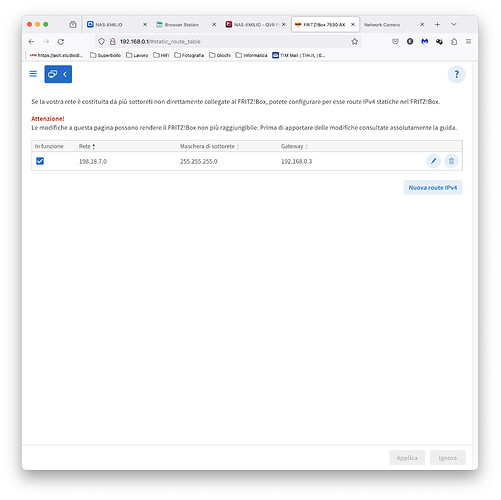
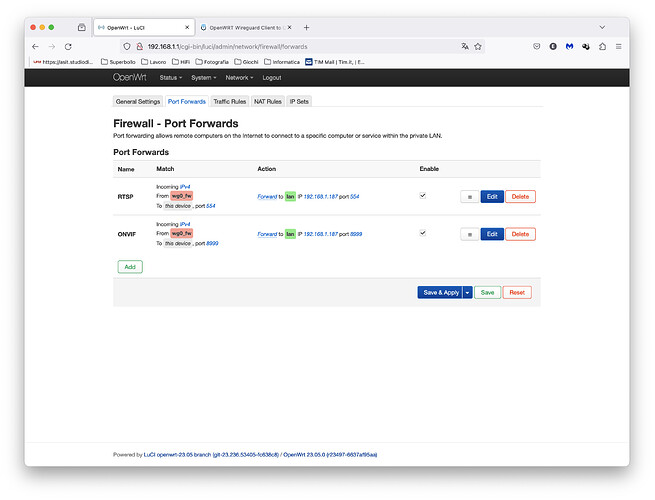
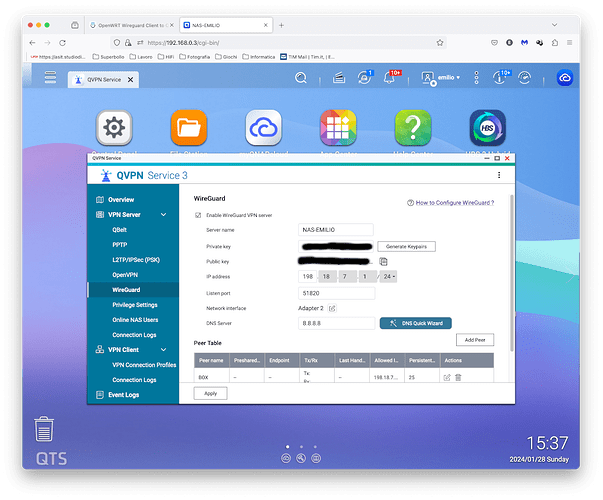
Hello everybody, first post here, although I had a little experience with OpenWRT few years ago on a D-Link router (DGN-3500). I'm familiar with Linux (and similar systems) but I've always been a sucker at more than basic network configurations. ![]()
I'm setting up a TP-Link TR-ML6400 as a Wireguard client to connect to my QNAP NAS at home that hosts (among other things) a security camera recording system. Basically I need the cameras on 6400 lan (wlan) to be "seen" by the NAS via the tunnel.
I've managed to install OpenWRT, set up the cellular modem (thanks to this thread), set up the Wireguard connection between the 6400 (acting as a client) and the NAS (server).
I think I'm missing something in the routing/firewall settings of one or both sides.
Thanks in advance for your help, following are the configuration files and outputs:
ML6400 network conf file:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdea:8cd3:2e4c::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '3 6t'
config interface 'wwan'
option proto 'dhcp'
config interface 'wdm0'
option proto 'qmi'
option device '/dev/cdc-wdm0'
option apn 'internet.wind'
option auth 'none'
option pdptype 'ipv4v6'
option default_profile '1'
config interface 'wg0'
option proto 'wireguard'
option private_key '[...]'
list addresses '198.18.7.2/32'
option mtu '1412'
config wireguard_wg0
option description 'NAS-EMILIO'
option public_key '[...]'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '[...].myqnapcloud.com'
option endpoint_port '51820'
ML6400 firewall conf
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
list network 'wdm0'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'ivpn_fw'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'ivpn_fw'
NAS VPN config:
[Interface]
Address = 198.18.7.1/24
ListenPort = 51820
PrivateKey = [...]
PostUp = iptables -A FORWARD -i %i -j ACCEPT;
PostDown = iptables -D FORWARD -i %i -j ACCEPT;
SaveConfig = true
[Peer]
PublicKey = [...]
AllowedIPs = 198.18.7.2/32
PersistentKeepalive = 10
NAS iptables -L output:
[~] # iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
QUFIREWALL all -- anywhere anywhere state NEW
Chain FORWARD (policy ACCEPT)
target prot opt source destination
DOCKER-USER all -- anywhere anywhere
DOCKER-ISOLATION-STAGE-1 all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
DOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
SYSDOCKER-USER all -- anywhere anywhere
SYSDOCKER-ISOLATION-STAGE-1 all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
SYSDOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
SYSDOCKER all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
CSFORWARD all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
DROP all -- anywhere anywhere match-set BRNOIPSET src,dst
Chain CSFORWARD (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
DROP all -- anywhere anywhere ctstate INVALID,NEW
DROP all -- anywhere anywhere ctstate INVALID,NEW
DROP all -- anywhere anywhere ctstate INVALID,NEW
DROP all -- anywhere anywhere ctstate INVALID,NEW
Chain DOCKER (1 references)
target prot opt source destination
Chain DOCKER-ISOLATION-STAGE-1 (1 references)
target prot opt source destination
DOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain DOCKER-ISOLATION-STAGE-2 (1 references)
target prot opt source destination
DROP all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain DOCKER-USER (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere
Chain QUFIREWALL (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere -m geoip --source-country IT,TW
ACCEPT all -- 198.18.7.0 anywhere
ACCEPT udp -- anywhere anywhere multiport dports 51820
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere
NFLOG all -- anywhere anywhere match-set PSIRT.ipv4 src nflog-prefix "RULE=12 ACT=DROP"
DROP all -- anywhere anywhere match-set PSIRT.ipv4 src
NFLOG all -- anywhere anywhere match-set TOR.ipv4 src nflog-prefix "RULE=13 ACT=DROP"
DROP all -- anywhere anywhere match-set TOR.ipv4 src
ACCEPT all -- 192.168.0.0/24 anywhere
ACCEPT all -- anywhere anywhere -m geoip --source-country IT
NFLOG all -- anywhere anywhere nflog-prefix "RULE=16 ACT=DROP"
DROP all -- anywhere anywhere
[Chain SYSDOCKER (2 references)
target prot opt source destination
ACCEPT tcp -- anywhere 172.30.8.2 tcp dpt:www
Chain SYSDOCKER-ISOLATION-STAGE-1 (1 references)
target prot opt source destination
SYSDOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
SYSDOCKER-ISOLATION-STAGE-2 all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain SYSDOCKER-ISOLATION-STAGE-2 (2 references)
target prot opt source destination
DROP all -- anywhere anywhere
DROP all -- anywhere anywhere
RETURN all -- anywhere anywhere
Chain SYSDOCKER-USER (1 references)
target prot opt source destination
RETURN all -- anywhere anywhere]