lol123
February 2, 2024, 1:41am
1
Hello, i want to create a OpenWRT Wireguard Client can somebody help to create it?
Thank you for helping me
there are only a few fields to worry about:
in the interface section, you need the private key (for your side) the address.
In the peer section, you need the server's public key, endpoint host and endpoint port, and allowed IPs. Sometimes also a preshared key.
You theoretically have all of that information already -- where did the conf file come from?
lol123
February 2, 2024, 2:56am
3
Jeah but always when i create wg0, it wants the public key but every tut even in youtube they dont got this extra
What fields are in the conf file that you got from the VPN server side?
lol123
February 2, 2024, 3:18am
5
[Interface]
[Peer]
Private, Public and Preshared are all diff
Enter those things into the respective fields in OpenWrt.
create a new interface with protocol wireguard. Then you'll see the fileds.
Or, you could do this with UCI commands or editing the config files directly.
lol123
February 2, 2024, 3:28am
9
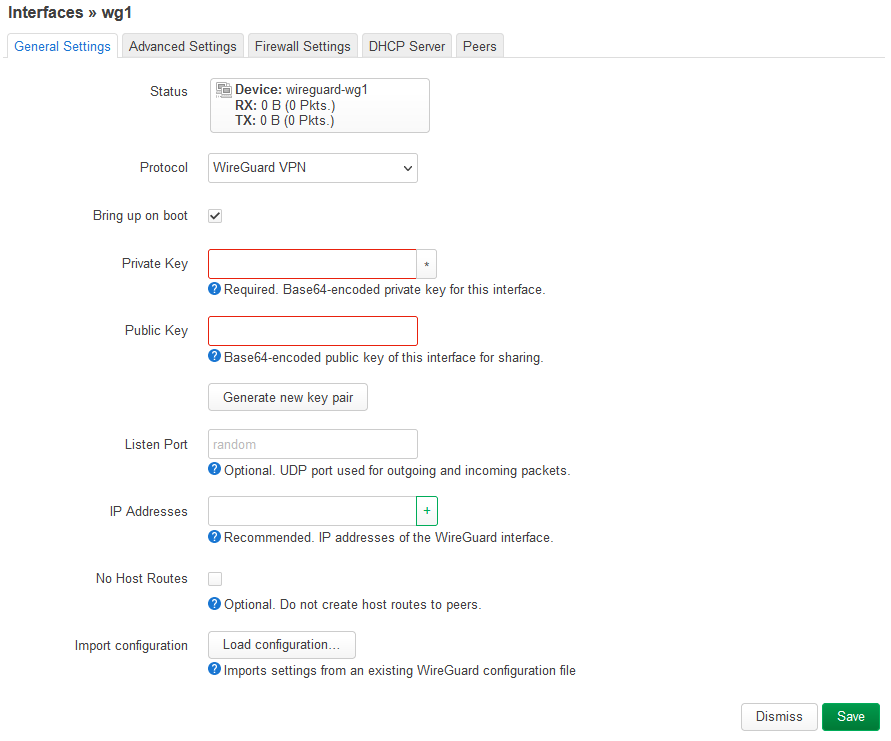
When i do this have my Problem look :
ztx6d
February 2, 2024, 3:29am
10
You can use the luci to configure wireguard,it is fast and easy.
put the private key into the private key field... put the IP address into the IP address field... an so on.
When you get to the peer section, click on Peers then add a peer and enter the respective information there.
Or.... click that load configuration button.
lol123
February 2, 2024, 3:36am
13
imported the config file .. Doenst work ..., the config works on my mobile phone ...
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
ubus call system board
cat /etc/config/network
cat /etc/config/firewall
lol123
February 2, 2024, 3:52am
15
It's about wg1 should be Client,wg0 is Server and it worked
root@OpenWrt:~# ubus call system board
{
"kernel": "5.15.134",
"hostname": "OpenWrt",
"system": "AR9 rev 1.2",
"model": "AVM FRITZ!Box 7320",
"board_name": "avm,fritz7320",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.0",
"revision": "r23497-6637af95aa",
"target": "lantiq/xway",
"description": "OpenWrt 23.05.0 r23497-6637af95aa"
}
}
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdd1:14ac:73a0::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'b'
option firmware '/lib/firmware/adsl.bin'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'dsl0'
option macaddr 'c0:25:06:8a:3d:b7'
config interface 'wan'
option device 'br-lan'
option proto 'dhcp'
config interface 'bridge'
option proto 'relay'
option ipaddr '192.168.20.1'
list network 'wan'
list network 'wifi'
config interface 'wifi'
option proto 'static'
option device 'phy0-ap0'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
config interface 'wg0'
option proto 'wireguard'
option private_key '*'
option listen_port '6789'
list addresses '192.168.21.1/24'
config wireguard_wg0
option description 'Client'
option public_key '*'
option private_key '*'
list allowed_ips '192.168.21.28/32'
option route_allowed_ips '1'
config interface 'wg1'
option proto 'wireguard'
option private_key '*'
list addresses '10.66.66.2/32'
list addresses 'fd42:42:42::2/128'
list dns '1.1.1.1'
list dns '1.0.0.1'
config wireguard_wg1
option description 'Imported peer configuration'
option public_key *'
option preshared_key '*'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option endpoint_host '154.53.166.155'
option endpoint_port '1234'
option route_allowed_ips '1'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
list network 'lan'
list network 'wifi'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Wireguard'
option src 'wan'
option src_dport '6789'
option dest_ip '192.168.20.1'
option dest_port '6789'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'WireguardServer'
option src 'wan'
option src_dport '1234'
option dest_port '1234'
option dest_ip '192.168.20.1'
config zone
option name 'VPN'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'wg1'
config forwarding
option src 'lan'
option dest 'VPN'
root@OpenWrt:~#
The config looks fine from a wireguard perspective, but getting it to work on a device running relayd is a bit of a different story.
This might help:
I don't have another wire-guard device unfortunately and i think relayd is my only option. I'm in a share house and my room is far from the Main router. Main cannot mesh and i cant connect via cable.
I have tried the solution in here and it works. WireGuard "server" on Relayd client bridge device [SOLVED]
Now i can connect to wire-guard VPN and also have internet access.
I cant access devices connect to the OpenWrt AP or lan ports. I can only connect to computers connected to the wlan from t…
lol123
February 2, 2024, 4:07am
17
Wow this is so long
I have never done anything with relayd and it is a bit of an outlier in terms of the methods of setting up wireguard, so hopefully that thread (and the linked solution beyond that) is accurate.
Did it work for you?
lol123
February 2, 2024, 4:17am
19
i cant find the solution it should be in there but iam not so good in english ...
it should be here? which postnr? WireGuard "server" on Relayd client bridge device [SOLVED]
As I read through the linked solution, it looks like the answer was simple...
But your config is rather different than most due to the relayd... I'm not sure that it can work in this situation because the devices that connect to your network will all use your main router as the gateway. They don't even know that this device can be used as a gateway (via the VPN), so they'll never select this path. It might be possible to address this with DHCP option 3 on your main DHCP server, or to manually set the IP address information on your devices (static IP) so that you can specify this as the gateway device.
But normally, if you want to use a router as a VPN endpoint through which the traffic all tunnels, it needs to be the gateway for the network (i.e. the main router, not a relayd/repeater).
![]()