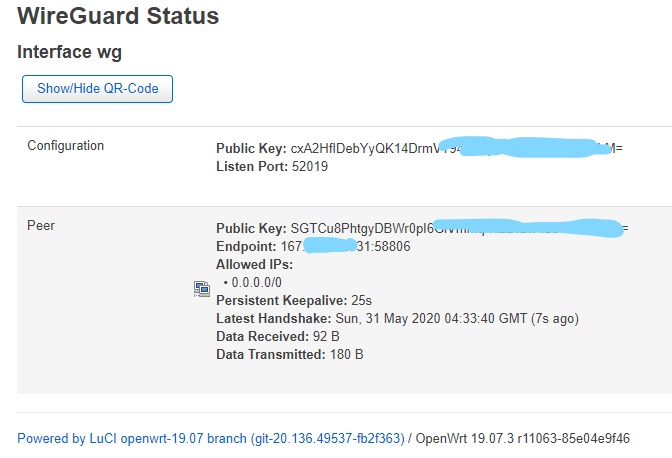
I want to use wireguard client on my x86 openwrt [LuCI openwrt-19.07 branch (git-20.136.49537-fb2f363) / OpenWrt 19.07.3 r11063-85e04e9f46].
.
I have finish configure the wireguard connection on the openwrt, which shows the handshake success. The picture shows the handshake success.
Then I start configure the firewall setting. What I have done is assign Lan zone for the WG interface. I did not make any change in firewall section.
However, this kind of firewall setting not works.
I can connect the internet through my real IP address, instead of wireguard's IP address. The wireguard settings should be right, since the wireguard setting works well in my phone app and windows software.
Even though I have try many kind of methods from Internet about the firewall setting, I could not make it works. I also put the /etc/config/network and /etc/config/firewall in the below.
I thought there are some problems about my firewall settings. Can you help me figure it out?
Really appreciate it! 
network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd9f:166d:f613::/48'
config interface 'lan'
option ifname 'eth0'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option ip6assign '60'
option type 'bridge'
config interface 'wan'
option proto 'dhcp'
option ifname 'eth1'
config interface 'wg'
option proto 'wireguard'
list addresses '10.66.66.3/24'
option private_key 'kCmDYVcgFM6L+RyKB3666dGLoQA4tGLAo39bAGb6666=' #fake
config wireguard_wg
option public_key 'SGTCu8PhtgyDBWr0pI6GlV666/NEDIBw4btXGra6666=' #fake
option endpoint_port '58806'
list allowed_ips '0.0.0.0/0'
option preshared_key '7NlhDyJ065tHxXLUDGjLuP8wLZ4VRtRUjlFG/BO6666=' #fake
option endpoint_host '167.999.226.131' #fake
option persistent_keepalive '25'
firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan wg'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '58806'
option name 'Allow-Wireguard-Inbound'
config rule
option src '*'
option target 'ACCEPT'
option proto 'udp'
option dest_port '58806'
option name 'Allow-Wireguard-Inbound'
config forwarding
option dest 'wan'
option src 'lan'