Lynx
7
It's fiddly but once set up it's done and you can leave it be for ages.
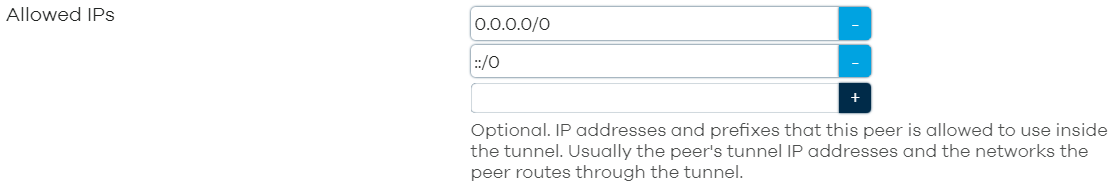
I think I had to add the IPv6 address in allowed IPs here:
Also you may want to consider the simple nftables-based pbr that is configurable through LuCi:
This allows you to configure which addresses go where (either directly out through WAN) or through VPN. And all through the LuCi GUI. Fantastic.